ESET researchers present insights into how PlushDaemon performs adversary-in-the-middle assaults utilizing a beforehand undocumented community implant that we’ve named EdgeStepper, which redirects all DNS queries to an exterior, malicious hijacking node, successfully rerouting the visitors from authentic infrastructure used for software program updates to attacker-controlled infrastructure.
Key factors on this blogpost:
- We analyzed the community implant EdgeStepper to know how PlushDaemon attackers compromise their targets.
- We offer an evaluation of LittleDaemon and DaemonicLogistics, two downloaders that deploy the group’s signature SlowStepper backdoor on Home windows machines.
PlushDaemon profile
PlushDaemon is a China-aligned menace actor energetic since at the very least 2018 that engages in espionage operations towards people and entities in China, Taiwan, Hong Kong, Cambodia, South Korea, the USA, and New Zealand. PlushDaemon makes use of a customized backdoor that we observe as SlowStepper, and its major preliminary entry method is to hijack authentic updates by redirecting visitors to attacker-controlled servers via a community implant that we name EdgeStepper. Moreover, we’ve noticed the group gaining entry by way of vulnerabilities in net servers, and in 2023 it carried out a supply-chain assault.
Overview
In 2024, whereas researching PlushDaemon’s clusters of exercise (together with the supply-chain compromise of a South Korean VPN service), we observed that an ELF file submitted to VirusTotal contained two subdomains from PlushDaemon’s infrastructure. That file, referred to as bioset, was beforehand hosted on a server possible compromised by a number of menace actors. Observe that on the identical day of the submission to VirusTotal, a researcher (@James_inthe_box) tweeted about an open listing on the server the place bioset was hosted, so the pattern was most likely uploaded to VirusTotal by a researcher who was investigating the contents of the listing.
Internally named dns_cheat_v2 by its builders – and codenamed EdgeStepper by us – bioset is PlushDaemon’s adversary-in-the-middle software, which forwards DNS visitors from machines in a focused community to a malicious DNS node. This permits the attackers to redirect the visitors from software program updates to a hijacking node that serves directions to the authentic software program to obtain a malicious replace.
