Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke
KnowBe4 Menace Labs lately examined a complicated dual-vector marketing campaign that demonstrates the real-world exploitation chain following credential compromise. This isn’t a standard virus assault. As a substitute of deploying customized viruses, attackers are bypassing safety perimeters by weaponizing the required IT instruments that directors belief. By stealing a “skeleton key” to the system, they flip professional Distant Monitoring and Administration (RMM) software program right into a persistent backdoor.
Phishing Assault Abstract
- Vector and Kind: Electronic mail Phishing / Twin-vector assault that strikes from credential harvesting to full system takeover
- Strategies: model impersonation, credential harvesting, RMM deployment
- Bypassed SEG detection: Sure
- Targets: Organizations globally
The Two-Wave Assault Technique
This marketing campaign operates in two distinct waves: first by harvesting credentials by way of faux invitation notifications, then weaponizing these credentials to deploy professional RMM software program that establishes persistent backdoor entry to sufferer programs.
Wave 1: Credential Harvesting
The assault begins with a phishing electronic mail disguised as a Greenvelope invitation. As a result of Greenvelope is a professional service used for company occasions and weddings, the “Social Engineering Indicators” are refined. Victims who click on the invitation are directed to a extremely convincing spoofed login web page designed to seize their credentials.
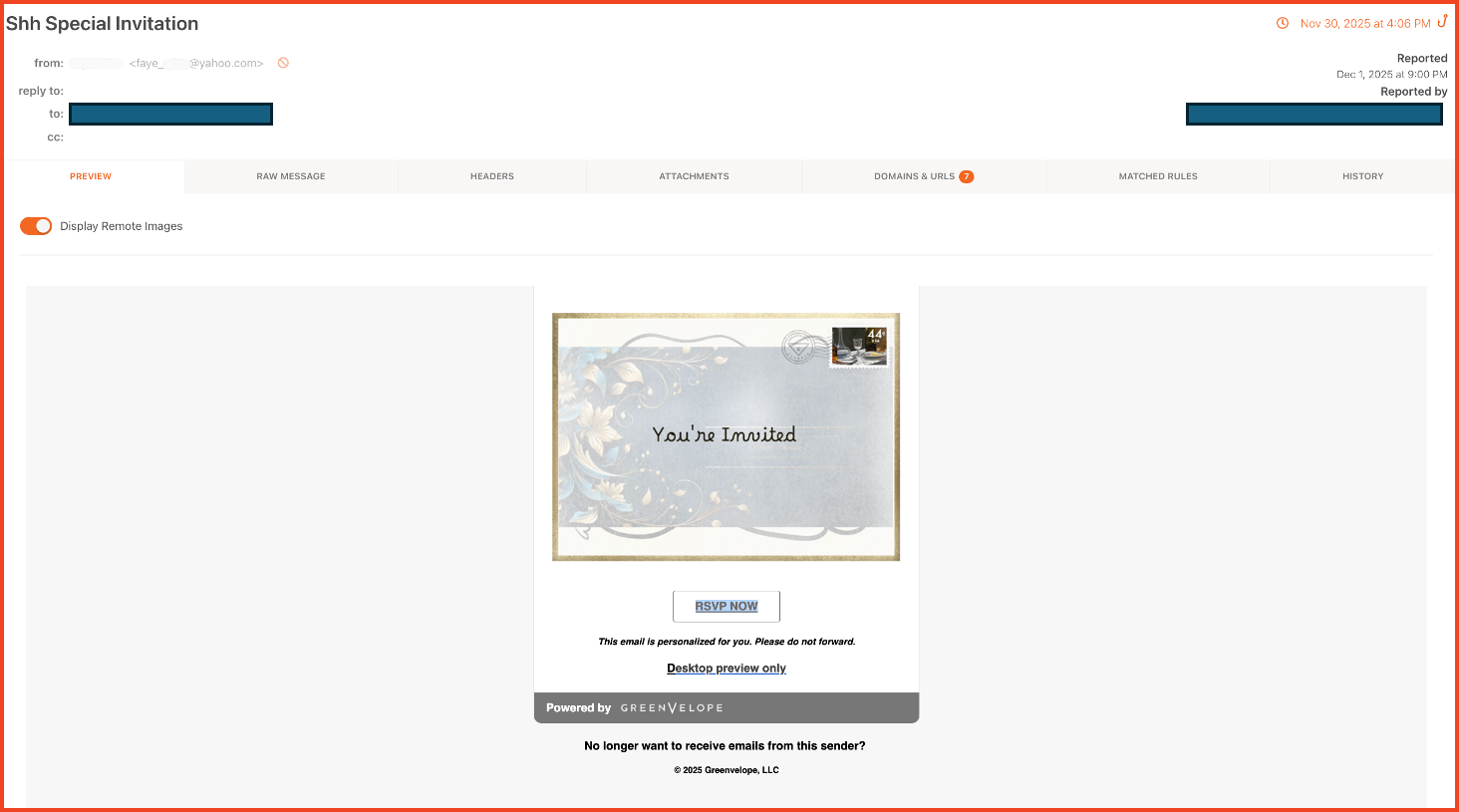
Instance of a faux GreenVelope invitation phishing electronic mail used to reap sufferer credentials in Wave 1 of the assault.
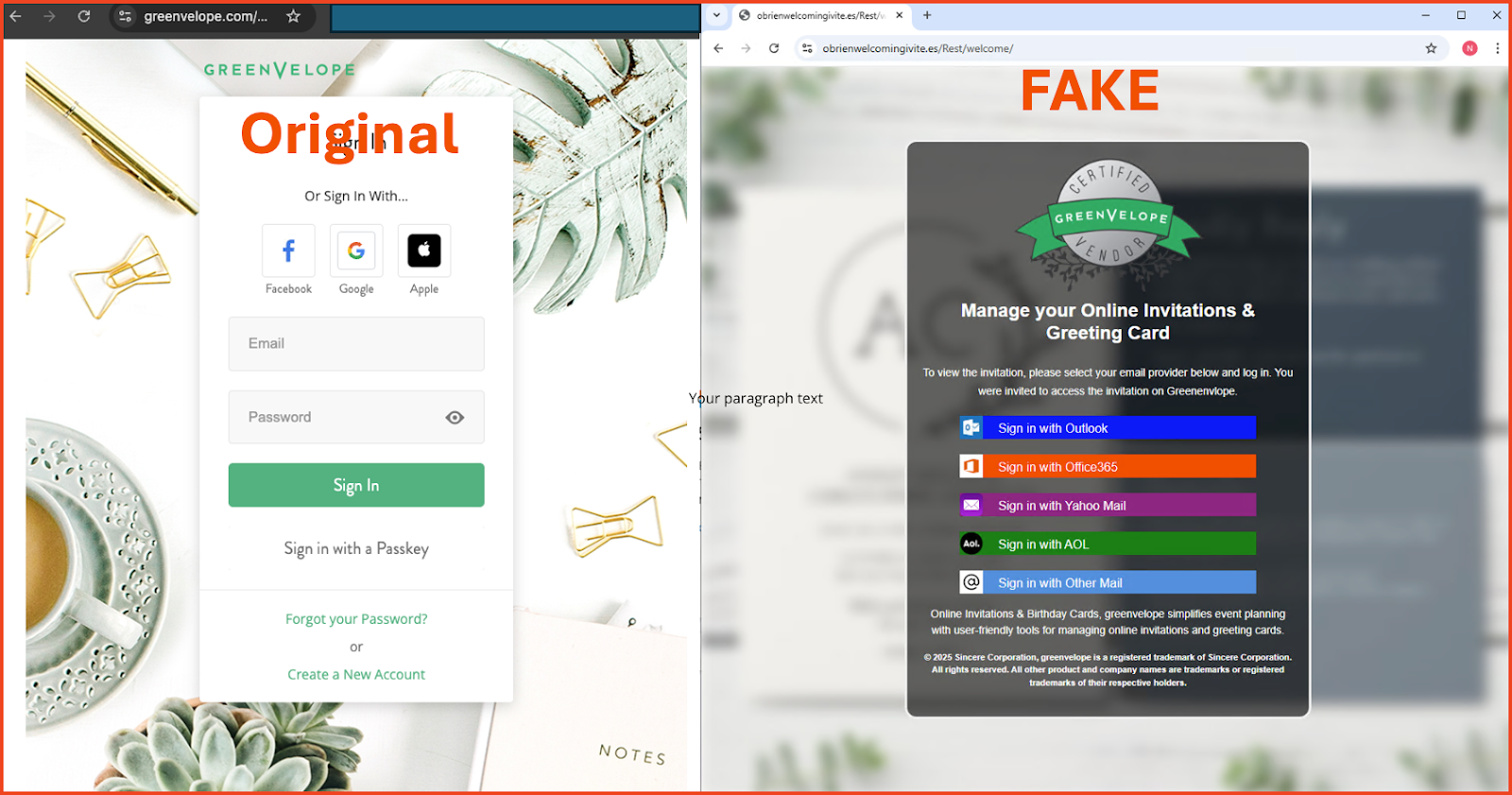
Instance of an authentic GreenVelope login web page in comparison with the spoofed login web page.
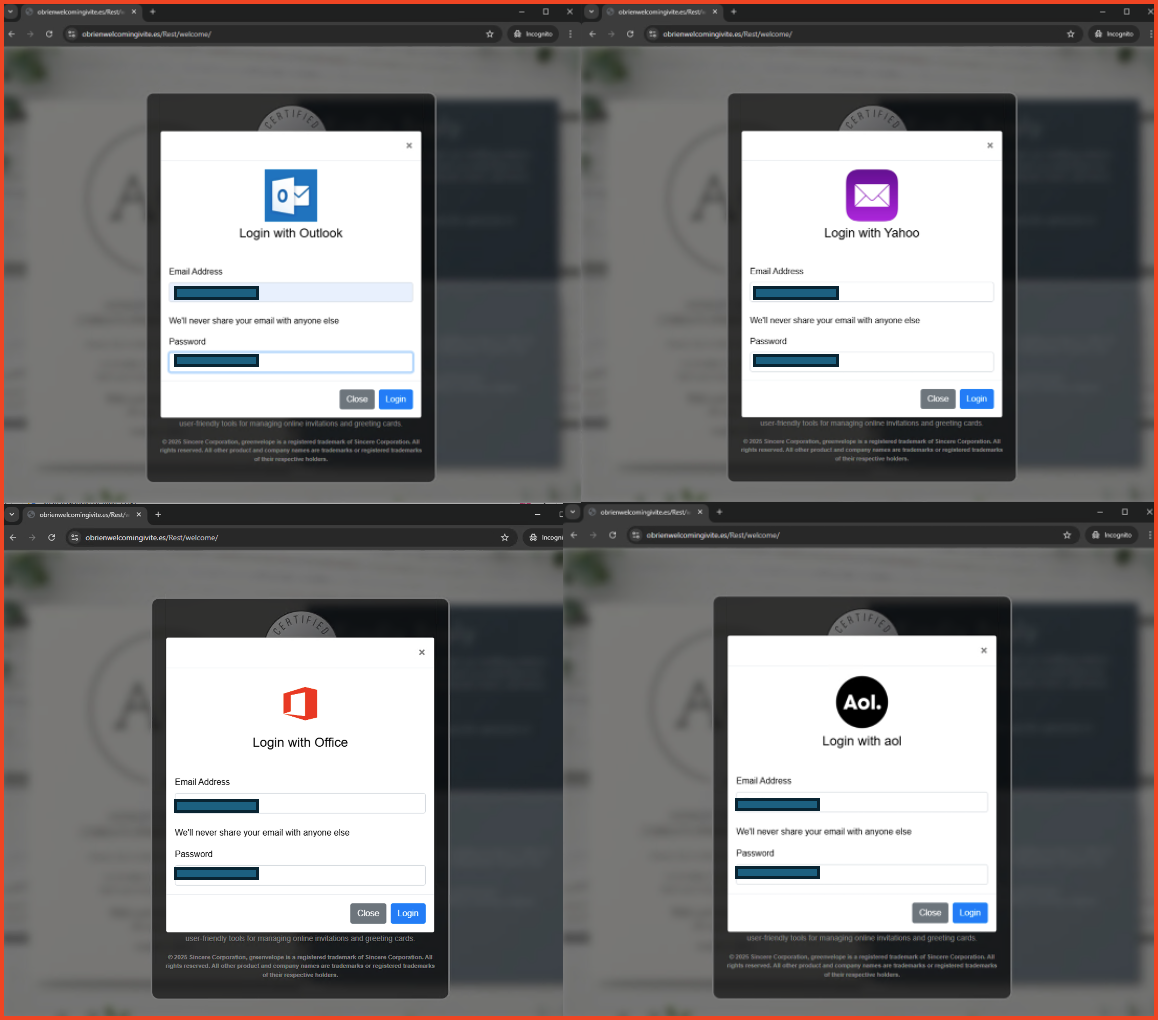
Grid of 4 phishing touchdown pages, every designed to reap consumer credentials by impersonating well-known electronic mail and expertise service suppliers.
The success of Wave 1, the theft of legitimate credentials, just isn’t the last word finish aim; it’s the enabling step for the highly-advanced Wave 2 of this assault technique.
