Over 1,000 CrushFTP situations presently uncovered on-line are weak to hijack assaults that exploit a essential safety bug, offering admin entry to the online interface.
The safety vulnerability (CVE-2025-54309) is because of mishandled AS2 validation and impacts all CrushFTP variations under 10.8.5 and 11.3.4_23. The seller tagged the flaw as actively exploited within the wild on July nineteenth, noting that assaults could have begun earlier, though it has but to seek out proof to substantiate this.
“July 18th, 9AM CST there’s a 0-day exploit seen within the wild. Presumably it has been happening for longer, however we noticed it then. Hackers apparently reverse engineered our code and located some bug which we had already mounted,” reads CrushFTP’s advisory
“They’re exploiting it for anybody who has not stayed present on new variations. As all the time we advocate recurrently and frequent patching. Anybody who had stored updated was spared from this exploit.”
Nevertheless, CrushFTP added final week that servers which have been stored updated will not be weak to assaults, stating that prospects who use a demilitarized zone (DMZ) occasion to isolate their most important server aren’t impacted by this vulnerability.
The corporate additionally recommends reviewing add and obtain logs for uncommon exercise, in addition to enabling computerized updates and whitelisting IPs for server and admin entry to additional mitigate exploitation makes an attempt.
In line with scans from the safety risk monitoring platform Shadowserver, roughly 1,040 CrushFTP situations stay unpatched towards CVE-2025-54309 and are weak to assaults.
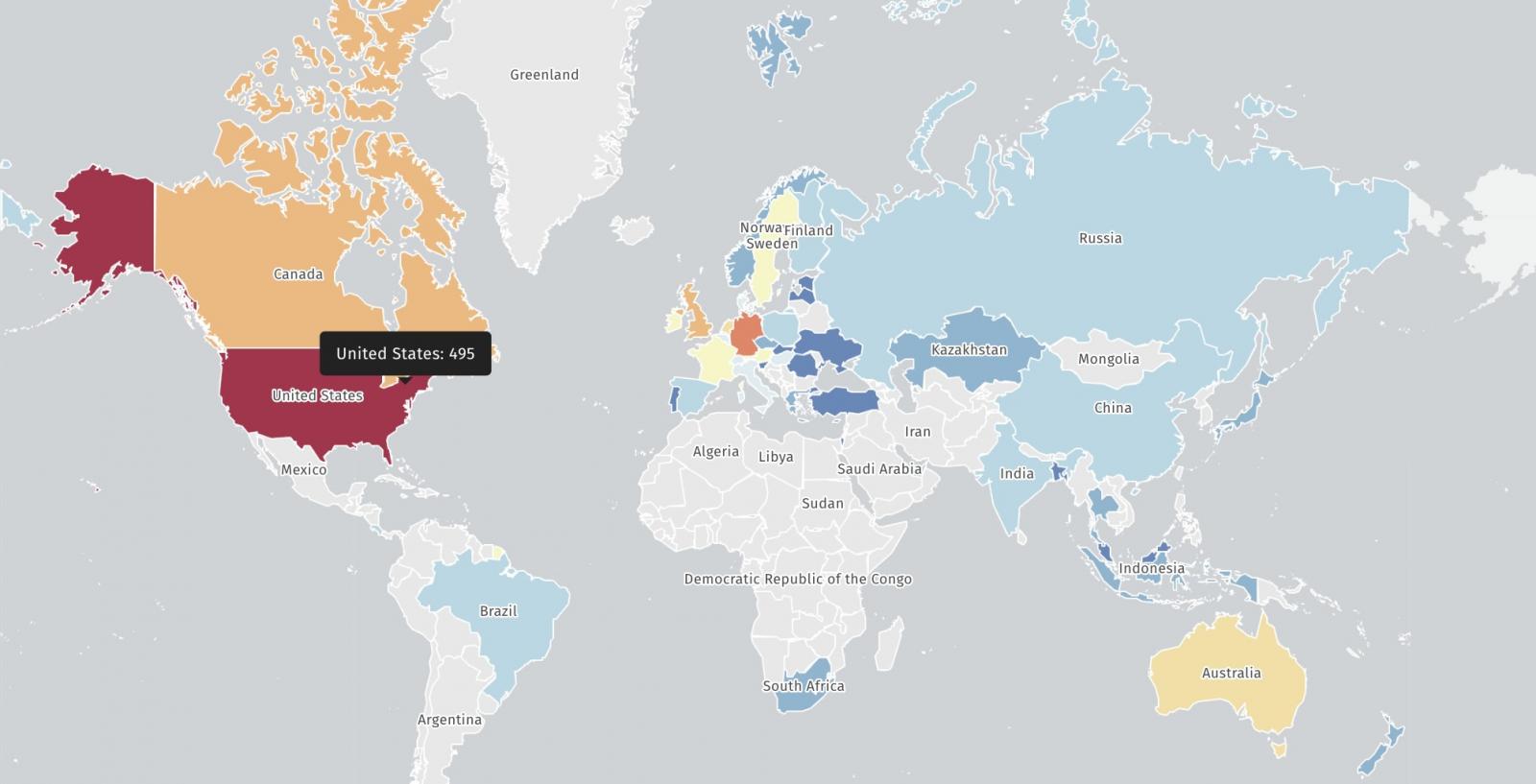
ShadowServer is now notifying CrushFTP prospects that their servers are unprotected towards ongoing CVE-2025-54309 exploitation, exposing their contents to knowledge theft makes an attempt.
Whereas it is unclear if these ongoing assaults deploy malware or had been used for knowledge theft, managed file switch options like CrushFTP have been high-value targets for ransomware gangs lately.
As an illustration, the Clop cybercrime gang alone has been linked to a number of knowledge theft campaigns concentrating on zero-day flaws in Accelion FTA, GoAnywhere MFT, MOVEit Switch, and, most not too long ago, Cleo software program.
One 12 months in the past, in April 2024, CrushFTP additionally patched an actively exploited zero-day (tracked as CVE-2024-4040) that allowed unauthenticated attackers to flee the person’s digital file system (VFS) and obtain system information.
On the time, the cybersecurity firm CrowdStrike discovered proof that the assaults, which focused CrushFTP situations at a number of U.S. organizations and centered on intelligence gathering, had been possible politically motivated.
CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud safety drives enterprise worth.
This free, editable board report deck helps safety leaders current threat, impression, and priorities in clear enterprise phrases. Flip safety updates into significant conversations and quicker decision-making within the boardroom.


