ESET researchers have recognized a number of samples of Linux backdoor, which we’ve named WolfsBane, that we attribute with excessive confidence to the Gelsemium superior persistent risk (APT) group. This China-aligned risk actor has a identified historical past relationship again to 2014 and till now, there have been no public reviews of Gelsemium utilizing Linux malware. Moreover, we found one other Linux backdoor, which we named FireWood. Nevertheless, we can not definitively hyperlink FireWood to different Gelsemium instruments, and its presence within the analyzed archives is perhaps coincidental. Thus, we attribute FireWood to Gelsemium with low confidence, contemplating it could possibly be a instrument shared amongst a number of China-aligned APT teams.
Probably the most notable samples we present in archives uploaded to VirusTotal are two backdoors resembling identified Home windows malware utilized by Gelsemium. WolfsBane is the Linux counterpart of Gelsevirine, whereas FireWood is linked to Challenge Wooden. We additionally found different instruments doubtlessly associated to Gelsemium’s actions. The objective of the backdoors and instruments found is cyberespionage focusing on delicate information comparable to system data, consumer credentials, and particular recordsdata and directories. These instruments are designed to keep up persistent entry and execute instructions stealthily, enabling extended intelligence gathering whereas evading detection.
The development of APT teams specializing in Linux malware is changing into extra noticeable. We consider this shift is because of enhancements in Home windows e mail and endpoint safety, such because the widespread use of endpoint detection and response (EDR) instruments and Microsoft’s determination to disable Visible Fundamental for Functions (VBA) macros by default. Consequently, risk actors are exploring new assault avenues, with a rising concentrate on exploiting vulnerabilities in internet-facing methods, most of which run on Linux.
On this blogpost, we offer technical evaluation of the Linux malware, primarily specializing in the 2 totally different backdoors.
Key factors of the blogpost:
- ESET researchers discovered archives with a number of Linux samples, containing two beforehand unknown backdoors.
- The primary backdoor, WolfsBane, is a Linux model of Gelsevirine, a Home windows backdoor utilized by Gelsemium.
- Its dropper is the equal of the Gelsemine dropper, and encompasses a hider based mostly on an open-source userland rootkit.
- The second backdoor, which we’ve named FireWood, is linked to Challenge Wooden. The Home windows model of the Challenge Wooden backdoor was beforehand utilized by the Gelsemium group in Operation TooHash.
- Alongside the backdoors, we discovered further instruments, primarily internet shells based mostly on publicly obtainable code.
Overview
In 2023, we discovered these samples in archives uploaded to VirusTotal from Taiwan, the Philippines, and Singapore, in all probability originating from an incident response on a compromised server. Gelsemium has beforehand focused entities in Jap Asia and the Center East.
The primary backdoor is part of a easy loading chain consisting of the dropper, launcher, and backdoor. We named this malware WolfsBane. As defined within the Attribution and connection and Technical evaluation sections, WolfsBane is a Linux equal of Gelsemium’s Gelsevirine backdoor and the WolfsBane dropper is analogous to the Gelsemine dropper. Our title for Gelsemium comes from one potential translation of the title we discovered within the report from VenusTech, who dubbed the group 狼毒草. It’s the title of a genus of flowering vegetation within the household Gelsemiaceae, and Gelsemium elegans is the species that accommodates poisonous compounds like Gelsemine, Gelsenicine, and Gelsevirine, which we selected as names for the three elements of this malware household. We beforehand analyzed Gelsevirine and Gelsemine in this white paper. A part of the analyzed WolfsBane assault chain can be a modified open-source userland rootkit, a kind of software program that exists within the consumer house of an working system and hides its actions.
The second backdoor, which we named FireWood, is linked to a backdoor tracked by ESET researchers underneath the title Challenge Wooden, beforehand analyzed within the Challenge Wooden part of this blogpost. We have now traced it again to 2005 and noticed it evolving into extra subtle variations.