Wave 2: RMM Deployment
For the attacker, a sound password just isn’t the tip aim—it’s the supply mechanism. As soon as credentials are secured, the menace actors generate professional RMM entry tokens. These tokens are then deployed in follow-on assaults by way of a file referred to as “GreenVelopeCard.exe” to ascertain persistent distant entry to sufferer programs.
How the Assault Works
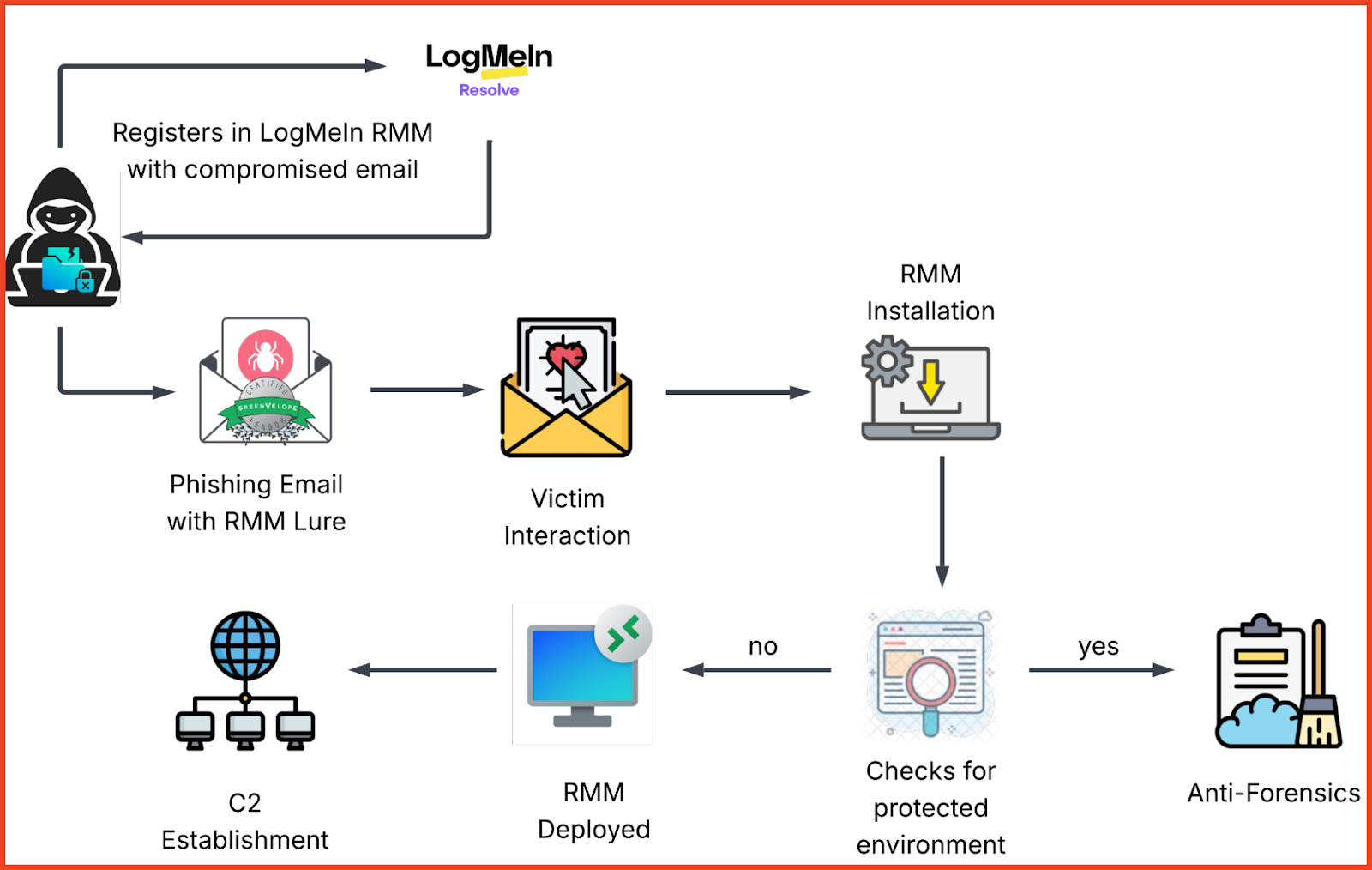
Full assault movement exhibiting the two-wave development from credential theft to RMM deployment and chronic entry.
Supply Methodology: Pretend GreenVelope Invitation Emails
Preliminary Payload: GreenVelopeCard.exe
Legit Signer: GoTo Applied sciences USA, LLC
RMM Instruments Deployed: GoTo Resolve, LogMeIn
