The Black Basta ransomware operation created an automatic brute-forcing framework dubbed ‘BRUTED’ to breach edge networking units like firewalls and VPNs.
The framework has enabled BlackBasta to streamline preliminary community entry and scale ransomware assaults on weak internet-exposed endpoints.
The invention of BRUTED comes from EclecticIQ researcher Arda Büyükkaya following an in-depth examination of the ransomware gang’s leaked inside chat logs.
A number of studies of large-scale brute-forcing and password spray assaults towards these units all through 2024, a few of which could be linked to BRUTED or similar-origin operations.
Automating brute-forcing
Büyükkaya says Black Basta has been utilizing the automated BRUTED platform since 2023 to conduct large-scale credential-stuffing and brute-force assaults on edge community units.
Evaluation of the supply code signifies that the framework was particularly designed to brute-force credentials on the next VPN and remote-access merchandise: SonicWall NetExtender, Palo Alto GlobalProtect, Cisco AnyConnect, Fortinet SSL VPN, Citrix NetScaler (Citrix Gateway), Microsoft RDWeb (Distant Desktop Internet Entry), and WatchGuard SSL VPN.
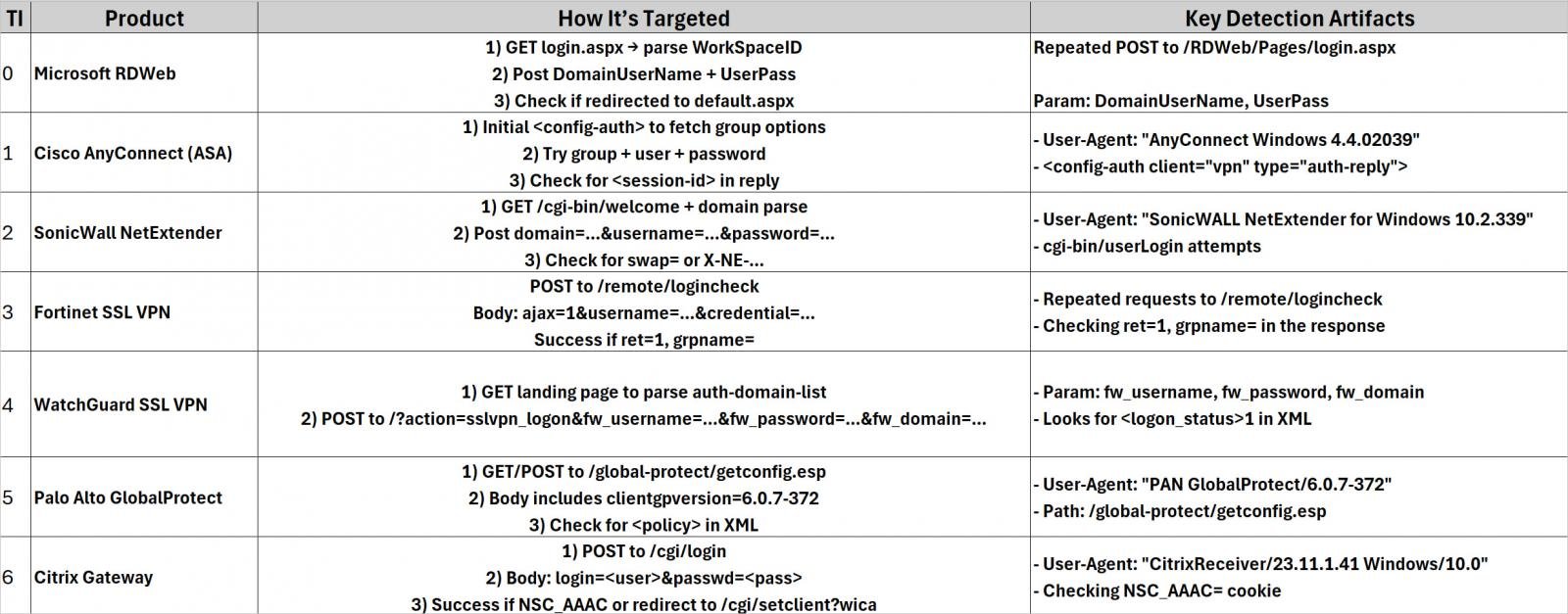
Supply: EclecticIQ
The framework searches for publicly accessible edge networking units matching the targets listing by enumerating subdomains, resolving IP addresses, and appending prefixes like ‘.vpn’ or ‘distant.’ Matches are reported again to the command-and-control (C2) server.