The archives we analyzed additionally comprise a number of further instruments, principally webshells, that enable distant management to a consumer as soon as they’re put in on a compromised server, and easy utility instruments.
Attribution and connection
On this part, we clarify the similarities that led us to attribute the WolfsBane malware to the Gelsemium APT group and set up a connection between the FireWood backdoor and the Challenge Wooden malware.
WolfsBane hyperlinks to Home windows Gelsevirine
Primarily based on the next similarities, we assess that the WolfsBane backdoor is the Linux model of Gelsevirine. Subsequently, we attribute WolfsBane to the Gelsemium APT group with excessive confidence:
- Customized libraries for community communication: Each the Linux and Home windows variations load an embedded customized library for community communication, with a special library for every communication protocol used. The backdoor accesses the library’s capabilities by calling its create_seesion export/image; notably, the typo seesion is identical in each variations (as proven in Determine 1).
- Command execution mechanism: Each variations use the identical mechanism for executing instructions obtained from the C&C server. The backdoor creates a desk with hashes (derived from the command title) and corresponding tips to capabilities that deal with these instructions (Determine 2). We offer extra particulars within the Technical evaluation part.
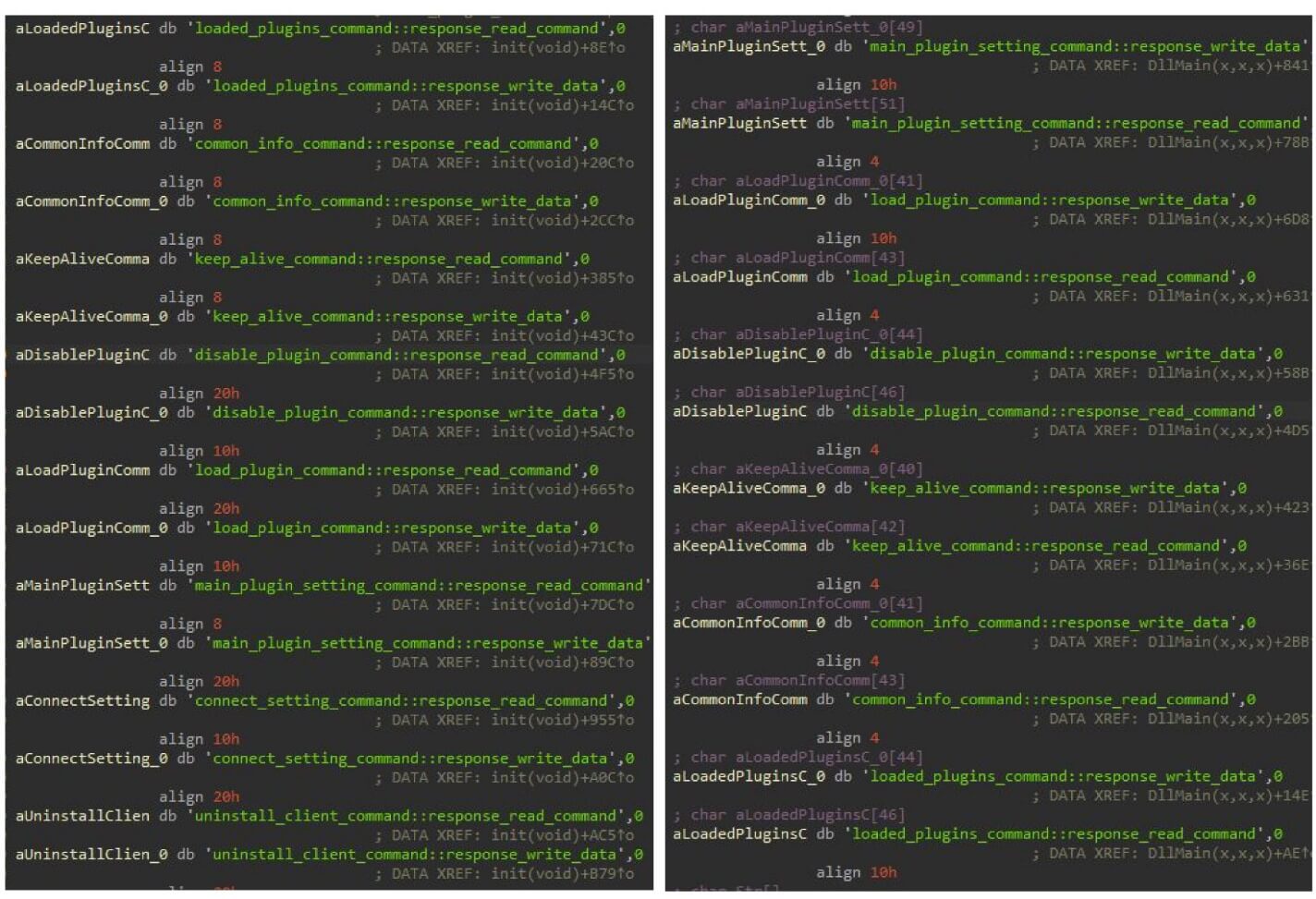
- Configuration construction: Each backdoors use a really related configuration construction. Whereas the Linux model has some omitted fields and a few further ones, many of the area names are constant. For instance, the worth of pluginkey discovered within the configuration is identical as in all Home windows Gelsevirine samples from 2019. Moreover, the controller_version values within the Linux model configuration match these within the Gelsevirine samples.
- Area Utilization: The area dsdsei[.]com, utilized by the Linux model, was beforehand flagged by ESET researchers as an indicator of compromise (IoC) related to the Gelsemium APT group.
