A brand new and complicated phishing rip-off has been uncovered, leveraging Microsoft 365 domains to trick customers into compromising their PayPal accounts.
The assault exploits legitimate-looking sender addresses and URLs, making it more durable for victims to acknowledge the phishing try.
Safety consultants, together with Chief Info Safety Officers (CISOs), have raised alarms in regards to the rising menace, urging warning and vigilance, shared by Fortinet.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free
How the Rip-off Works
This phishing marketing campaign makes use of Microsoft 365’s free trial domains to craft authentic-looking e mail addresses.

As soon as a scammer registers a trial area, they arrange misleading distribution lists with obscure addresses resembling authentic ones.
For instance, an e mail may seem to originate from “Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com,” which at first look may look credible to unsuspecting customers. Right here’s the rip-off’s modus operandi step-by-step:
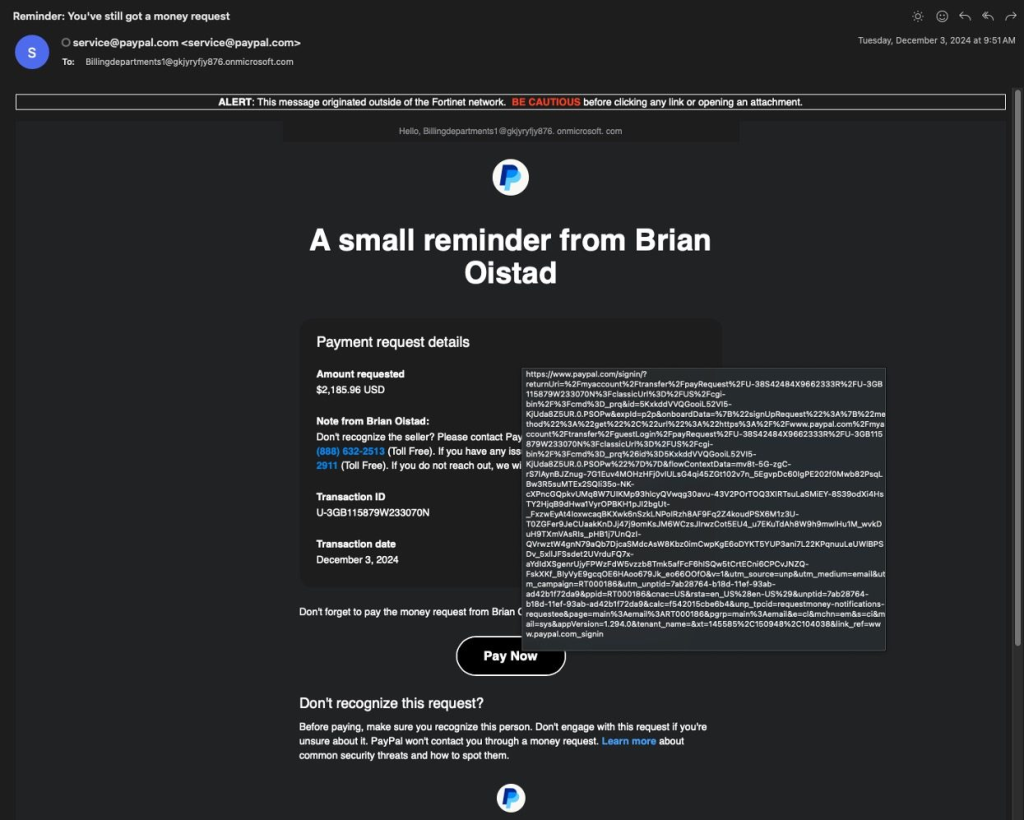
- The Cash Request E-mail: The attacker makes use of the PayPal interface to ship fee requests to the distribution checklist they created. This makes it seem PayPal itself is searching for cash from the victims. The e-mail is technically authentic and passes sender authentication strategies like SPF, DKIM, and DMARC checks, making it indistinguishable from actual PayPal communications.
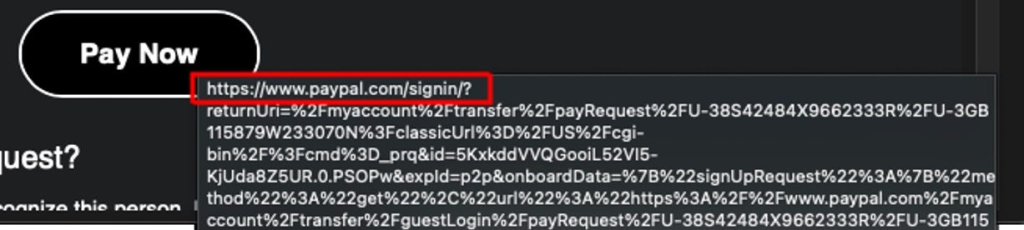
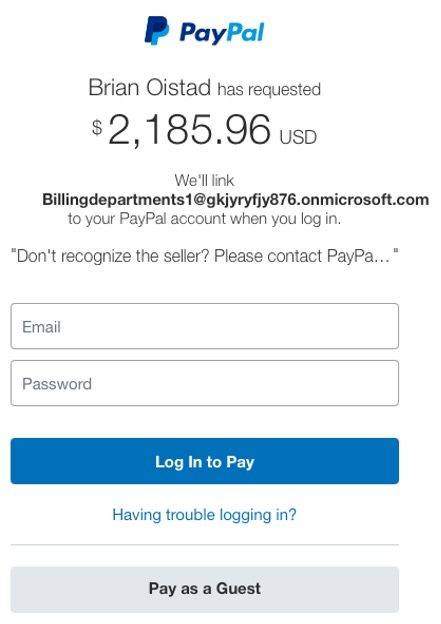
- The Phishing Hook: Upon receiving the e-mail, victims who click on the embedded hyperlink are directed to what seems like an official PayPal login web page. The web page shows the fee request, creating a way of urgency and panic. Many victims proceed to log in with out suspicion, thereby falling into the scammer’s entice.
- Account Takeover: As soon as the sufferer logs in, their PayPal account turns into linked to the scammer’s e mail deal with, akin to “Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com.” This permits the attacker to entry the sufferer’s account, probably transferring funds or stealing delicate info.

