Safety researchers have uncovered a brand new assault marketing campaign by the North Korean state-sponsored APT group Kimsuky, also referred to as “Black Banshee.”
The group, lively since at the least 2012, has been noticed using superior techniques and malicious scripts of their newest cyber espionage efforts concentrating on international locations similar to South Korea, Japan, and the US.
The assault begins with a ZIP file containing 4 parts: a VBScript, a PowerShell script, and two encoded textual content recordsdata.
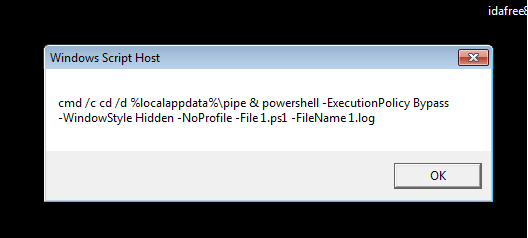
The VBScript makes use of obfuscation methods, leveraging chr() and CLng() capabilities to dynamically generate characters and execute instructions, successfully bypassing signature-based detection strategies.
Multi-Stage Payload Evaluation
Upon execution, the preliminary script triggers a PowerShell part that decodes base64-encoded information from one of many textual content recordsdata.
Based on the Report, this decoded script performs a number of crucial capabilities, together with system reconnaissance, information exfiltration, and command-and-control (C2) communication.
The malware displays VM-aware habits, terminating its execution if it detects a digital machine atmosphere.
For non-VM targets, it proceeds to gather delicate data, together with the BIOS serial quantity, which is used to create a singular listing for storing attack-related recordsdata.


Superior Information Theft and Persistence Mechanisms
The Kimsuky malware demonstrates subtle capabilities for information exfiltration.
It targets a number of browsers, together with Edge, Firefox, Chrome, and Naver Whale, to extract person profiles, cookies, login data, and net information.
The malware additionally searches for cryptocurrency pockets extensions and harvests their related recordsdata.
Moreover, the malware creates a complete system profile, gathering {hardware} data, community adapter standing, and an inventory of put in packages.
It implements persistence by way of scheduled duties and repeatedly displays the system for brand spanking new information to exfiltrate.
Within the last stage of the assault, the malware deploys a keylogger part.
This module imports Home windows API capabilities to detect key presses, monitor clipboard exercise, and log window titles.


The collected information is periodically uploaded to the attacker’s C2 server, offering real-time surveillance of the sufferer’s actions.
The Kimsuky group’s evolving techniques and multi-component strategy spotlight the rising sophistication of state-sponsored cyber threats.


As these assaults develop into extra evasive and sophisticated, organizations should stay vigilant and make use of strong safety measures to guard in opposition to such superior persistent threats.
Are you from SOC/DFIR Groups? – Analyse Malware, Phishing Incidents & get dwell Entry with ANY.RUN -> Begin Now for Free.

.webp?w=696&resize=696,0&ssl=1)