FireWood connection to Challenge Wooden
We have now discovered code similarities between the FireWood pattern and the backdoor utilized in Operation TooHash (SHA-1: ED5342D9788392C6E854AAEFA655C4D3B4831B6B), as described by G DATA, who contemplate it to be part of the DirectsX rootkit. ESET researchers later named this backdoor Challenge Wooden. These similarities embrace:
- Naming conventions: Each use the “Wooden” string in naming. For instance, the FireWood backdoor configuration construction is referenced by the image WoodConf, and Win32 variations use the mutex title IMPROVING CLIENT Need Wooden To Exit?.
- File extensions: Each samples share particular filename extensions comparable to .k2 and .v2.
- TEA encryption algorithm: The implementation of the TEA encryption algorithm with a variable variety of rounds is identical in each samples.
- C&C communication strings: Each samples use the identical strings within the code accountable for C&C communications, XORed with the identical single-byte key (0x26).
- Networking code: The networking code in each samples may be very related.
Primarily based on these findings, we assess with excessive confidence that the FireWood backdoor is the Linux continuation of the Challenge Wooden backdoor. A connection between the FireWood backdoor to different Gelsemium instruments can’t be proved and its presence within the archives analyzed could possibly be coincidental. So, we make our attribution to Gelsemium solely with low confidence and acknowledge the chance that it’s a instrument shared by a number of Chinese language APT teams, maybe by way of a standard digital quartermaster as we’ve seen with different China-aligned teams.
Technical evaluation
The first archive was uploaded to VirusTotal on March 6th, 2023, from Taiwan. Subsequent archives have been uploaded additionally from the Philippines and Singapore. Primarily based on the folder construction (Determine 3), the goal was in all probability an Apache Tomcat webserver operating an unidentified Java internet utility.