Why This Rip-off is Harmful
The cleverness of this assault lies in its leveraging of authentic applied sciences. By utilizing free Microsoft 365 take a look at domains, the scammers bypass typical detection methods.
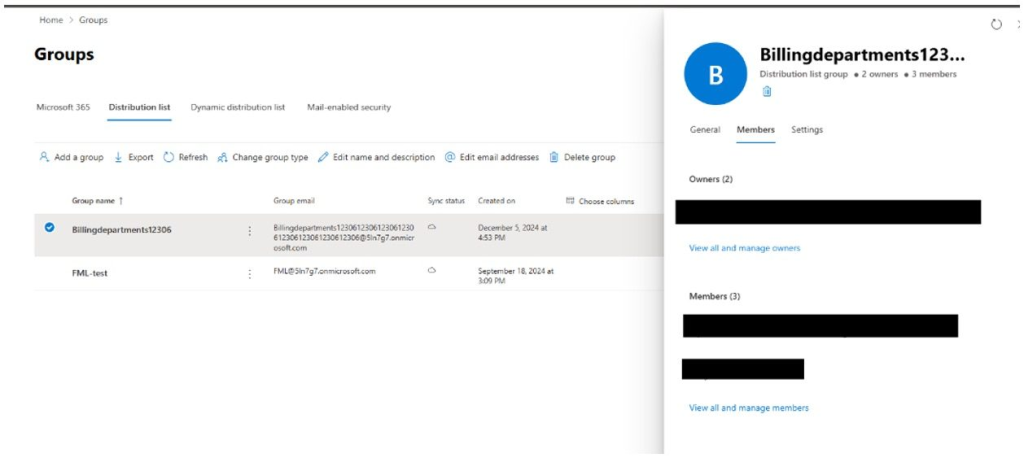

The distribution checklist function additional obfuscates the true sender, creating believable deniability. Even PayPal’s phishing detection directions would fail to flag this technique.
Most dangerously, the phishing e mail’s sender deal with and hyperlinks seem genuine, and the e-mail passes commonplace safety checks. This raises the stakes, as even tech-savvy customers may fall for the rip-off.
Consultants urge vigilance when dealing with fee requests, even from seemingly authentic sources. Listed below are some security suggestions:
- Confirm Requests: All the time double-check fee requests instantly inside your PayPal account slightly than counting on e mail hyperlinks.
- Scrutinize Sender Addresses: Look fastidiously on the sender deal with for anomalies or inconsistencies.
- Allow Two-Issue Authentication (2FA): This provides an additional layer of safety to your PayPal account.
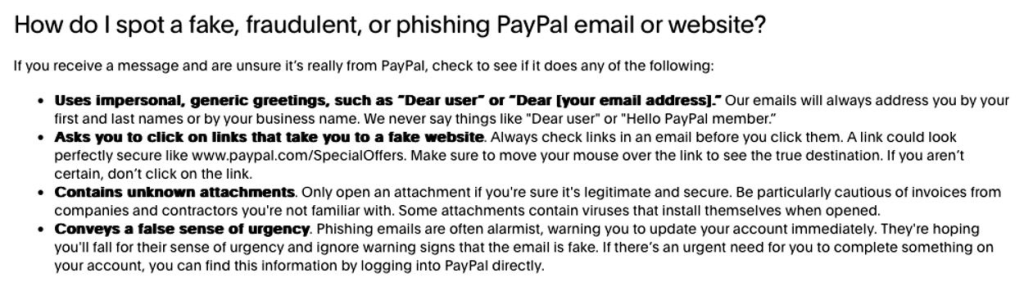

As attackers proceed to innovate, staying knowledgeable and cautious is important. PayPal customers, particularly these dealing with company accounts, should prioritize cybersecurity to keep away from falling sufferer to threats like these.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Immediate Updates!