As soon as potential targets are recognized, BRUTED retrieves password candidates from a distant server and combines them with regionally generated guesses to execute many authentication requests through a number of CPU processes.
Büyükkaya shared the supply code with BleepingComputer, which reveals how the software makes use of particular request headers and person brokers for every focused machine within the brute drive assaults.
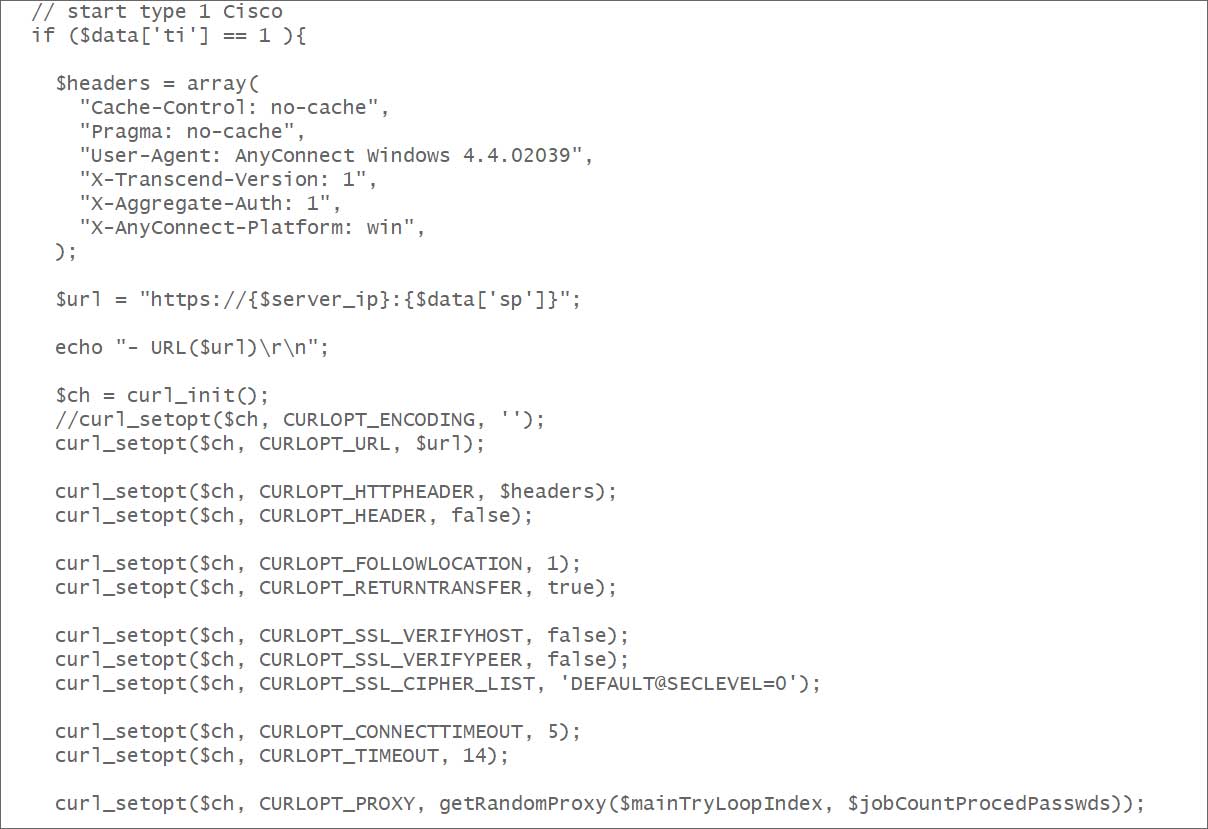
Supply: BleepingComputer
The EclecticIQ report says BRUTED can extract Frequent Identify (CN) and Topic Different Names (SAN) from the SSL certificates of focused units, which helps generate further password guesses based mostly on the goal’s area and naming conventions.