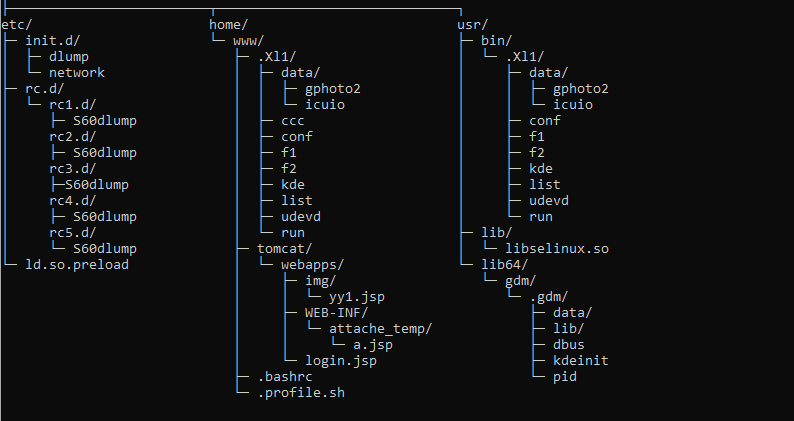
Preliminary entry
Though we lack concrete proof concerning the preliminary entry vector, the presence of a number of webshells (as proven in Desk 1 and described within the Webshells part) and the ways, strategies, and procedures (TTPs) utilized by the Gelsemium APT group lately, we conclude with medium confidence that the attackers exploited an unknown internet utility vulnerability to realize server entry.
Desk 1. Webshells present in analyzed archives
| SHA-1 | Filename | Description |
| 238C8E8EB7A732D85D8A |
login.jsp | Modified AntSword JSP webshell. |
| 9F7790524BD759373AB5 |
yy1.jsp | icesword webshell. |
| FD601A54BC622C041DF0 |
a.jsp | Obfuscated JSP webshell. |
Toolset
WolfsBane
WolfsBane elements and chain of execution are depicted in Determine 4.
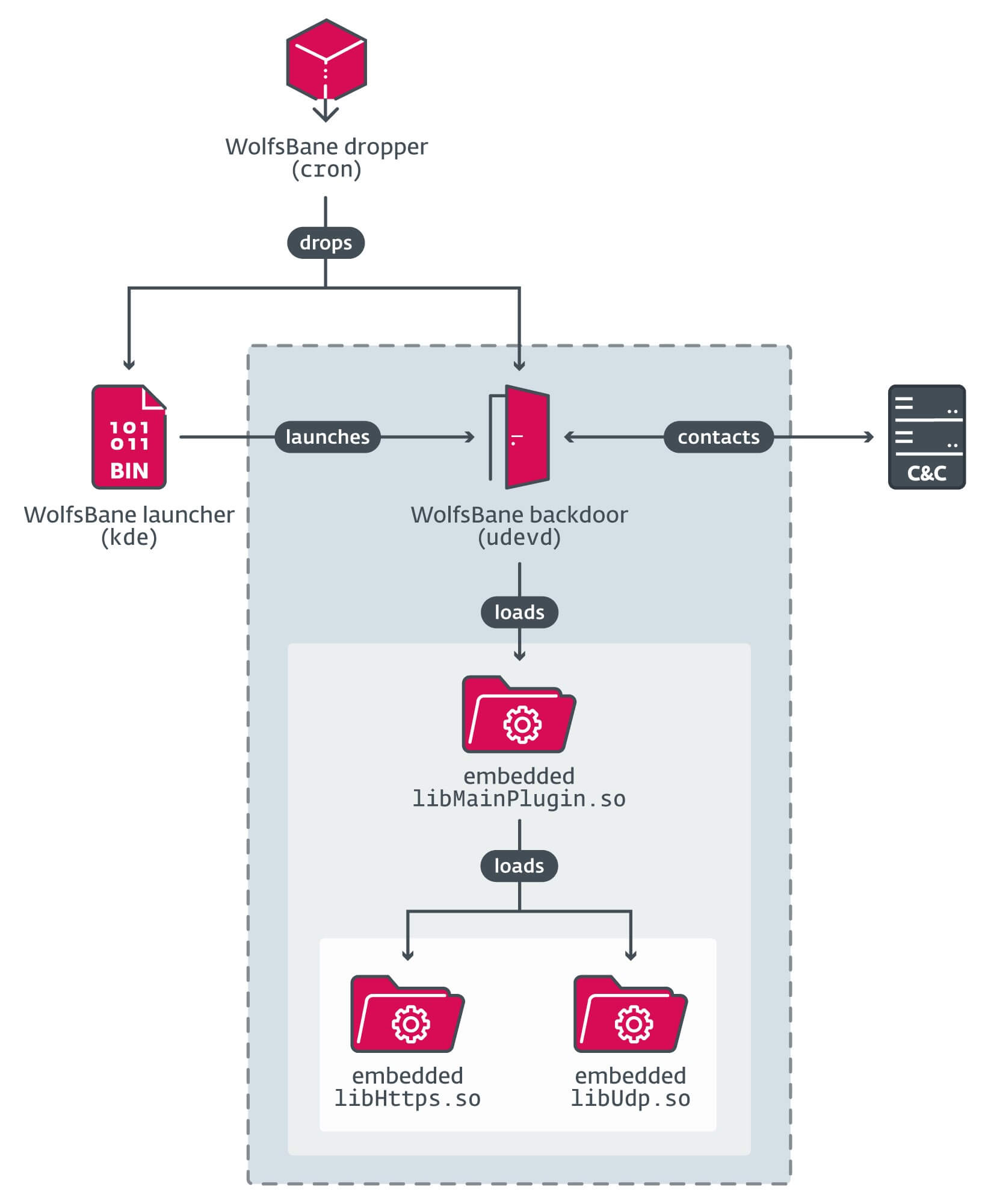
Stage 1: WolfsBane dropper
The dropper for WolfsBane was present in a file named cron, mimicking the respectable command scheduling instrument. Upon execution, it first locations the launcher and the first backdoor within the $HOME/.Xl1 hidden listing (word the usage of the letter l), created by the dropper. The listing is more than likely intentionally named to resemble X11 – a generally used folder title within the X Window System.
The dropper then establishes persistence based mostly on the system’s configuration and execution context:
If executed as root:
- Checks for the presence of the systemd suite.
- If systemd is current, writes the file /lib/systemd/system/display-managerd.service with the trail to the subsequent stage (WolfsBane launcher) because the ExecStart entry (see Determine 5). This ensures the launcher runs as a system service, as a result of .service recordsdata on this folder are parsed throughout system startup.