Menace Stage: CRITICAL – Persistent distant entry with credential dumping capabilities
Using legitimately signed software program from a trusted vendor permits the malware to bypass many safety options that depend on signature-based detection.
Technical Evaluation
The GreenVelopeCard.exe file serves as the first orchestrator. Evaluation has revealed that it comprises a JSON configuration file with seven vital command line arguments that configure the RMM set up:
- Firm ID: Hyperlinks to an attacker-controlled GoTo Resolve firm account
- Set up ID: Registered with the attacker’s GoTo Resolve account
- WorkFolder: Makes use of the Firm ID as a folder title for group
- Surroundings: Connects to manufacturing servers:
- console[.]gotoresolve[.]com,
- Gadgets-iot[.]console[.]gotoresolve[.]com
- Software Kind: Allows unattended operation with full capabilities (it runs with out consumer interplay, operates silently within the background, and gives distant management)
- Language: Logs written in English
- Web site URL: Main Command and Management (C2) endpoint for the RMM set up
- Important Area: console[.]gotoresolve[.]com (official GoTo Resolve infrastructure)
- Subdomain: devices-iot (IoT/system administration console)
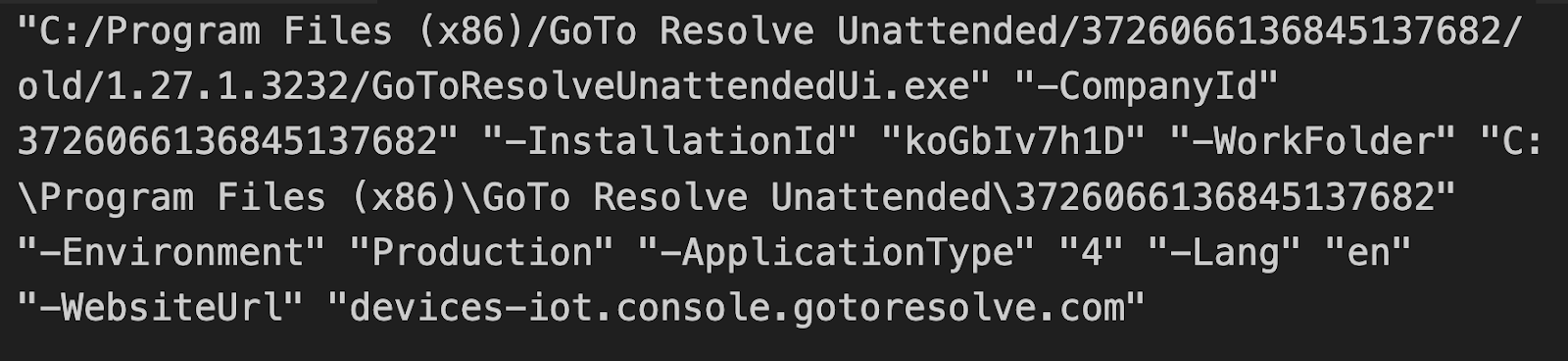
Seven command line arguments extracted from GreenVelopeCard.exe exhibiting attacker-controlled configuration parameters.
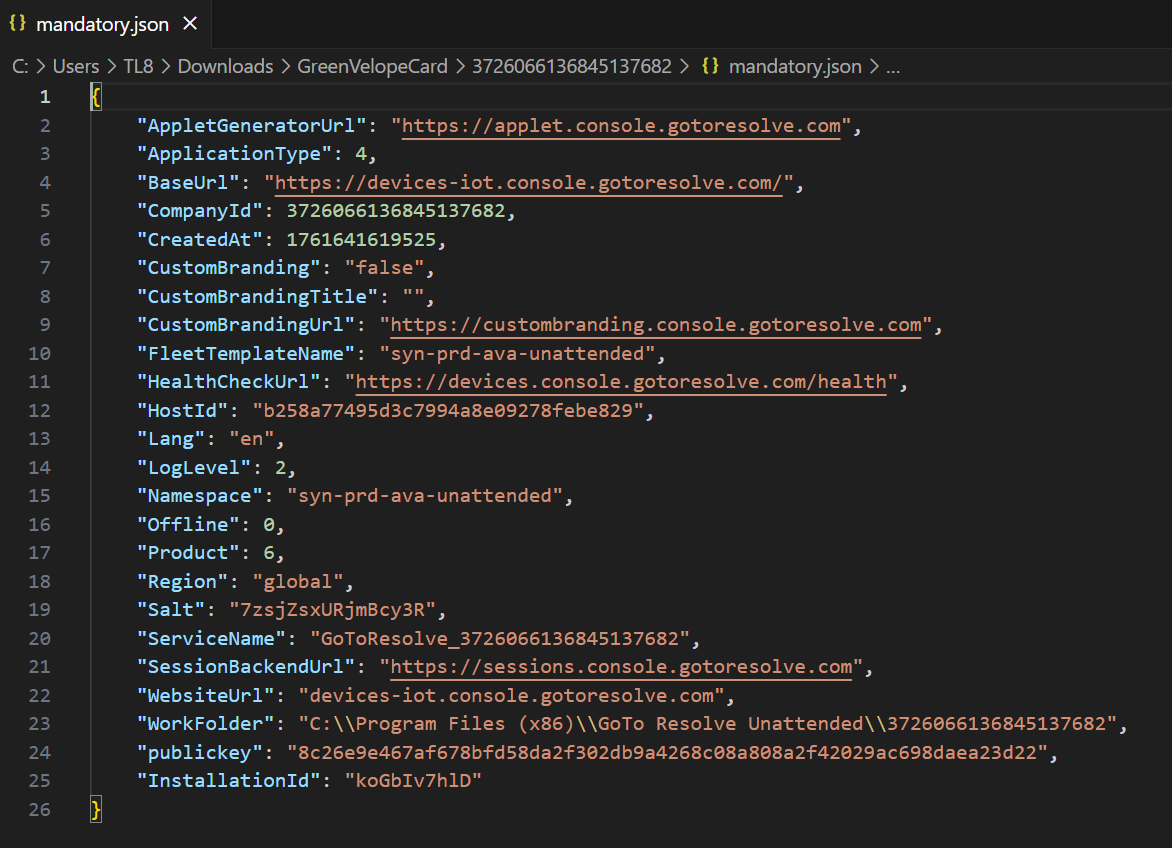
JSON configuration file embedded inside the GreenVelopeCard.exe file dropper.