Victimology
Determine 1 presents the geographical distribution of victims of PlushDaemon which have been compromised via malicious updates, since 2019, in line with ESET telemetry.
PlushDaemon has compromised people and organizations situated within the following areas:
- United States (2019)
- Taiwan (2021, 2024)
- China (2021–2024), together with a college in Beijing and a Taiwanese firm that manufactures electronics
- Hong Kong (2023)
- New Zealand (2023)
- Cambodia (2025), together with an organization within the automotive sector and a department of a Japanese firm within the manufacturing sector
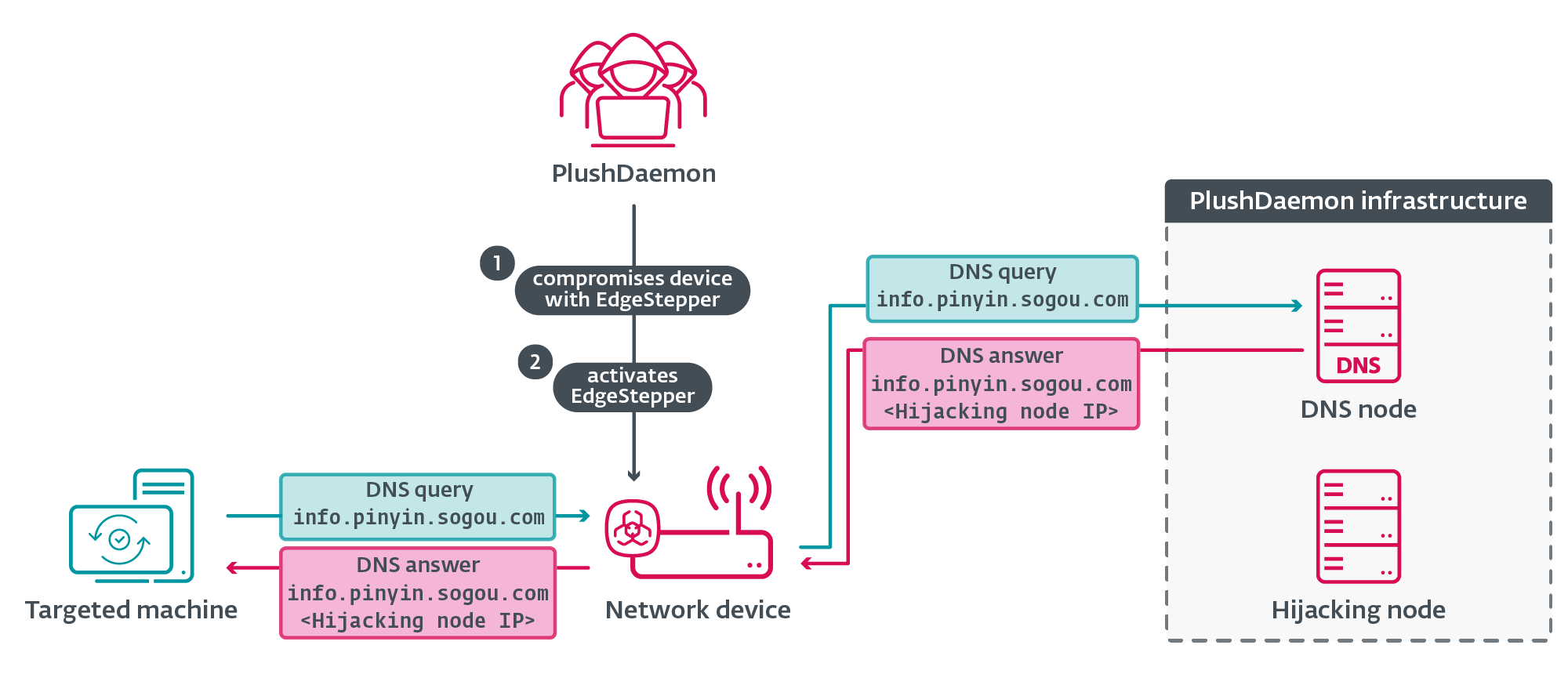
Adversary-in-the-middle assault overview
First, PlushDaemon compromises a community machine (for instance, a router) to which their goal may join; the compromise might be achieved by exploiting a vulnerability within the software program working on the machine or via weak and/or well-known default administrative credentials, enabling the attackers to deploy EdgeStepper (and presumably different instruments).
EdgeStepper begins redirecting DNS queries to a malicious DNS node that verifies whether or not the area (for instance, data.pinyin.sogou.com from Sogou Pinyin) within the DNS question message is said to software program updates, and in that case, it replies with the IP handle of the hijacking node. Alternatively, we’ve additionally noticed that some servers are each the DNS node and the hijacking node; in these instances, the DNS node replies to DNS queries with its personal IP handle.
Observe that since we’ve carefully studied updates for Sogou Pinyin software program being hijacked, we are going to proceed to make use of that for instance from right here on out. Many different fashionable Chinese language software program titles even have their updates hijacked in related methods by PlushDaemon by way of EdgeStepper.
Determine 2 illustrates the primary levels of the deployment of PlushDaemon’s capabilities.
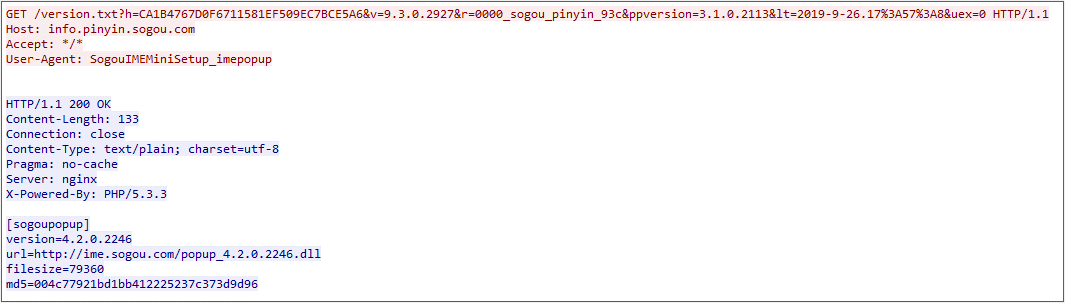
The updating software program communicates by way of HTTP with the hijacking node as an alternative of Sogou’s authentic infrastructure; the hijacking node replies with directions to, for instance, obtain a DLL file from http://ime.sogou.com/popup_4.2.0.2246.dll, as proven in Determine 3.
