The net cybercrime market, Russian Market, has advanced from promoting Distant Desktop Protocol (RDP) entry to turning into one of the vital energetic underground hubs for information-stealing malware logs.
Stolen person credentials are traded every day, and every compromised login represents a possible gateway into company programs.
Risk actors routinely buy credentials to launch credential-based assaults that put companies, governments, and people vulnerable to account compromise and follow-on cyberattacks.
A number of high-profile breaches have been traced again to credentials purchased on marketplaces like Russian Market, demonstrated how a single uncovered password can result in important knowledge loss, monetary injury, and reputational hurt.
At its inception in early 2020, Russian Market specialised in promoting RDP entry and login credentials to compromised computer systems. Risk actors exploited this entry for ransomware deployment, cyberespionage, and to pivot inside goal networks.
From 2020 till January 2024, when RDP gross sales have been discontinued, {the marketplace} commoditized entry to hundreds of servers and workstations.
In 2021, operators shifted focus to stolen bank card knowledge earlier than launching the “Bots” product line later that 12 months.
These “bots” are knowledge logs exfiltrated from compromised machines—usually through information-stealing malware—and embrace harvested cookies, credentials, autofill knowledge, and session tokens.
By the primary half of 2025, over 180,000 infostealer logs have been supplied on the market. Three key distributors—Nu####ez, bl####ow, and Mo####yf—dominated {the marketplace}, accounting for practically 70% of all bot listings.
Sellers make use of a multi-stealer strategy, leveraging malware variants similar to Raccoon, Vidar, Lumma, RedLine, and Stealc. Extra lately, Rhadamanthys and Acreed have gained traction following legislation enforcement disruptions of Lumma Stealer infrastructure.
Anatomy of a Bot Sale
Inside the “Logs” part, consumers can filter listings by geography, working system, infostealer, and vendor.
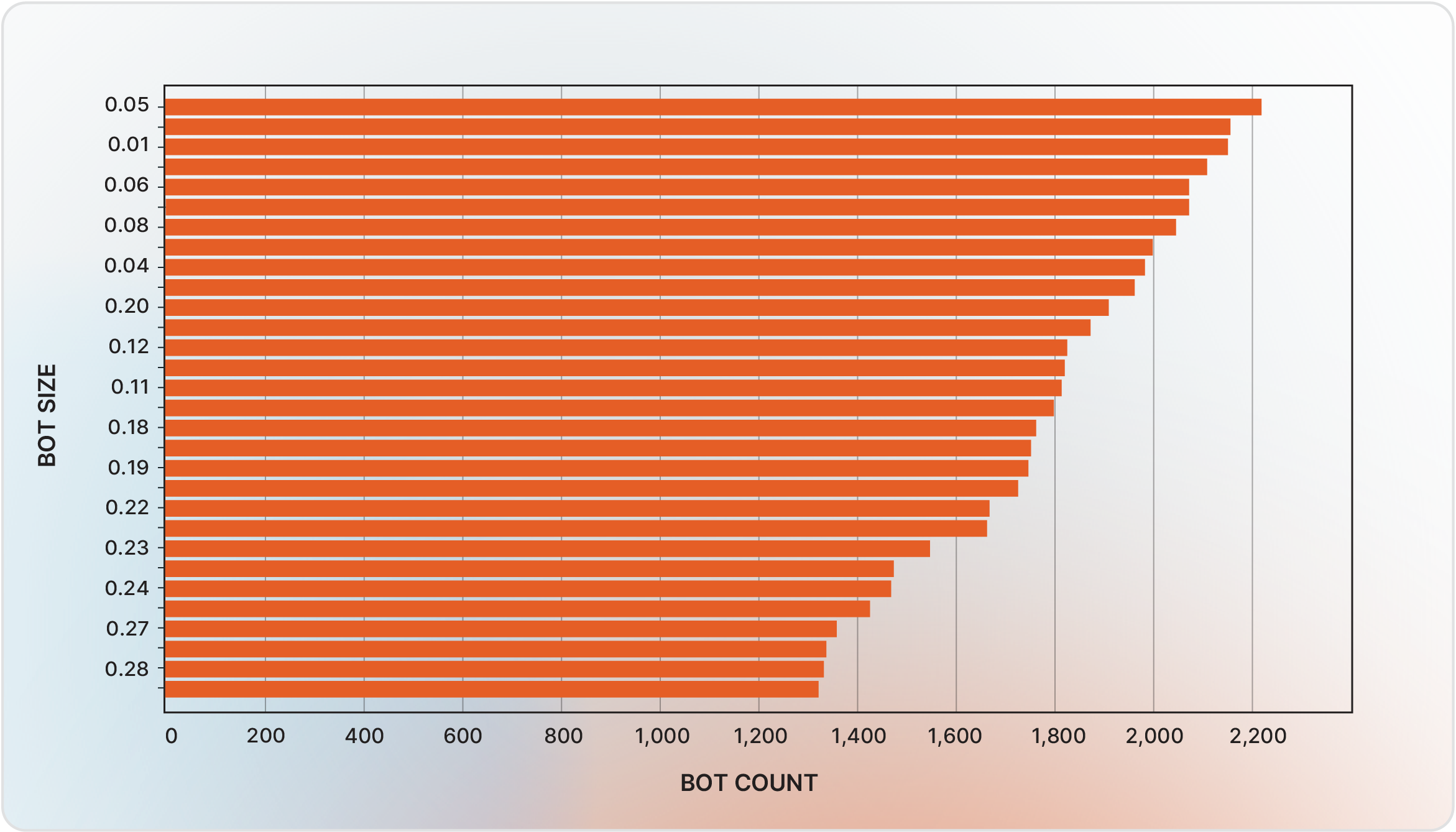
A typical bot comprises credentials for a number of domains; its dimension—starting from 0.05 to 0.3 megabytes—correlates with the variety of harvested logins.
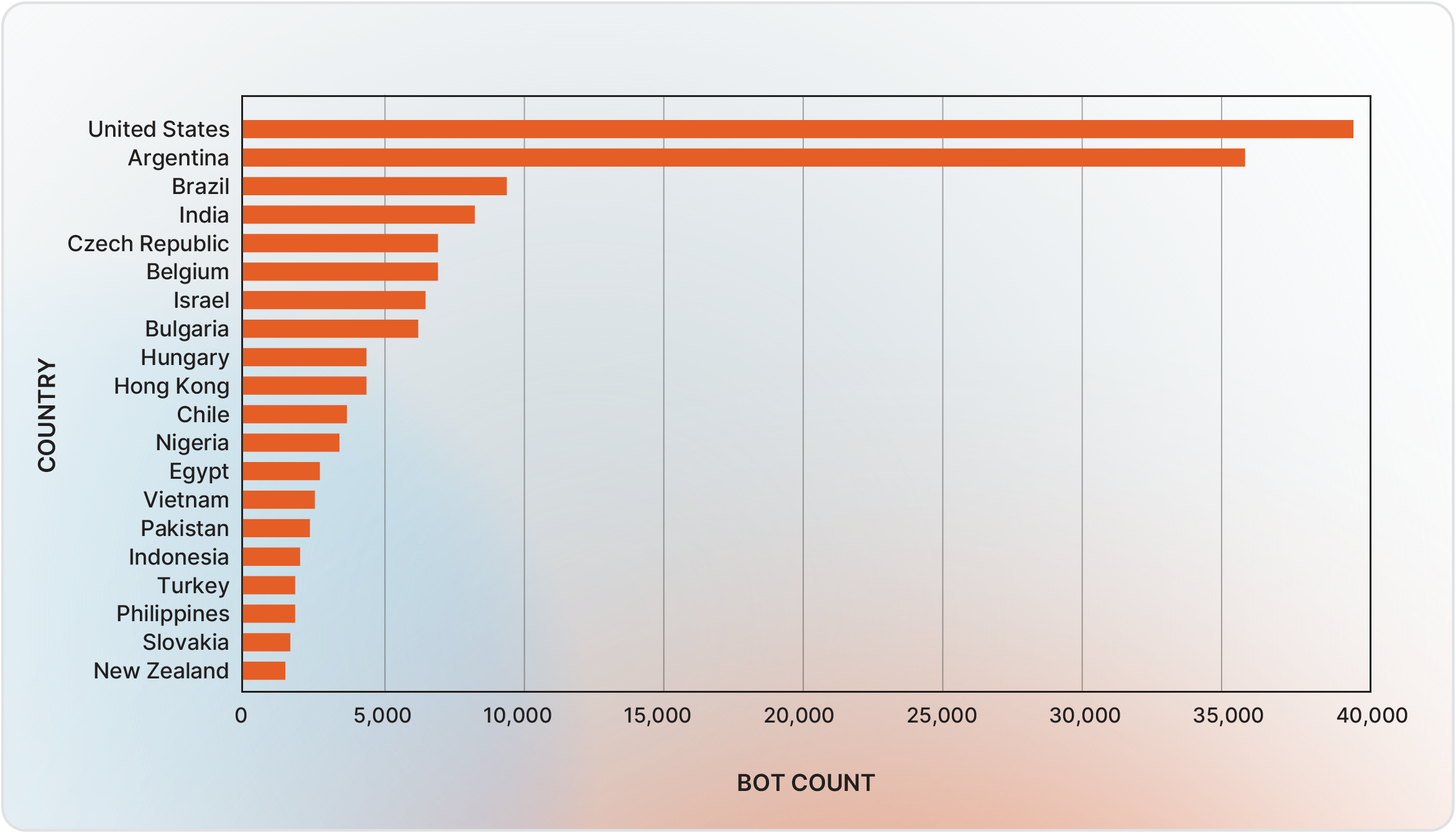