- Disables the SELinux safety module by altering the SELINUX entry within the SELinux configuration file from imposing to disabled.
[Unit]
Description=Show-Supervisor
[Service]
Sort=easy
ExecStart=
[Install]
WantedBy=multi-user.targetComment Determine 5. Content material of the display-managerd.service file
If systemd isn’t current, the dropper writes a easy bash script that executes the launcher (Determine 6), to a file named S60dlump into all rc[1-5].d startup folders.
#!/bin/bash
/usr/bin/.Xl1/kdeDetermine 6. Script executing WolfsBane launcher
If executed as an unprivileged consumer on a Debian-based system, it:
- writes an identical bash script to the profile.sh file, and
- provides the command /house/www/.profile.sh 2>/dev/null to .bashrc and .profile recordsdata within the consumer’s house folder, guaranteeing that the Wolfsbane launcher begins routinely after the sufferer logs in.
For different Linux distributions it creates the identical profile.sh file however provides its path solely to .bashrc.
Moreover, if the dropper is executed with root privileges, it drops the WolfsBane Hider rootkit as /usr/lib/libselinux.so and provides this command to /and many others/ld.so.preload, guaranteeing that the rootkit library hundreds into all processes.
Lastly, the dropper removes itself from the disk and executes the subsequent stage – the launcher.
Stage 2: WolfsBane launcher
A small binary named kde is used to keep up persistence, cleverly disguised as a respectable KDE desktop element to keep away from detection and preserve persistence. No matter institution methodology, the intention is to execute this binary, whose predominant operate is to parse its embedded configuration and provoke the subsequent stage – the WolfsBane backdoor – from the desired file within the configuration.