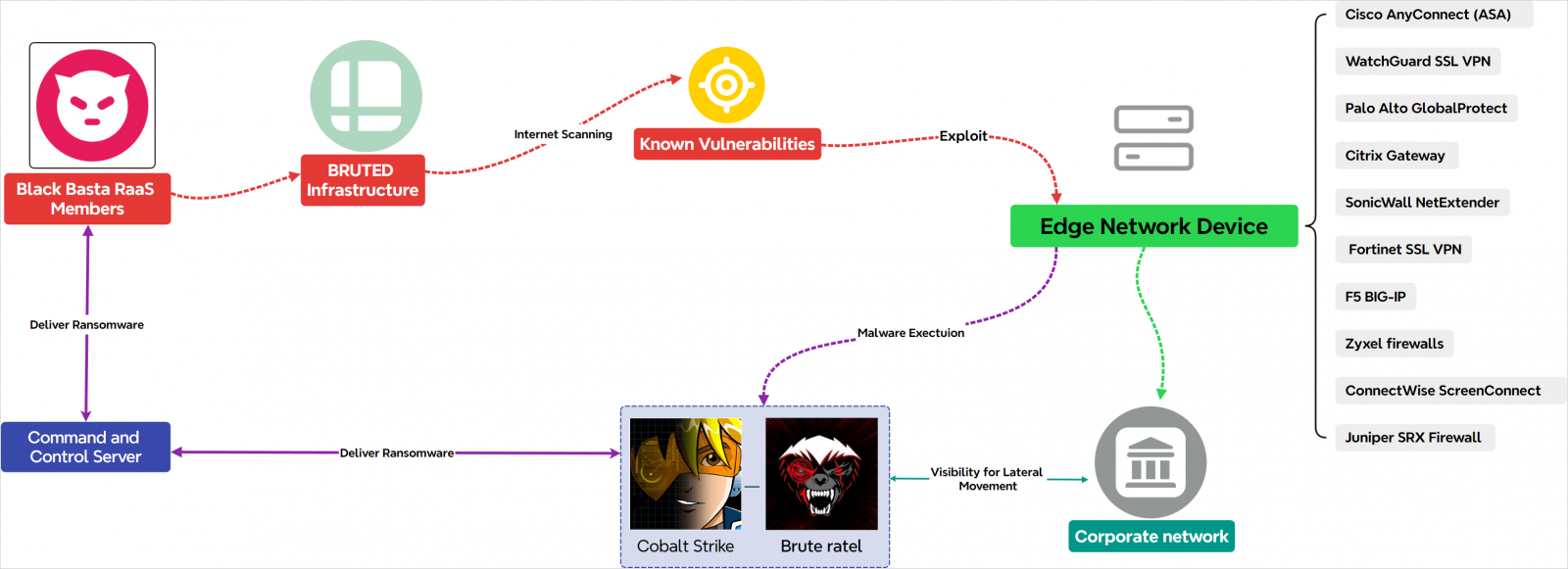
Supply: EclecticIQ
To evade detection, the framework makes use of an inventory of SOCKS5 proxies with an fascinating area title that hides the attacker’s infrastructure behind an intermediate layer.
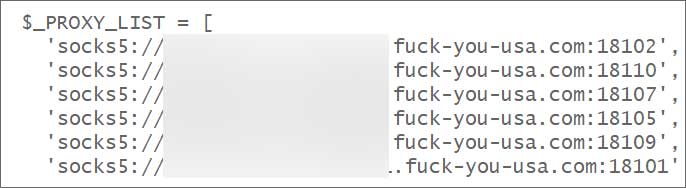
Supply: BleepingCoputer
Its foremost infrastructure includes a number of servers in Russia and is registered underneath Proton66 (AS 198953).
Leaked chat logs additionally revealed inside discussions about server downtime because of unpaid charges, which have been later renewed, giving us a glimpse of the day-to-day operations ransomware gangs must take care of.
Defending towards brute-forcing
Instruments like BRUTED streamline ransomware operations by breaching many networks directly with minimal effort, growing the monetization alternatives for menace actors.
A key protection technique is to implement sturdy, distinctive passwords for all edge units and VPN accounts and use multi-factor authentication (MFA) to dam entry even when credentials are compromised.
Additionally it is essential to observe for authentication makes an attempt from unknown areas and high-volume login failures and implement rate-limiting and account lockout insurance policies.
ElecticIQ has shared an inventory of IPs and domains utilized by BRUTED that can be utilized to create new firewall guidelines that block requests from recognized malicious infrastructure.
Whereas BRUTED doesn’t exploit any vulnerabilities to breach community edge units, it’s nonetheless essential to maintain these units up-to-date by making use of the newest safety updates.


