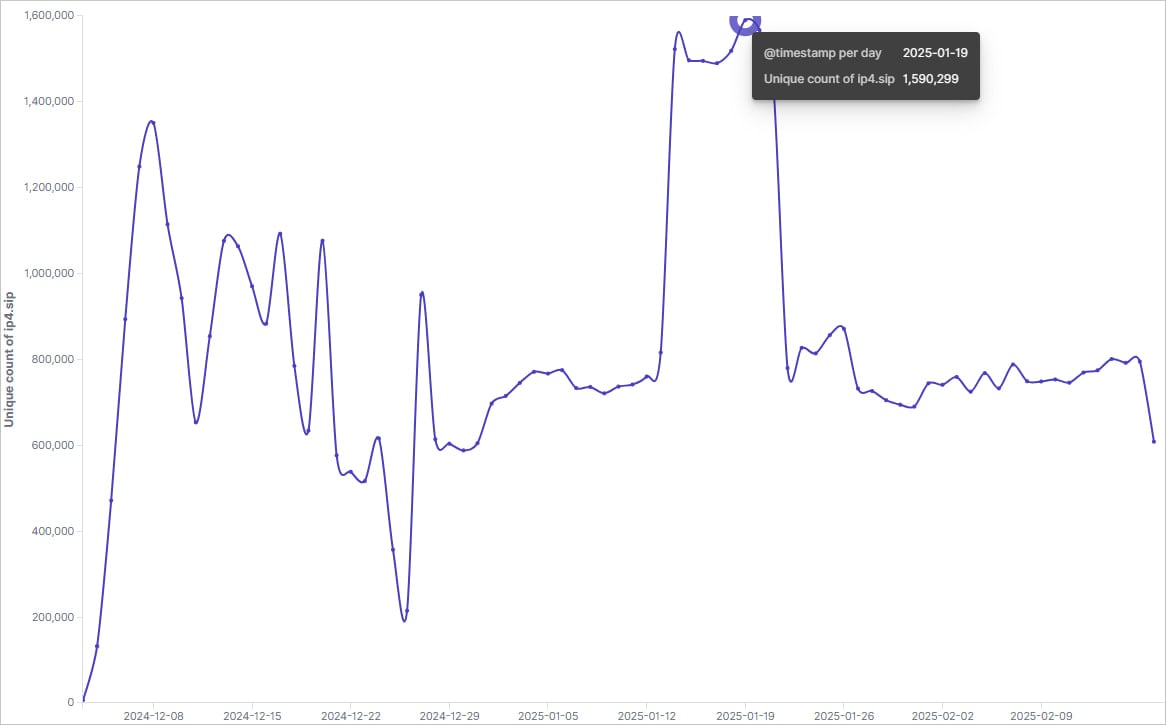
A brand new variant of the Vo1d malware botnet has grown to 1,590,299 contaminated Android TV gadgets throughout 226 international locations, recruiting gadgets as a part of nameless proxy server networks.
That is in response to an investigation by Xlab, which has been monitoring the brand new marketing campaign since final November, reporting that the botnet peaked on January 14, 2025, and presently has 800,000 energetic bots.
In September 2024, Dr. Net antivirus researchers discovered 1.3 million gadgets throughout 200 international locations compromised by Vo1d malware by way of an unknown an infection vector.
XLab’s current report signifies that the brand new model of the Vo1d botnet continues its operations on a bigger scale, not deterred by the earlier publicity.
Furthermore, the researchers underline that the botnet has advanced with superior encryption (RSA + customized XXTEA), resilient DGA-powered infrastructure, and enhanced stealth capabilities.
Supply: XLab
Large botnet measurement
The Vo1d botnet is without doubt one of the largest seen lately, surpassing Bigpanzi, the unique Mirai operation, and the botnet chargeable for a record-breaking 5.6 Tbps DDoS assault dealt with by Cloudflare final 12 months.