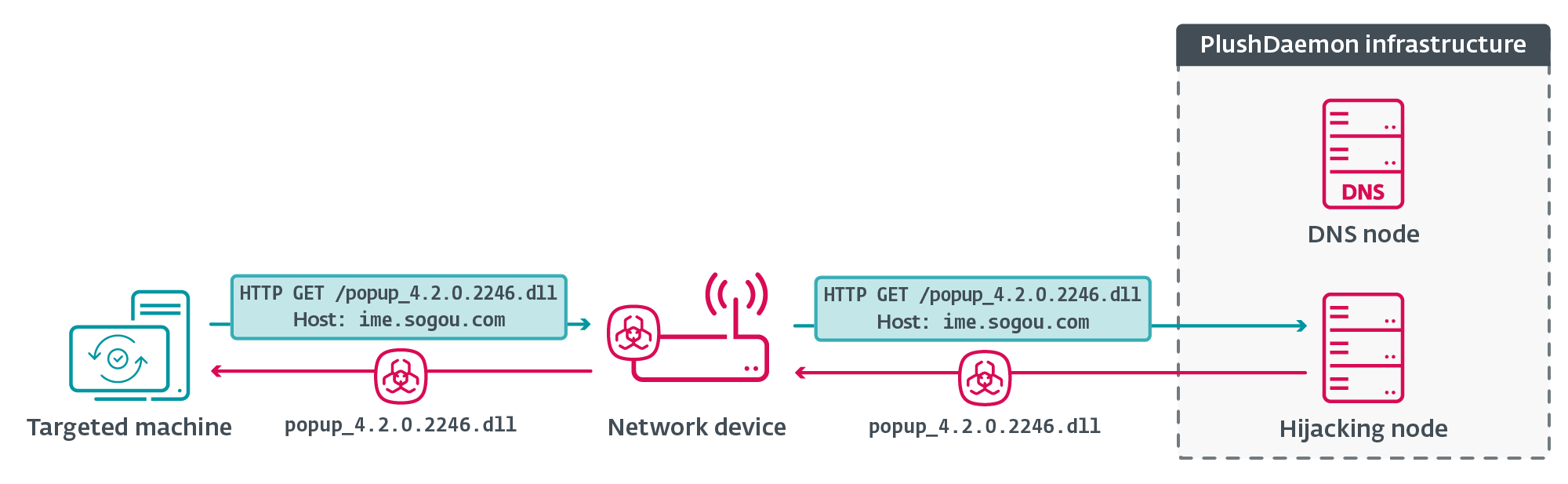
The software program sends an HTTP GET request to ime.sogou.com to attempt to get hold of the DLL; nevertheless, the communication is once more redirected to the hijacking node, which serves popup_4.2.0.2246.dll that, in actuality, is the LittleDaemon DLL. The method is illustrated in Determine 4.
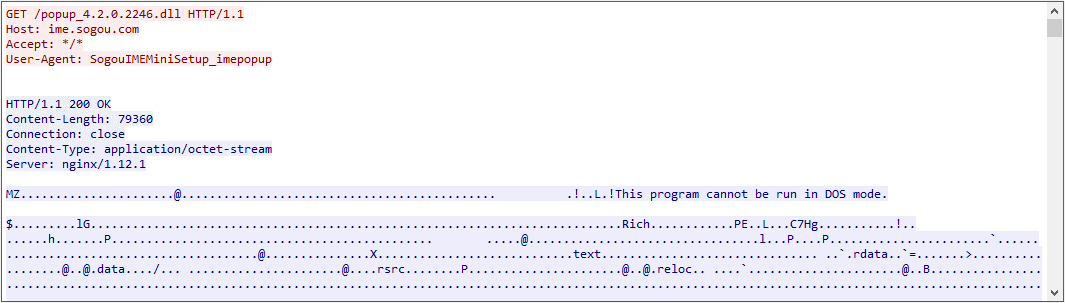
Determine 5 exhibits the hijacking node serving LittleDaemon.
