A breakthrough framework named SCAVY has been launched to proactively detect reminiscence corruption targets that might probably result in privilege escalation within the Linux kernel.
Introduced on the prestigious USENIX Safety Symposium in August 2024, the framework goals to deal with long-standing gaps in understanding how reminiscence corruption will be exploited to compromise system integrity.
SCAVY’s builders have hailed it as a brand new device within the struggle towards Linux kernel vulnerabilities, urging researchers to take proactive measures.
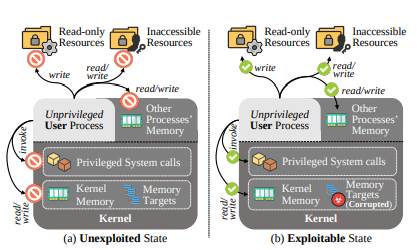
Privilege escalation assaults sometimes exploit reminiscence corruption vulnerabilities within the Linux kernel. By focusing on particular reminiscence places, attackers can elevate their permissions, enabling unauthorized entry to assets corresponding to information or processes.
Traditionally, defenders have centered on figuring out identified vulnerabilities, however solely a small subset of kernel reminiscence constructions—these with perform pointers—have been systematically explored.
Roughly 90% of Linux kernel constructions stay neglected, leaving a considerable assault floor unprotected.
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Risk Intelligence Lookup - Attempt for Free
Enter SCAVY: A Recreation-Changer
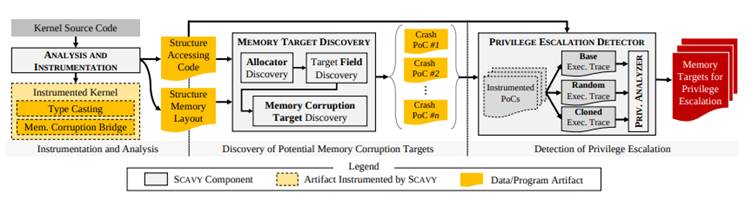
SCAVY (brief for “Scavenger”) is a cutting-edge automated framework designed to determine kernel reminiscence corruption targets past the historically prioritized perform pointers.
In contrast to earlier instruments that focus narrowly on particular vulnerabilities, SCAVY adopts a broader, vulnerability-agnostic method. The device systematically explores kernel reminiscence constructions to detect areas that, if corrupted, may escalate privileges.
SCAVY combines superior fuzzing methods with differential evaluation to guage how reminiscence corruption modifications entry to delicate assets. By evaluating system conduct with and with out corruption, SCAVY pinpoints exploitable fields in kernel constructions.
Key Improvements of SCAVY:
- Broader Scope: SCAVY examines all reminiscence fields in Linux kernel constructions, together with the 88.7% beforehand unexplored.
- Automated Goal Discovery: The framework autonomously identifies reminiscence corruption targets by way of environment friendly fuzzing and execution-state reasoning.
- Protection-Bypassing Capabilities: SCAVY can uncover privilege escalation vectors that evade current defenses corresponding to Management Stream Integrity (CFI) and Kernel Tackle Area Structure Randomization (KASLR).
By way of its complete evaluation, SCAVY found 955 proof-of-concept (PoC) exploits, highlighting 17 beforehand unknown reminiscence corruption targets unfold throughout 12 kernel constructions.
SCAVY additionally demonstrated its potential by creating six exploits for 5 identified CVE vulnerabilities. These exploits showcased how new reminiscence targets may make once-dismissed vulnerabilities exploitable.
A Actual-World Case Research:
One notable goal recognized by SCAVY is the vm_area_struct::vm_file area. In apply, modifying this area enabled attackers to control non permanent information and achieve unauthorized entry to privileged information like /and many others/passwd.
The researchers carried out a PoC utilizing the CVE-2022-27666 vulnerability to take advantage of this reminiscence goal with out triggering conventional kernel defenses, corresponding to Supervisor Mode Entry Prevention (SMAP).

SCAVY not solely enhances attackers’ capabilities but in addition offers defenders with unprecedented alternatives to proactively deal with vulnerabilities.
By figuring out broader classes of reminiscence corruption targets, the framework equips builders with insights to safe kernel constructions extra successfully.
For instance, focused protections corresponding to slab cache randomization or write-once reminiscence insurance policies might be deployed for fields recognized by SCAVY, decreasing system overhead in comparison with broader defenses.
The findings spotlight the pressing want for kernel builders and safety researchers to re-evaluate the definition of privilege escalation targets inside the Linux kernel ecosystem.
The analysis workforce behind SCAVY has made the framework’s supply code open for future research, offering the broader neighborhood with a strong new device. Particulars, documentation, and the PoC exploits can be found by way of the SCAVY GitHub repository.
Whereas SCAVY introduces a sturdy methodology for figuring out single-field reminiscence corruption targets, the researchers acknowledge the necessity for additional work.
Automating multi-field goal evaluation and integrating SCAVY into bigger exploit-generation pipelines may unlock even better potential for each assault simulation and protection mechanism design.
SCAVY marks a revolution in addressing safety issues within the Linux kernel, bridging important gaps in automated goal discovery for privilege escalation.
By broadening the assault floor and introducing environment friendly methods to counter these exploits, SCAVY is poised to turn out to be an important asset in securing Linux methods worldwide.
Integrating Software Safety into Your CI/CD Workflows Utilizing Jenkins & Jira -> Free Webinar

