Evasive Panda, a classy risk actor identified by the aliases Bronze Highland, Daggerfly, and StormBamboo, has escalated its offensive capabilities via a two-year marketing campaign that has deployed superior assault strategies,, together with adversary-in-the-middle (AitM) assaults and DNS poisoning.
In accordance with June 2025 analysis, the group maintained persistent operations between November 2022 and November 2024, concentrating on victims throughout Turkey, China, and India with evolving malware supply mechanisms designed to evade detection.
The marketing campaign reveals a marked evolution within the risk actor’s operational method. Moderately than counting on direct distribution strategies, Evasive Panda orchestrated highly-targeted assaults utilizing AitM strategies mixed with DNS poisoning to intercept professional site visitors and redirect victims to attacker-controlled servers.
The attackers distributed loaders disguised as professional software updates together with SohuVA, iQIYI Video, IObit Sensible Defrag, and Tencent QQ exploiting consumer belief in acquainted software program distributors to ascertain preliminary system entry.
Technical Sophistication
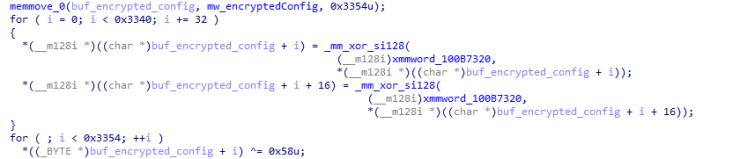
The sophistication of Evasive Panda’s loader demonstrates vital improvement funding. Written in C++ utilizing the Home windows Template Library (WTL), the malware employs a number of encryption layers and obfuscation strategies to complicate evaluation.
The loader makes use of XOR-based decryption algorithms to show configuration components solely after execution, whereas all vital strings together with system paths and command execution parameters stay encrypted till runtime.
Most notably, the attackers developed a novel injector enabling in-memory execution of their MgBot implant inside professional processes.
By leveraging DLL sideloading strategies with a decade-old signed executable (evteng.exe), the group achieved persistent presence with out writing major payloads to disk. This method considerably reduces detection floor and complicates forensic investigation.
The DNS poisoning mechanism represents the marketing campaign’s most revolutionary component. Attackers manipulated DNS responses for professional web sites, together with dictionary.com, redirecting victims’ techniques to attacker-controlled infrastructure primarily based on geographical location and ISP affiliation.
The malware retrieves encrypted payloads disguised as PNG photographs from these poisoned domains, with payload choice tailor-made to the sufferer’s Home windows model and system configuration.
The an infection chain employs multi-stage execution: the preliminary loader decrypts shellcode and retrieves encrypted second-stage payloads via DNS-poisoned site visitors.
To stop interception and evaluation, attackers carried out customized hybrid encryption combining Microsoft’s Knowledge Safety API (DPAPI) with RC5 encryption.
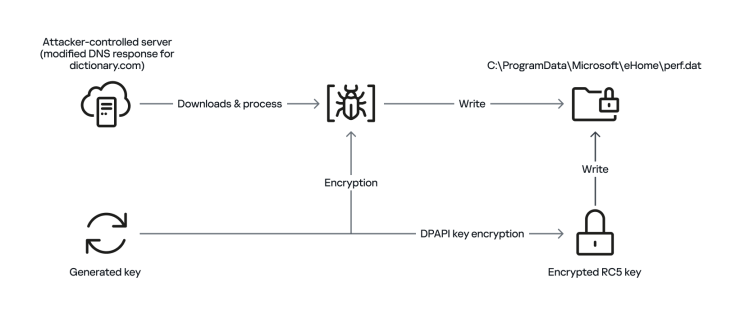
This method ensures payload decryption happens completely on compromised techniques, creating uneven benefits for defenders making an attempt forensic restoration.
Persistence and Attribution
Some compromised techniques maintained energetic infections for over one yr, indicating sustained operational dedication.
The attackers maintained a number of command-and-control (C2) servers energetic for years, suggesting deliberate infrastructure redundancy designed to protect management regardless of potential takedown operations.
Attribution to Evasive Panda seems extremely assured primarily based on tactical convergence with historic operations.
The group’s constant use of supply-chain compromise, AitM strategies, and watering-hole assaults mixed with the resurgent MgBot implant with enhanced configuration components aligns with established risk actor behaviors.
Regardless of technical visibility, vital operational gaps stay. Researchers have but to find out how Evasive Panda initially compromises community infrastructure to execute DNS poisoning at scale.
Two believable situations exist: both selective ISP community implants had been deployed, or victim-controlled community gadgets (routers, firewalls) had been independently compromised.
The marketing campaign demonstrates sustained evolution inside Evasive Panda’s toolkit. New loader improvement suggests extra functionality enhancements stay forthcoming.
Organizations ought to implement sturdy DNS monitoring, community segmentation limiting lateral motion potential, and endpoint detection mechanisms tuned for multi-stage shellcode execution patterns.
Comply with us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most well-liked Supply in Google.

