Hackers are utilizing a novel approach that mixes authentic workplace.com hyperlinks with Lively Listing Federation Companies (ADFS) to redirect customers to a phishing web page that steals Microsoft 365 logins.
The strategy lets attackers bypass conventional URL-based detection and the multi-factor authentication course of by leveraging a trusted area on Microsoft’s infrastructure for the preliminary redirect.
Legitimacy of a trusted redirect
Researchers at Push Safety, an organization that gives safety options towards identity-based assaults, analyzed a current marketing campaign that focused a number of of its prospects and redirected workers from a authentic outlook.workplace.com hyperlink to a phishing web site.
Whereas the phishing web page didn’t exhibit any particular components that will stop its detection, the supply technique utilized trusted infrastructure to evade triggering safety brokers.
Push Safety decided that the phishing assault began with the goal clicking a malicious sponsored hyperlink in Google search outcomes for Workplace 265 (doubtless a typo).
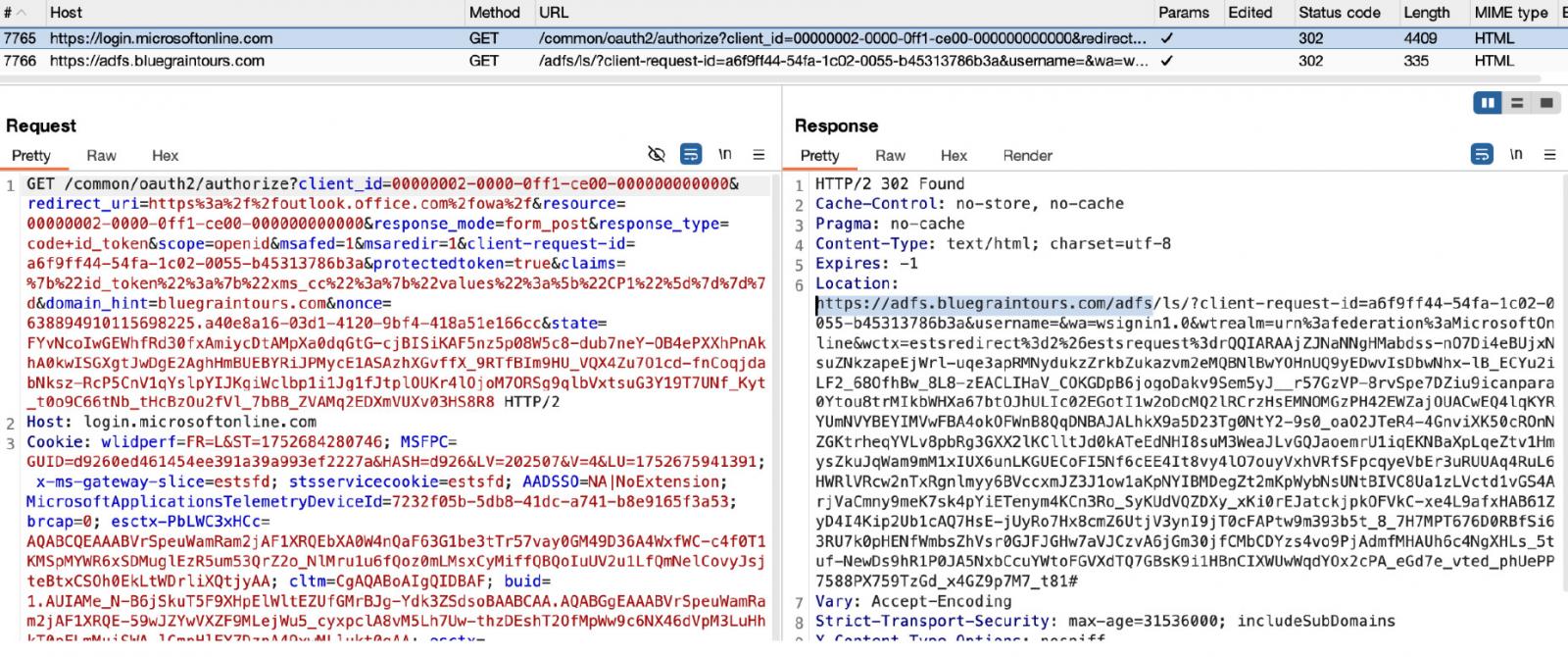
Clicking the malicious consequence would direct the goal to Microsoft’s Workplace, which in flip redirected to a different area, bluegraintours[.]com, that additional redirected to a phishing web page set as much as accumulate credentials.
At first look, attending to the malicious web page appeared to have occurred as a redirect from Microsoft’s workplace.com area with no phishing e-mail being concerned.
When investigating the incidents, Push Safety researchers found that “the attacker had arrange a customized Microsoft tenant with Lively Listing Federation Companies (ADFS) configured.”
ADFS is a single sign-on (SSO) answer from Microsoft that permits customers to entry a number of purposes, each inside and outdoors the company community, utilizing a single set of login credentials.
Though the service continues to be accessible on Home windows Server 2025 and there aren’t any official plans to deprecate it, Microsoft has been encouraging prospects emigrate to Azure Lively Listing (Azure AD) for id and entry administration (IAM).
By controlling a Microsoft tenant, the attacker was in a position to make use of ADFS to obtain authorization requests from the bluegraintours area, which acted as an IAM supplier, to enable authentication on the phishing web page.
supply: Push Safety
As a result of the bluegraintours web site is invisible to the goal throughout the redirect chain, the attacker crammed it with pretend weblog posts and ample particulars to make it seem authentic to automated scanners.
Additional evaluation of the assault revealed that the menace actor applied conditional loading restrictions that give entry to the phishing web page solely to targets deemed legitimate.
If a consumer doesn’t meet the situations, they’re routinely redirected to the authentic workplace.com web site, researchers say.
Jacques Louw, co-founder and Chief Product Officer at Push Safety, informed BleepingComputer that these assaults don’t seem to focus on a particular business or job roles, and could also be the results of a menace actor’s experimenting with new assault strategies.
“From what we have seen this seems to be a gaggle experimenting with novel strategies to get customers to click on extremely trusted hyperlinks to pretty normal phishing kits – in the identical vein as teams like Shiny Hunters and Scattered Spider have been seen doing” – Jacques Louw, co-founder and CPO at Push Safety
Microsoft ADFS has been utilized in phishing campaigns earlier than however attackers spoofed the focused group’s ADFS login web page to steal credentials.
To guard towards one of these assaults, Push Safety recommends a set of measures that embrace monitoring for ADFS redirects to malicious areas.
Because the investigated assault began from malvertising, the researchers additionally advise enterprises to examine for advert parameters in Google redirects to workplace.com, as this will reveal malicious domains or redirects to phishing pages.