EdgeStepper
In keeping with the symbols within the binary, EdgeStepper was initially referred to as dns_cheat_v2. It was developed in Go utilizing the open-source GoFrame framework, and compiled as an ELF file for MIPS32 processors. It is very important observe that it’s unlikely that EdgeStepper is the one element deployed on the compromised community machine. Sadly, we don’t have samples of different elements within the compromise chain.
EdgeStepper begins by acquiring and decrypting configuration information from /and many others/bioset.conf. For decryption, it makes use of AES CBC with the important thing and IV being the string I Love Go Body!, which is used because the default IV within the implementation by the GoFrame library.
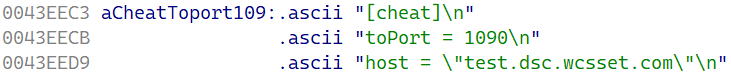
The decrypted configuration reveals the info proven in Determine 6.
[cheat]
toPort = 1090
host = "ds20221202.dsc.wcsset[.]com"Determine 6. Decrypted configuration
The that means of the parameters is as follows:
- toPort specifies the port the place EdgeStepper will pay attention, and
- host specifies the area that’s resolved to acquire the IP handle(es) of the DNS node to which the DNS question packets are forwarded.
Moreover, there’s a configuration block (Determine 7) within the EdgeStepper binary, which seems to not be referenced anyplace within the code. The area within the host subject is check.dsc.wcsset[.]com, which resolved to 47.242.198[.]250. We noticed that IP handle from 2021 to 2022 because the supply of the malicious replace: the hijacking node. On the time of writing, the area resolves to that IP handle.
After loading its configuration, EdgeStepper initializes the Distributor system and the Ruler system.
Distributor
The distributor resolves the IP handle(es) related to the area worth within the host subject of the configuration and invokes the Ruler system. The workflow of the distributor is illustrated in Determine 8.
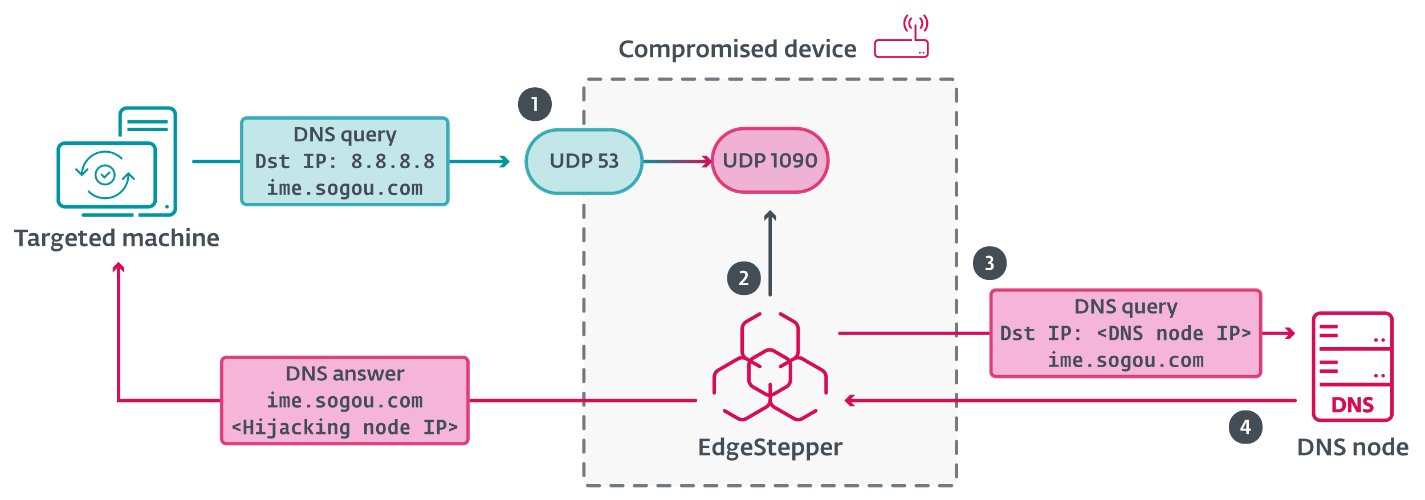
- By way of the Ruler system, the distributor redirects visitors on port 53 to port 1090, establishing itself as a DNS proxy.