Bots predominantly goal customers in america (26%), Argentina (23%), and Brazil. Within the first half of 2025, common bot dimension was 0.14 megabytes, and costs averaged $10 per bot, with historic ranges from $1 to $100 based mostly on geolocation, session high quality, and credential validity.

Instance SQL-style question utilized by consumers to find enterprise credentials:
sqlSELECT * FROM bots
WHERE area LIKE '%examplecorp.com'
AND infostealer="Lumma"
AND nation = 'US';
Every compromised login could characterize entry to webmail portals, cloud providers, or VPN connections.
These stolen credentials allow menace actors to bypass perimeter defenses and launch email-based phishing or direct ransomware deployments below the guise of professional person exercise.
Profiling Key Distributors
The infostealer ecosystem on Russian Market is anchored by a small variety of prolific distributors. Nu####ez, energetic since January 2024, holds a “Diamond” standing with a 4.41 score and makes use of Lumma, Rhadamanthys, and Acreed in 2025.
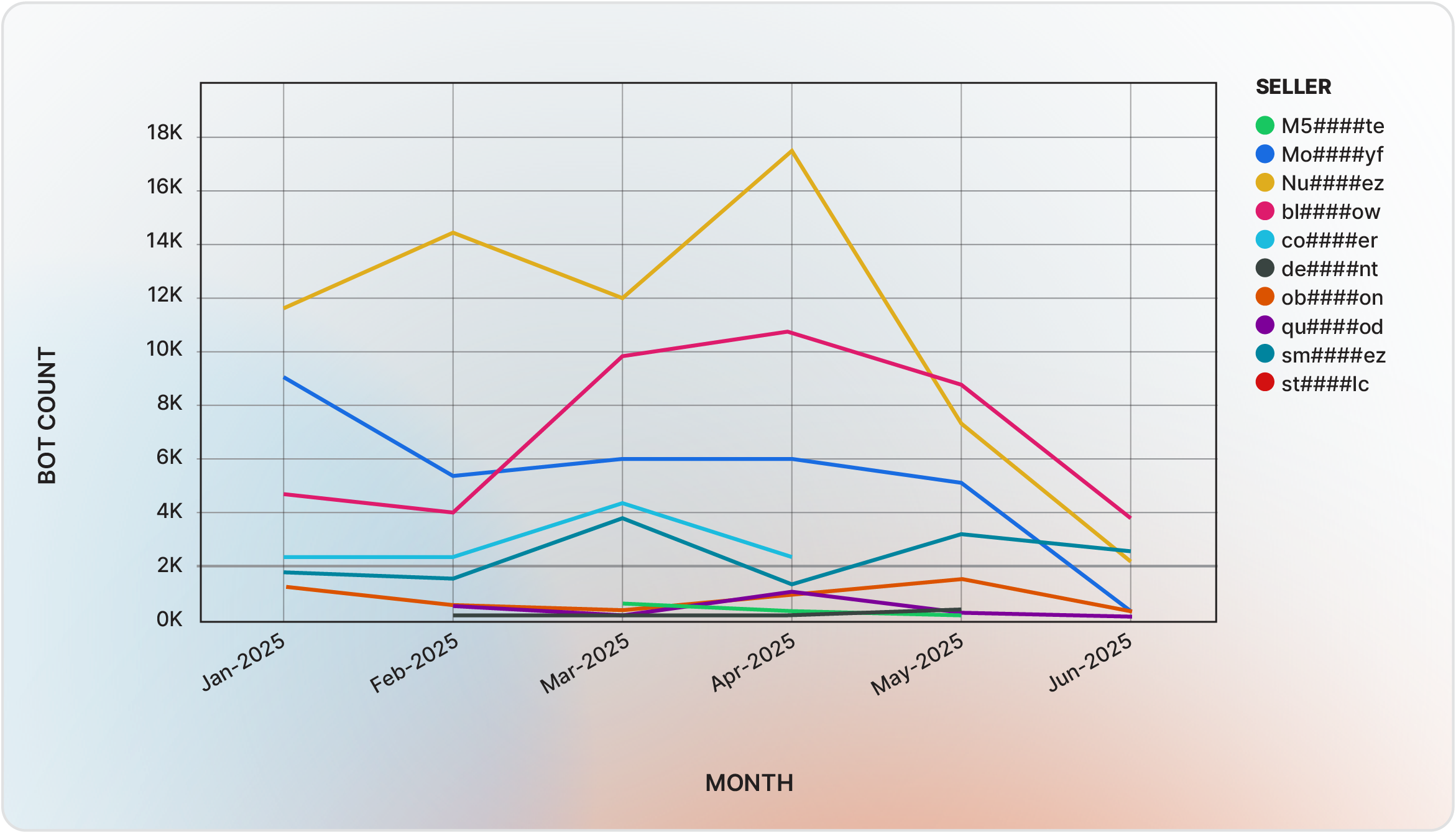

Bl####ow depends completely on Lumma, sustaining a 4.78 score via October 2024. Mo####yf, initially a bank card vendor, shifted to bots and achieved a 4.50 score, leveraging Lumma after utilizing Stealc and Vidar in 2024.
Newer entrants similar to sm####ez and co####er have quickly gained prominence with comparable multi-stealer methods.
Desk 1 – High Distributors by Market Share in H1 2025
| Vendor | Market Share | Main Malware Variants |
|---|---|---|
| Nu####ez | 38% | Lumma, Rhadamanthys, Acreed |
| bl####ow | 24% | Lumma |
| Mo####yf | 19% | Lumma |
| sm####ez | 7% | Lumma, Vidar, Stealc |
| co####er | 4% | Lumma, Stealc |
Info-stealing malware fuels a thriving underground economic system by offering the uncooked materials for credential-based intrusions.
Not like boards similar to BreachForums and XSS which have been disrupted, Russian Market has maintained steady operations, demonstrating its resilience and adaptableness.
Organizations should strengthen defenses by implementing multi-factor authentication, implementing steady credential monitoring, and integrating menace intelligence feeds to detect anomalous login exercise.
Profiling key distributors and infostealer variants supplies a uncommon inside have a look at Russian Market’s operations, underscoring the urgency for companies to behave now to stop publicity of worker credentials and mitigate the chance of devastating follow-on assaults.
Observe us on Google Information, LinkedIn, and X to Get Prompt Updates and Set GBH as a Most well-liked Supply in Google.

