A vital mixture of legacy parts might have allowed full entry to the Microsoft Entra ID tenant of each firm on the planet.
The deadly combine included undocumented tokens known as “actor tokens” and a vulnerability within the Azure AD Graph API (CVE-2025-55241) that allowed the tokens to work with any group’s Entra ID atmosphere.
A menace actor exploiting the difficulty would have had entry to a slew of extremely delicate knowledge with out leaving any hint within the logs on the focused atmosphere, apart from their very own actions.
Entra ID is Microsoft’s cloud-based id and entry administration (IAM) service, previously generally known as Azure Energetic Listing (Azure AD), which supplies organizations with single sign-on, multi-factor authentication, and safety controls throughout apps and assets.
A devoted Entra ID occasion represents a single group and manages safe entry to all of the apps used, each on-premise and cloud-based.
This could embrace Microsoft 365 companies, customized and third-party SaaS merchandise like Salesforce, Dropbox, or cloud apps from Google, Amazon, or SAP.
Safety researcher Dirk-jan Mollema, founding father of offensive safety Outsider Safety, found a token validation flaw that gave him World Admin privileges in each Entra ID tenant.
This degree of entry permits full tenant compromise and opens the door to any service authenticated via Entra ID.
Impersonating any person within the tenant
In a technical weblog publish, Mollema explains that actor tokens are issued by a legacy service known as Entry Management Service, which “is used for authentication with SharePoint purposes and in addition appears to be utilized by Microsoft internally.”
The researcher discovered them whereas investigating hybrid Change setups. He seen that Change would request them when speaking with different companies on behalf of a person.
“The Actor token permits it to ‘act’ as one other person within the tenant when speaking to Change On-line, SharePoint and because it seems the Azure AD Graph” – Dirk-jan Mollema
Actor tokens should not signed, that means they can be utilized to impersonate any person within the tenant, and have a 24-hour validity with out the potential of being revoked throughout this era.
Mollema says that “this entire Actor token design is one thing that by no means ought to have existed,” as a result of they lack the right required safety controls:
- there aren’t any logs when Actor tokens are issued
- since these companies can craft the unsigned impersonation tokens with out speaking to Entra ID, there are additionally no logs when they’re created or used
- they can’t be revoked inside their 24-hour validity
- they fully bypass any restrictions configured in Conditional Entry
- now we have to depend on logging from the useful resource supplier to even know these tokens have been used within the tenant
The researcher says that Microsoft depends on actor tokens internally for service-to-service communication and that the corporate plans to take away them.
Microsoft calls them “high-privileged entry (HPA)” that permits an software or service, “to impersonate different customers with out offering any proof of person context.
Whereas testing a number of methods to make use of an actor token, Mollema modified the tenant ID to at least one totally different from that producing the token, and despatched it to the deprecated Azure AD Graph API (graph.home windows.web), anticipating an “entry denied” message.
As an alternative, the error the researcher noticed indicated that the token was legitimate, however entry was unauthorized as a result of the id of the person was not discovered within the tenant.
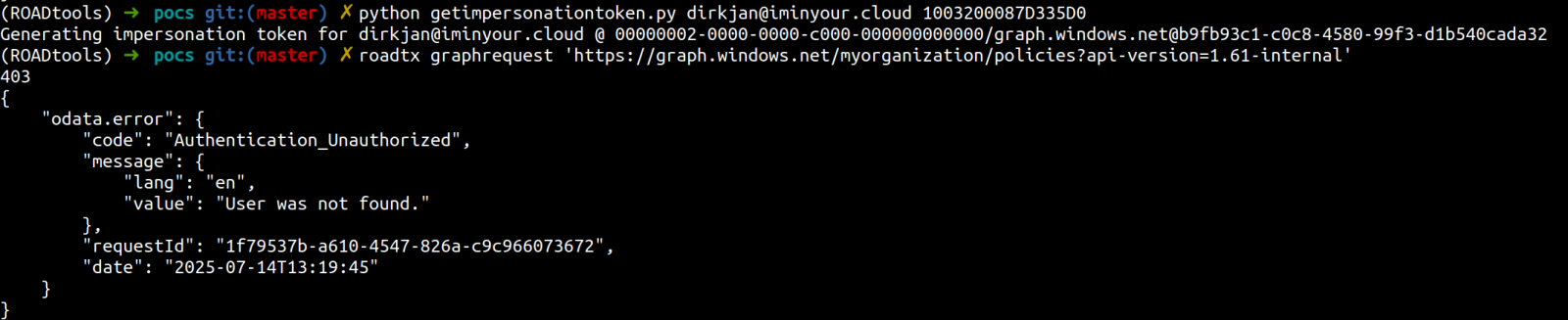
supply: Dirk-jan Mollema
Mollema tried once more, this time with a sound person ID from the focused tenant, and noticed Azure AD Graph API return the requested knowledge.
“I examined this in a number of extra take a look at tenants I had entry to, to verify I used to be not loopy, however I might certainly entry knowledge in different tenants, so long as I knew their tenant ID (which is public info) and the netId of a person in that tenant.”
Utilizing the identical actor token, the researcher was in a position to impersonate the World Administrator within the goal tenant and carry out all of the actions related to the position (e.g. handle and create customers of various roles, modify configurations, reset passwords, add admins).
Mollema highlights that not one of the actions required for acquiring World Admin privileges generated any logs within the sufferer tenant.
From an attacker’s perspective, exploiting the problems would have been doable in a number of steps, beginning with producing the actor token from a tenant underneath their management:
- Discovering the tenant ID for the focused atmosphere could be accomplished with public APIs based mostly on the area title
- Discovering a sound netId of an everyday person within the goal tenant
- Crafting an impersonation token with the actor token from the attacker tenant utilizing the tenant ID and netId of the person within the sufferer tenant
- Itemizing all World Admins within the tenant and their netId
- Crafting an impersonation token for the World Admin
- Performing any learn/write motion via the Azure AD Graph API
Mollema notes that solely exercise within the final step could be recorded within the sufferer tenant.
It is very important observe that Microsoft began the deprecation course of for the Azure AD Graph API service in September final 12 months.
In late June, the corporate warned that apps configured for prolonged entry however nonetheless used Azure AD Graph would not be capable of use the APIs beginning early September 2025.
Mollema reported the problems to Microsoft on July 14 and the corporate confirmed that the issue was resolved 9 days later.
On September 4, Microsoft additionally patched CVE-2025-55241, describing it as a vital privilege escalation vulnerability in Azure Entra.