In essence, this JSON file acts because the attacker’s pre-programmed deployment script. It may possibly inform the professional GoTo Resolve software to put in itself silently, connect with the attacker’s non-public community, and run with full, distant management capabilities. This all occurs with out the sufferer or most safety programs ever realizing a professional software is being criminally weaponized.
Privilege Escalation: Gaining the “Grasp Key”
As soon as the RMM software is on the system, the attackers transfer to safe SYSTEM-level privileges. That is the distinction between having a key to a single room and having the grasp key to your entire constructing.
- Registry Manipulation: The attackers alter Home windows service settings for GoTo Resolve, forcing it to run with unrestricted entry to system assets.
- COM API Backdoors: The marketing campaign establishes hidden scheduled duties through the Home windows COM API. These duties make sure the RMM software restarts even when a consumer manually kills the method.
- Service Abuse: By utilizing the Home windows Service Management Supervisor (companies.exe) to launch parts, the malware inherits the belief of the working system.
Community Communication: Hiding in Plain Sight
The simplest a part of this marketing campaign is its “Command and Management” (C2) technique. By utilizing official manufacturing infrastructure, the malicious site visitors is sort of indistinguishable from on a regular basis enterprise operations.
|
Endpoint |
Evasion Technique |
|
dumpster.console.gotoresolve.com |
Makes use of encrypted HTTPS on GoTo’s official manufacturing servers. |
|
dumpster.dev01-console.gotoresolve.com |
A secondary “improvement” channel used for redundancy. |
|
settings.cc |
A fallback area used to ship up to date configuration scripts. |
Turning Intelligence into Motion
Within the face of quickly evolving ways, safety groups can not afford a “wait and see” strategy to consumer schooling. Organizations should transfer shortly to counter these refined threats. Human Threat Administration (HRM) gives the framework to do that by dismantling the standard silos between menace analysis and consumer consciousness.
A HRM platform constantly synthesizes behavioral information, product telemetry, and real-time menace intelligence to generate extremely correct danger scores for every particular person consumer. This data-driven strategy permits for the platform to automate technical controls and hyper-personalized coaching to intervene and coach customers once they want it most.
The simplest technique to construct this protection is by reworking actual phishing assaults—just like the “Greenvelope” assault—into de-fanged phishing simulations. This may present extremely correct coaching that may equip customers to establish and report refined threats in real-time.
Defensive Measures: Strengthening Your Perimeter
To mitigate the danger of RMM-based assaults, safety groups ought to prioritize the next rapid actions:
- Hunt for offered Indicators of Compromise (IOCs) in your atmosphere
- Block recognized C2 domains on the community perimeter
- Monitor for unauthorized RMM installations and utilization patterns
Indicators of Compromise (IOCs)
The menace panorama evolves quickly. For probably the most present checklist of domains, hashes, and behavioral signatures associated to this marketing campaign, please confer with the most recent intelligence replace from KnowBe4 Menace Labs.
View the total IOC checklist on X:
https://x.com/Kb4Threatlabs/standing/1996210706258313663?s=20
For real-time updates and ongoing menace intelligence, comply with the KnowBe4 Menace Lab analysts on X: @Kb4Threatlabs

