The legacy area for Microsoft Stream was hijacked to point out a faux Amazon website selling a Thailand on line casino, inflicting all SharePoint websites with outdated embedded movies to show it as spam.
Microsoft Stream is an enterprise video streaming service that permits organizations to add and share movies in Microsoft 365 apps, equivalent to Groups and SharePoint.
Video content material hosted on Microsoft Stream was accessed or embedded by means of a portal at microsoftstream.com.
In September 2020, Microsoft introduced they had been deprecating the Microsoft Stream traditional service and transferring it into SharePoint.
Organizations had been informed to migrate their Microsoft Stream movies to the brand new platform by April 2024, when the service was retired.
Microsoft Streams traditional area hijacked
As we speak, the Microsoft Streams traditional area, microsoftstream.com, was hijacked to show a web site imitating Amazon that acts as a phishing web page for a Thai on-line on line casino, as proven beneath.
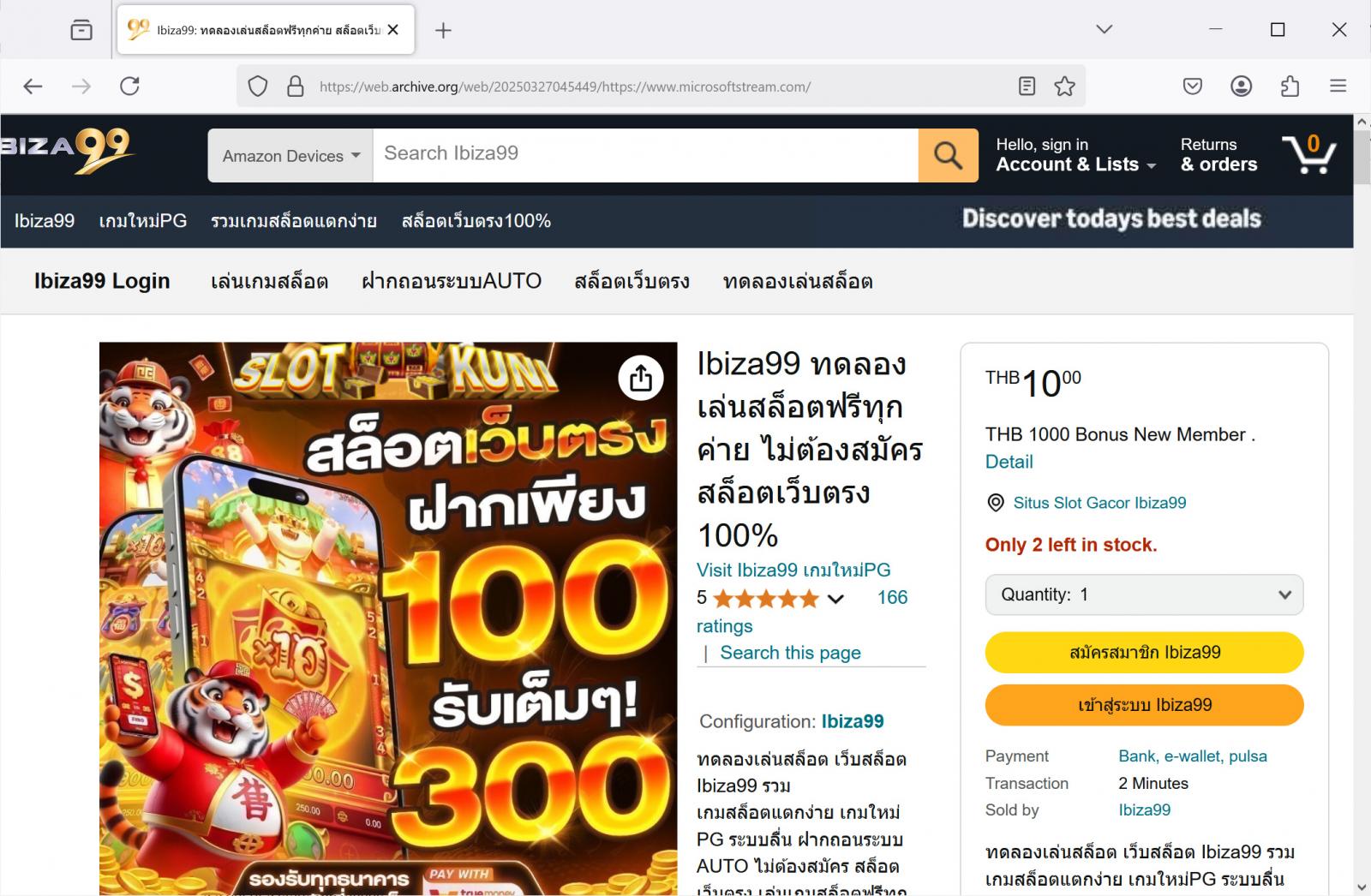
Supply: Archive.org
It’s unclear if the area was hijacked or DNS modified to point out the information website, however WHOIS information present {that a} change was made to the area on March 27, 2025.
Area Title: MICROSOFTSTREAM.COM
Registry Area ID: 2027086511_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.comlaude.com
Registrar URL: http://www.comlaude.com
Up to date Date: 2025-03-27T02:46:29Z
Creation Date: 2016-05-09T22:38:37Z
Registry Expiry Date: 2025-05-09T22:38:37Z
Registrar: Nom-iq Ltd. dba COM LAUDE
Registrar IANA ID: 470
Registrar Abuse Contact Electronic mail: abuse@comlaude.com
Registrar Abuse Contact Cellphone: +442074218250
Area Standing: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Area Standing: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Area Standing: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Title Server: NS1-04.AZURE-DNS.COM
Title Server: NS2-04.AZURE-DNS.NET
Title Server: NS3-04.AZURE-DNS.ORG
Title Server: NS4-04.AZURE-DNS.INFO
Because of the hijack, SharePoint servers that also had embedded movies from the traditional microsoftstream.com area, had been now seeing this spam web page in pages.
“This afternoon, a person reported a suspicious web site on our intranet, that’s utilizing microsoftstream.com. After some evaluation, it seems the area is at the moment redirecting to a sketchy web site signed by ‘Ibiza99’,” reported a SharePoint admin on Reddit.
“This is an fascinating one for you all. I simply acquired a name that our SharePoint website was exhibiting spam as an alternative of embedded movies. Attention-grabbing, I believed. I’m wondering how that might occur,” one other Reddit thread defined.
“So I jumped on to see the difficulty, website is utilizing embedded video from an aspx web page on the SharePoint format. It’s undoubtedly exhibiting spam.”
Earlier at the moment, the area was shut down once more, blocking the spam web page from showing in SharePoint.
“We’re conscious of those stories and have taken applicable motion to additional stop entry to impacted domains,” Microsoft informed BleepingComputer when requested in regards to the incident.
Nonetheless, Microsoft didn’t share additional details about how the area was hijacked.
Fortunately, the menace actors behind this hijack didn’t try to conduct a extra dangerous marketing campaign, equivalent to distributing malware by means of faux software program updates or different messages that will have been displayed on SharePoint servers.