- When a DNS message is obtained from a possible sufferer’s machine, it checks whether or not the message is RFC compliant (most likely simply to confirm that the packet is absolutely from the DNS protocol).
- Then it forwards the packet to the malicious DNS node.
- Lastly, it forwards the reply from the DNS node to the machine.
Ruler
The Ruler system makes use of the iptables command to problem new guidelines, and to take away them when concluding the assault. First, it points a rule to redirect all UDP visitors on port 53 of the machine to the port specified by toPort within the configuration:
iptables -t nat -I PREROUTING -p udp –dport 53 -j REDIRECT –to-port
Then it points a command to just accept the packets on that port:
iptables -t filter -I INPUT -p udp –dport
When terminating, it removes the earlier guidelines it arrange by issuing the instructions:
iptables -t nat -D PREROUTING *
iptables -t filter -D INPUT -p udp –dport
LittleDaemon
LittleDaemon is the primary stage deployed on the sufferer’s machine via hijacked updates. We now have noticed each DLL and executable variations, each of them 32-bit PEs. The principle goal of LittleDaemon is to speak with the hijacking node to acquire the downloader that we name DaemonicLogistics. LittleDaemon doesn’t set up persistence.
First, it verifies whether or not the SlowStepper backdoor is working on the system. If not, LittleDaemon downloads DaemonicLogistics by issuing an HTTP GET request to a server (usually, the hijacking node), decrypts it with a mix of XOR operations, after which executes it.
The request will be despatched to 2 authentic domains (ime.sogou.com or mobads.baidu.com) or the IP handle 119.136.153.0. The useful resource path is /replace/updateInfo.bzp for all three. Within the case of the authentic domains, it’s anticipated that the visitors might be redirected to the hijacking node by EdgeStepper.
DaemonicLogistics
DaemonicLogistics is position-independent code downloaded and executed in reminiscence by LittleDaemon. Its major goal is to obtain and deploy the SlowStepper implant.
When DaemonicLogistics sends a request to the server (usually, the hijacking node), it replies with an HTTP standing code, which DaemonicLogistics interprets as a command, and performs the actions listed in Desk 1.
Desk 1. Instructions supported by DaemonicLogistics
| Code | Motion taken |
| 200 | Downloads SlowStepper with out checking for the presence of a course of named 360tray.exe (a element of the 360 Complete Safety antimalware answer). |
| 205 | |
| 206 | |
| 208 | |
| 203 | Downloads a file named plugin.exe and executes it (throughout our checks, the server didn’t request downloading this file). |
| 207 | Checks for the presence of a course of named 360tray.exe and downloads SlowStepper if not current. |
| 202–300 | Default to execute command 200. These could possibly be unimplemented instructions. |
The preliminary HTTP GET request is distributed to:
ime.sogou.com/replace/newest/new_version?tp=2&c=0&s=
The that means of the parameters within the URL are as follows:
- The values tp and c are hardcoded by default to 2 and 0, respectively.
- The s subject is one byte and is a quantity that identifies the working system model.
- The mac subject is six bytes and is the MAC handle worth from the machine’s ethernet or Wi-Fi adapter, or randomly generated if it fails to acquire any; the worth might be used as an identifier by the server.
Throughout our evaluation we noticed that the server replied with standing code 207, to which DaemonicLogistics replied with one other request to ime.sogou.com/replace/newest/new_version?tp=1&g=15&c=0. On this case, the a part of the URL tp=1&g=15&c=0 is hardcoded.
The server replied with standing code 202. DaemonicLogistics proceeded to do two requests to obtain the SlowStepper payload recordsdata, first to ime.sogou.com/replace/file6.bdat, after which to ime.sogou.com/replace/file2.bdat.
The payload information within the first and second responses from the server started with a magic worth:
- In response to the primary request, the magic worth in hex was 50 4B 03 04 0A 1B 2C 3D (PK34A1B2C3C):
○ DaemonicLogistics actively checks that the primary eight bytes of information obtained from the server match this magic worth. If true, it writes the info to %PROGRAMDATApercentTencentQQUpdateMgrUpdateFileslogo.gif.