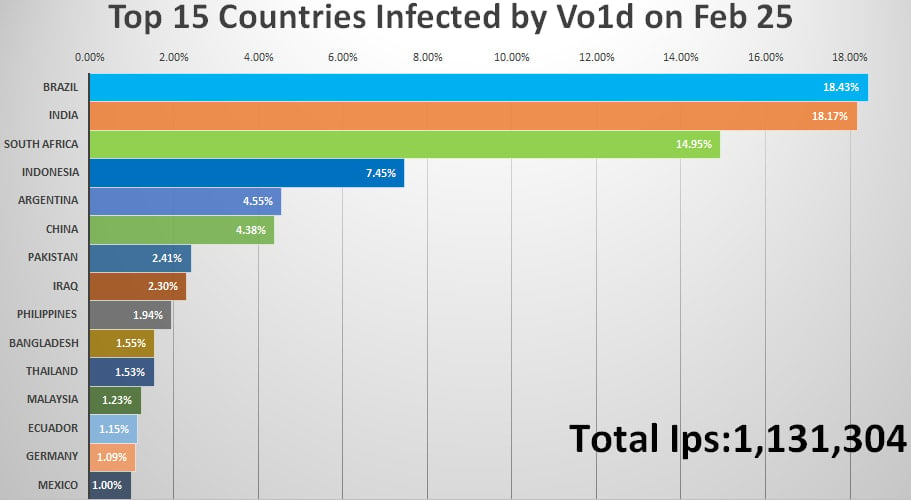
As of February 2025, practically 25% of the infections impression Brazilian customers, adopted by gadgets in South Africa (13.6%), Indonesia (10.5%), Argentina (5.3%), Thailand (3.4%), and China (3.1%).
The researchers report that the botnet has had notable an infection surges, like going from 3,900 to 217,000 bots in India inside simply three days.
The biggest fluctuations recommend that the botnet operators could also be “renting” gadgets as proxy servers, that are generally used to conduct additional criminal activity or botting.
“We speculate that the phenomenon of “speedy surges adopted by sharp declines” could also be attributed to Vo1d leasing its botnet infrastructure in particular areas to different teams. This is how this “rental-return” cycle might work:
Leasing Part:
Initially of a lease, bots are diverted from the principle Vo1d community to serve the lessee’s operations. This diversion causes a sudden drop in Vo1d’s an infection depend because the bots are quickly faraway from its energetic pool.
Return Part:
As soon as the lease interval ends, the bots rejoin the Vo1d community. This reintegration results in a speedy spike in an infection counts because the bots turn into energetic once more underneath Vo1d’s management.
This cyclical mechanism of “leasing and returning” might clarify the noticed fluctuations in Vo1d’s scale at particular time factors.”
❖ Xlab
The size of its command and management (C2) infrastructure can also be spectacular, with the operation utilizing 32 area technology algorithm (DGA) seeds to provide over 21,000 C2 domains.
C2 communication is protected by a 2048-bit RSA key, so even when researchers establish and register a C2 area, they aren’t capable of subject instructions to the bots.
Supply: XLab
Vo1d capabilities
The Vo1d botnet is a multi-purpose cybercrime device that turns compromised gadgets into proxy servers to facilitate unlawful operations.
Contaminated gadgets relay malicious site visitors for the cybercriminals, hiding the origin of their exercise and mixing in with residential community site visitors. This additionally helps the risk actors bypass regional restrictions, safety filtering, and different protections.
One other perform of Vo1d is advert fraud, faking consumer interactions by simulating clicks on advertisements or views on video platforms to generate income for fraudulent advertisers.
The malware has particular plugins that automate advert interactions and simulate human-like searching habits, in addition to the Mzmess SDK, which distributes fraud duties to totally different bots.
On condition that the an infection chain stays unknown, it’s endorsed that Android TV customers observe a holistic safety method to mitigate the Vo1d risk.
Step one is shopping for gadgets from respected distributors and reliable resellers to attenuate the chance of malware being pre-loaded from the manufacturing unit or whereas in transit.
Secondly, it is crucially essential to put in firmware and safety updates that shut gaps that could be leveraged for distant infections.
Thirdly, customers ought to keep away from downloading apps exterior of Google Play or third-party firmware photographs that promise prolonged and “unlocked” performance.
Android TV gadgets ought to have their distant entry options disabled if not wanted, whereas taking them offline when not used can also be an efficient technique.
Finally, IoT gadgets needs to be remoted from beneficial gadgets that maintain delicate knowledge on the community stage.

