Cybercriminals have launched a classy phishing marketing campaign that exploits belief in inside safety methods by spoofing e-mail supply notifications to look as professional spam-filter alerts inside organizations.
These misleading emails are designed to steal login credentials that might compromise e-mail accounts, cloud storage, and different delicate methods.
The assault begins with an e-mail claiming that latest upgrades to the group’s Safe Message system have resulted in pending messages failing to achieve the recipient’s inbox.
The notification shows a professional-looking supply report that features the goal’s e-mail deal with, generic message topics designed to not elevate suspicion, and standing data offered in a structured format.

Recipients are urged to click on a “Transfer to Inbox” button to retrieve these supposedly held messages, with assurances that supply will happen inside one to 2 hours after affirmation.
The Technical Deception
Each the first motion button and the unsubscribe hyperlink make use of a redirect mechanism by way of cbssports[.]com to masks the true vacation spot a phishing website hosted on the area mdbgo[.]io.
Safety researchers at Unit42 initially recognized this marketing campaign kind, prompting deeper investigation into its mechanics.
The phishing infrastructure demonstrates notable sophistication. Hyperlinks throughout the spoofed emails cross the goal’s e-mail deal with as a base64-encoded string to the phishing website, which then presents a faux login display screen with the sufferer’s area pre-populated.
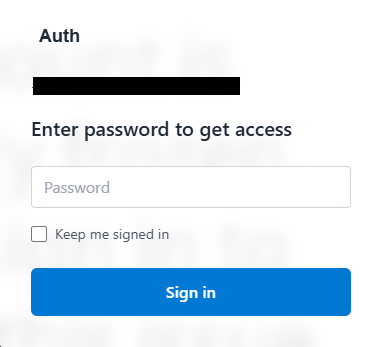

This personalization creates an phantasm of legitimacy that may idiot even cautious customers.
Latest evaluation reveals this assault variant has grow to be extra superior than initially reported. The phishing website employs closely obfuscated code and harvests credentials by way of websocket know-how a persistent connection between the browser and server that operates like a steady cellphone name.
In contrast to conventional internet varieties that submit information when customers click on submit, websockets transmit data immediately as victims kind.


This real-time information exfiltration permits attackers to obtain credentials the second they’re entered and even ship further prompts requesting two-factor authentication codes.
As soon as attackers receive these particulars, they’ll instantly entry e-mail accounts, cloud-stored recordsdata, reset passwords for different companies, and impersonate victims throughout a number of platforms.
Safety Methods
Safety specialists emphasize two basic guidelines for avoiding these threats: by no means open unsolicited attachments, and all the time confirm the web site deal with in your browser earlier than getting into credentials to make sure it matches the anticipated professional website.
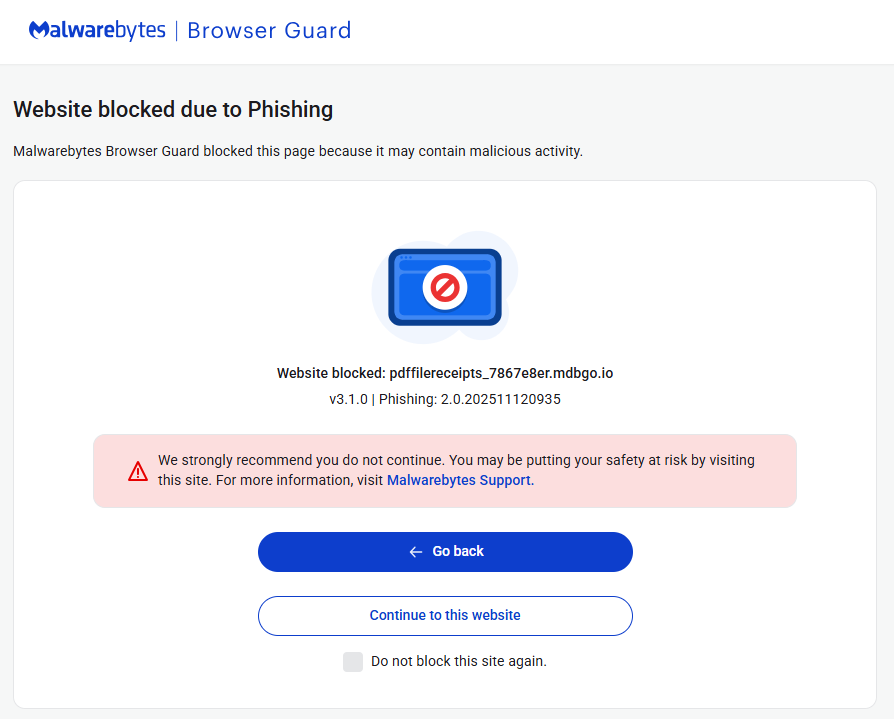
In case you’ve already entered credentials on a suspicious website, instantly change your passwords. Safety options like Malwarebytes Browser Guard can present a further layer of protection by blocking entry to identified phishing websites earlier than credentials are entered.

Further protecting measures embody verifying sender e-mail addresses for authenticity, confirming sudden attachments or hyperlinks by way of various communication channels, sustaining up to date safety software program with internet safety capabilities, holding all units and software program present, enabling multi-factor authentication on all accounts, and utilizing password managers that gained’t auto-fill credentials on fraudulent websites.
Organizations ought to educate workers about spoofing techniques, the place cybercriminals impersonate trusted entities to achieve confidence, entry methods, steal information, or unfold malware.
E mail spoofing entails explicitly sending messages with false sender addresses as a part of phishing assaults designed to steal data or set up malware.
Comply with us on Google Information, LinkedIn, and X to Get Prompt Updates and Set GBH as a Most well-liked Supply in Google.