Stage 3: WolfsBane backdoor
The WolfsBane backdoor, saved in a file named udevd, begins by loading an embedded library and calling its main_session export, which accommodates the principle backdoor functionalities. This library, named by its authors as libMainPlugin.so, is analogous to the MainPlugin.dll used within the Home windows model of the Gelsevirine backdoor.
Much like its Home windows model, the WolfsBane backdoor makes use of different embedded libraries for community communication. Within the samples we’ve collected, they’re named libUdp.so and libHttps.so, and each export the image create_seesion (the spelling mistake is precisely the identical as within the Home windows model of the Gelsevirine TCP module). These shared libraries present C&C communications through UDP and HTTPS protocols, respectively.
The backdoor encrypts the libMainPlugin.so library utilizing the RC4 algorithm (with the important thing obtained from the pluginkey worth within the configuration) and saves it to
The WolfsBane backdoor makes use of an identical method to its Home windows counterpart for executing instructions obtained from its C&C server.
WolfsBane Hider rootkit
WolfsBane backdoor makes use of a modified open-source BEURK userland rootkit to cover its actions. Positioned in /usr/lib/libselinux.so, this rootkit abuses the working system’s preload mechanism to load into new processes earlier than different libraries by including its path to the /and many others/ld.so.preload file, thus enabling its capabilities to hook the unique ones.
The WolfsBane Hider rootkit hooks many fundamental customary C library capabilities comparable to open, stat, readdir, and entry. Whereas these hooked capabilities invoke the unique ones, they filter out any outcomes associated to the WolfsBane malware. Not like the unique BEURK rootkit, which makes use of an embedded configuration file for filtering, the WolfsBane builders retained the default configuration however modified the supply code to exclude data associated to the hardcoded filenames of the malware executables udevd and kde. Moreover, the unique BEURK rootkit’s community traffic-hiding options are absent.
FireWood backdoor
The FireWood backdoor, in a file named dbus, is the Linux OS continuation of the Challenge Wooden malware, as famous within the Attribution and connection part. The analyzed code means that the file usbdev.ko is a kernel driver module working as a rootkit to cover processes. The FireWood backdoor communicates with the kernel drivers utilizing the Netlink protocol.
FireWood makes use of a configuration file named kdeinit that’s XOR encrypted with the single-byte key 0x26. The configuration file’s construction is detailed in Desk 2.
Desk 2. Chosen offsets and their corresponding values from the FireWood backdoor configuration file
| Offset | Worth | That means |
| 0x00 | 20190531110402 | Unknown timestamp. |
| 0x28 | AAAAAAAAAA | Placeholder for backdoor working listing. |
| 0x3C | 0.0.0.0 | C&C IP deal with (if 0.0.0.0, the backdoor makes use of the C&C area). |
| 0x66 | asidomain[.]com | C&C area. |
| 0xCC | [scsi_eh_7] | Spoofed course of title. |
| 0x164 | 0x072BA1E6 | TEA encryption key. |
| 0x1E0 | 4 | Connection day (backdoor connects each fourth day of the month). |
| 0x1E4 | 5 | Delay time. |
| 0x1E8 | 0x0474 | Connection time (in minutes). |
FireWood renames its course of based mostly on the worth within the configuration.
To determine persistence on the system, it creates a file named /.config/autostart/gnome-control.desktop. Throughout startup, all recordsdata with a .desktop extension within the /.config/autostart/ listing are parsed, and any instructions listed within the Exec entry are executed. The contents of the gnome-control.desktop file may be seen in Determine 7.