- In response to the second request, the magic worth in hex was 47 49 46 38 39 61 10 10 (GIF89a1010)
○ DaemonicLogistics doesn’t examine this magic worth particularly: when the examine for the earlier magic worth doesn’t match, it processes the info and decrypts it utilizing a mix of XOR operations. The information incorporates recordsdata which are written to disk on paths specified within the decrypted information..
Conclusion
We analyzed the EdgeStepper community implant that allows PlushDaemon’s adversary-in-the-middle capabilities to hijack updates from machines in a focused community. We additionally analyzed LittleDaemon and DaemonicLogistics instruments that collectively deploy the SlowStepper implant on Home windows machines. These implants give PlushDaemon the potential to compromise targets anyplace on this planet.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis affords non-public APT intelligence reviews and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete record of indicators of compromise and samples will be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | ESET detection identify | Description |
| 8F569641691ECB3888CD |
bioset | Linux/Agent.AEP | EdgeStepper. |
| 06177810D61A69F34091 |
bioset.conf | Win32/Rozena.BXX | EdgeStepper encrypted configuration. |
| 69974455D8C13C5D57C1 |
popup_4.2.0. |
Win32/Agent.AGXK | LittleDaemon. |
| 2857BC730952682D39F4 |
sogou_wubi_15.4. |
Win32/Agent.AFDT | LittleDaemon. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 8.212.132[.]120 | ds20221202.dsc. |
Alibaba (US) Know-how Co., Ltd. | 2024‑07‑12 | DNS/Hijacking node. |
| 47.242.198[.]250 | check.dsc.wcsset |
Alibaba Cloud LLC | 2024‑07‑12 | DNS/Hijacking node. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 18 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Useful resource Improvement | T1583.001 | Purchase Infrastructure: Domains | PlushDaemon makes use of EdgeStepper to redirect visitors to particular subdomains which are a part of PlushDaemon’s infrastructure on wcsset[.]com. |
| T1583.002 | Purchase Infrastructure: DNS Server | A part of the PlushDaemon infrastructure is used to host its malicious DNS nodes. | |
| T1583.004 | Purchase Infrastructure: Server | PlushDaemon has acquired servers to host its DNS/hijacking nodes and C&C servers. | |
| T1608.001 | Stage Capabilities: Add Malware | PlushDaemon hosts its payloads on DNS/hijacking servers. | |
| Preliminary Entry | T1659 | Content material Injection | Hijacking nodes from PlushDaemon course of hijacked visitors and reply to authentic software program with directions to obtain malware equivalent to LittleDaemon. |
| Execution | T1106 | Native API | DaemonicLogistics executes the SlowStepper implant utilizing the ShellExecute API. |
| Protection Evasion | T1070.004 | Indicator Elimination: File Deletion | Some variants of LittleDaemon can take away themselves. |
| T1036.005 | Masquerading: Match Authentic Identify or Location | DaemonicLogistics creates a subdirectory named Tencent, the place it shops its recordsdata. | |
| T1036.008 | Masquerading: Masquerade File Sort | DaemonicLogistics and SlowStepper’s loader can decrypt recordsdata that masquerade as ZIP and GIF recordsdata. | |
| T1027.009 | Obfuscated Recordsdata or Info: Embedded Payloads | Recordsdata masquerading as ZIPs and GIF recordsdata comprise embedded encrypted elements. | |
| T1027.013 | Obfuscated Recordsdata or Info: Encrypted/Encoded File | Elements of the SlowStepper implant are encrypted on disk. | |
| Discovery | T1518.001 | Software program Discovery: Safety Software program Discovery | DaemonicLogistics checks for the presence of 360tray.exe – a element of 360 Complete Safety. |
| T1016 | System Community Configuration Discovery | DaemonicLogistics makes an attempt to acquire the ethernet or Wi-Fi adapter’s MAC handle. | |
| T1057 | Course of Discovery | DaemonicLogistics lists processes. | |
| Command and Management | T1071.001 | Software Layer Protocol: Internet Protocols | LittleDaemon and DaemonicLogistics use HTTP to speak with their server. |
| T1573 | Encrypted Channel | LittleDaemon downloads by way of HTTP the encrypted DaemonicLogistics that downloads by way of HTTP the encrypted SlowStepper implant. | |
| T1665 | Conceal Infrastructure | LittleDaemon and DaemonicLogistics make downloads by sending HTTP requests to authentic domains. |


