North Korean state-sponsored menace actors have escalated their cyber operations with the deployment of subtle new malware variants designed to ascertain persistent backdoor entry to compromised programs.
Latest investigations by menace intelligence researchers have uncovered two distinct toolsets from outstanding DPRK-aligned hacking teams: Kimsuky’s newly recognized HttpTroy backdoor and an upgraded model of Lazarus’s BLINDINGCAN distant entry device.
Each campaigns exhibit the continued evolution of North Korean cyber capabilities and their dedication to espionage operations concentrating on strategic victims throughout a number of international locations.
The discoveries underscore a troubling pattern in superior persistent menace actor conduct, the place established teams constantly refine their tradecraft to evade detection whereas sustaining operational effectiveness.
Safety researchers emphasize that these instruments signify important developments within the DPRK cyber arsenal, incorporating a number of layers of obfuscation and complex persistence mechanisms that problem conventional defensive measures.
The Kimsuky operation focused a single sufferer in South Korea utilizing a social engineering strategy designed to look as legit enterprise correspondence.
The assault chain started with a ZIP archive masquerading as a VPN service bill, particularly named to reference a Korean firm and SSL VPN administration companies.
As soon as executed, the malicious payload initiated a multi-stage an infection course of that in the end delivered the HttpTroy backdoor to the compromised system.
The an infection sequence includes three distinct elements working in live performance to ascertain persistent entry. First, a light-weight Go-based dropper containing three embedded recordsdata performs preliminary system compromise whereas displaying a decoy PDF doc to take care of the phantasm of legitimacy.
This dropper makes use of easy XOR encryption with the important thing 0x39 to decrypt its embedded payloads earlier than writing them to disk. The assault chain then progresses to MemLoad_V3, a first-stage backdoor accountable for establishing persistence by means of a scheduled activity impersonating AhnLab antivirus replace performance.
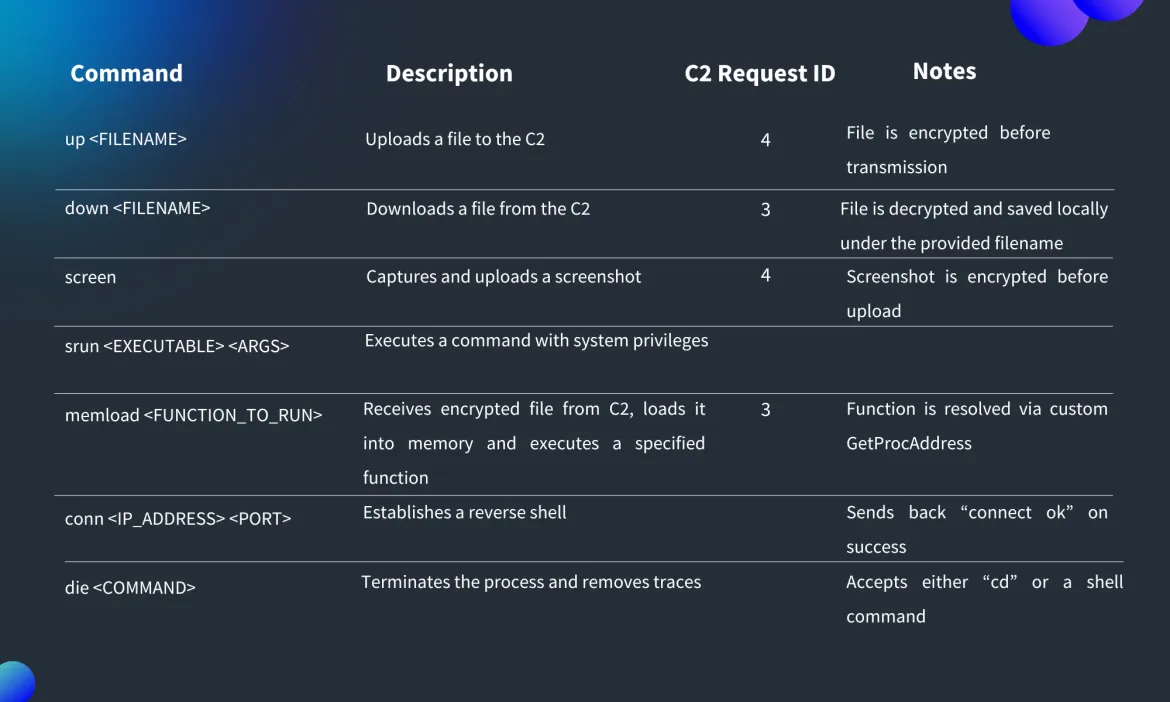
The ultimate HttpTroy payload represents a extremely succesful backdoor providing attackers complete management over contaminated programs.
Its performance consists of file add and obtain capabilities, screenshot seize and exfiltration, command execution with elevated privileges, in-memory executable loading, reverse shell institution, and course of termination for hint removing.
Communication with command-and-control infrastructure happens solely by means of HTTP POST requests, with all knowledge obfuscated utilizing XOR encryption and Base64 encoding.
BLINDINGCAN Distant Entry Capabilities
Parallel to the Kimsuky marketing campaign, Lazarus Group focused two victims in Canada with an up to date variant of their established BLINDINGCAN distant entry device.
Researchers intercepted this assault mid-chain, observing a brand new model of the Comebacker malware facilitating deployment of the improved BLINDINGCAN variant.
Whereas technical particulars of this particular marketing campaign stay below investigation, the operation demonstrates Lazarus’s ongoing dedication to sustaining and enhancing their present malware frameworks.
Each campaigns share frequent traits typical of DPRK cyber operations, together with heavy use of obfuscation strategies to complicate evaluation and evade safety options.
HttpTroy particularly employs customized API hashing, dynamic string reconstruction throughout runtime, and SIMD instruction-based obfuscation to withstand each static and dynamic evaluation makes an attempt.
All transmitted knowledge (each instructions and responses) is obfuscated utilizing a two-step course of: XOR encryption with the important thing 0x56, adopted by Base64 encoding.

Safety professionals advocate organizations implement a number of defensive layers to mitigate threats from subtle state-sponsored actors.
Important measures embody treating surprising electronic mail attachments with excessive warning, recognizing that recordsdata with extensions like .scr are executable packages relatively than paperwork, sustaining up to date safety software program with present menace intelligence, and implementing behavioral detection capabilities that may determine suspicious post-compromise actions.
The emergence of those new instruments reinforces the persistent and adaptive nature of North Korean cyber menace actors, requiring steady vigilance and up to date defensive methods from potential goal organizations.
Observe us on Google Information, LinkedIn, and X to Get Immediate Updates and Set GBH as a Most well-liked Supply in Google.