[Desktop Entry]
Sort=Software
Exec=
Hidden=false
NoDisplay=false
X-GNOME-Autostart-enabled=true
Title[en_US]=gnome-calculator
Title=gnome-control
Remark[en_US]= Determine 7. Contents of the gnome-control.desktop file used for persistence by the FireWood backdoor
FireWood communicates with its C&C server through TCP, as laid out in its configuration. All information is encrypted utilizing the TEA encryption algorithm with a variable variety of rounds. The encryption key and variety of rounds are offered within the FireWood configuration file, as proven again in Desk 2.
The construction of despatched and obtained messages is proven in Determine 8. The result of executing a command varies relying on the command kind, however usually, 0x10181 signifies success, whereas 0x10180 denotes an error.
struct information{
DWORD commandID_or_return_code_value ;
BYTE information [];
}Determine 8. Knowledge. construction for C&C communications utilized by FireWood backdoor
This backdoor is able to executing a number of instructions, as described in Desk 3.
Desk 3. FireWood backdoor instructions
| Command ID | Description |
| 0x105 | Obtain an executable file from the C&C to |
| 0x110 | Execute a shell command utilizing the popen operate. |
| 0x111 | Change connection time worth within the configuration. |
| 0x112 | Cover a course of utilizing the usbdev.ko kernel module. |
| 0x113 | Change delay time in configuration. |
| 0x114 | Change connection day worth in configuration. |
| 0x132 | Clear up and exit. |
| 0x181 | Checklist contents of the desired listing. |
| 0x182 | Exfiltrate specified file to C&C server. |
| 0x183 | Delete specified file. |
| 0x184 | Rename specified file. |
| 0x185 | Execute specified file utilizing the system operate. |
| 0x186 | Obtain file from C&C server. |
| 0x189 | Exfiltrate specified folder to C&C server. |
| 0x193 | Load specified kernel module or shared library. |
| 0x194 | Unload specified kernel module or shared library. |
| 0x19F | Modify specified file timestamp. |
| 0x200 | Delete specified listing. |
| 0x201 | Learn content material of the desired file and ship it to the C&C server. |
| 0x1018F | Seek for the desired file within the folder outlined within the command. |
Different instruments
We found two further instruments within the archives, which could possibly be associated to Gelsemium exercise: the SSH password stealer and a small privilege escalation instrument.
The SSH password stealer is an SSH consumer based mostly on the open-source OpenSSH software program, modified to gather customers’ SSH credentials vital for authenticating the consumer’s entry to a server. The adversaries changed the unique SSH consumer binary in /usr/bin/ssh with a trojanized model. Whereas it capabilities as a traditional SSH consumer, it saves all login information within the format
The privilege escalation instrument is a small binary, named ccc, that simply escalates consumer privileges by setting UID and GUID of the execution context to 0 and executes a program at a path obtained as an argument. To carry out this method, the consumer will need to have root privileges so as to add SUID permission to this executable upfront, making it a instrument for sustaining privileges relatively than for acquiring them.
Webshells
The login.jsp is a modified AntSword JSP webshell that executes Java bytecode from attackers. The payload, a Java class file, is base64 encoded within the tiger parameter of an HTTP POST request. The unique webshell additionally helps distant terminal, file operations, and database operations.
The yy1.jsp webshell, which we recognized as icesword JSP, is sourced from web boards, primarily these in Chinese language. The icesword JSP webshell encompasses a full graphical consumer interface inside its server-side code, permitting it to render a GUI within the attacker’s browser. It’s not obfuscated and collects system data, executes system instructions, and performs file operations. It additionally connects to SQL databases on the compromised host and executes SQL queries.
The a.jsp webshell, just like login.jsp however obfuscated, carries a binary Java payload that’s AES encrypted with the important thing 6438B9BD2AB3C40A after which base64 encoded. The payload is offered within the Tas9er parameter. The obfuscation consists of rubbish feedback, u-escaped Unicode strings (that are made tougher to learn), and random string variables and performance names. The end result, base64 encoded and inserted into the string 1F2551A37335B564
Conclusion
This report describes the Linux malware toolset and its connections with Home windows malware samples utilized by the Gelsemium APT group. We have now targeted on capabilities of WolfsBane and FireWood backdoors, and analyzed WolfsBane execution chain and its utilization of the userland rootkit. That is the primary public report documenting Gelsemium’s use of Linux malware, marking a notable shift of their operational technique.
The development of malware shifting in direction of Linux methods appears to be on the rise within the APT ecosystem. From our perspective, this improvement may be attributed to a number of developments in e mail and endpoint safety. The ever-increasing adoption of EDR options, together with Microsoft’s default technique of disabling VBA macros, are resulting in a state of affairs the place adversaries are being compelled to search for different potential avenues of assault.
Consequently, the vulnerabilities current in internet-facing infrastructure, notably these methods which are Linux-based, have gotten more and more focused. Which means these Linux methods have gotten the brand new most popular targets for these adversaries.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides personal APT intelligence reviews and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete checklist of indicators of compromise (IoCs) and samples may be present in our GitHub repository.
Information
| SHA-1 | Filename | Detection | Description |
| 0FEF89711DA11C550D39 |
dbus |
Linux/Agent.WF | FireWood backdoor. |
| 44947903B2BC760AC2E7 |
libselinux.so |
Linux/Rootkit.Agent.EC | WolfsBane Hider rootkit. |
| 0AB53321BB9699D354A0 |
udevd |
Linux/Agent.WF | WolfsBane backdoor. |
| 8532ECA04C0F58172D80 |
kde |
Linux/Agent.WF | WolfsBane launcher. |
| B2A14E77C96640914399 |
cron |
Linux/Agent.WF | WolfsBane dropper. |
| 209C4994A42AF7832F52 |
ccc |
Linux/Agent.WF | Privilege escalation helper instrument. |
| F43D4D46BAE9AD963C2E |
ssh |
Linux/SSHDoor.IC | Trojanized SSH consumer. |
| FD601A54BC622C041DF0 |
a.jsp |
Java/Agent.BP | JSP webshell. |
| 9F7790524BD759373AB5 |
yy1.jsp |
Java/JSP.J | icesword webshell. |
| 238C8E8EB7A732D85D8A |
login.jsp |
Java/Webshell.AM | Modified AntSword JSP webshell. |
| F1DF0C5A74C9885CB593 |
virus.tgz |
Linux/Agent.WF | VirusTotal archive. |
| B3DFB40336C2F17EC740 |
virus-b.tgz |
Linux/Agent.WF | VirusTotal archive. |
| 85528EAC10090AE743BC |
CHINA-APT-Trojan.zip |
Java/Agent.BP | VirusTotal archive. |
| CDBBB6617D8937D17A1A |
CHINA-APT-Trojan.zip |
Linux/Rootkit.Agent.EC | VirusTotal archive. |
| 843D6B0054D066845628 |
CHINA-APT-Trojan.zip |
Linux/Rootkit.Agent.EC | VirusTotal archive. |
| BED9EFB245FAC8CFFF83 |
Xl1.zip |
Linux/Rootkit.Agent.EC | VirusTotal archive. |
| 600C59733444BC8A5F71 |
CHINA-APT-Trojan.zip |
Linux/Rootkit.Agent.EC | VirusTotal archive. |
| 72DB8D1E3472150C1BE9 |
virus.tgz |
Linux/Agent.WF | VirusTotal archive. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| N/A | dsdsei[.]com | N/A | 2020-08-16 | WolfsBane backdoor C&C server. |
| N/A | asidomain[.]com | N/A | 2022-01-26 | FireWood backdoor C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Useful resource Improvement |
Purchase Infrastructure: Domains |
Gelsemium has registered domains by way of business suppliers. |
|
|
Purchase Infrastructure: Server |
Gelsemium more than likely acquires VPS from business suppliers. |
||
|
Develop Capabilities: Malware |
Gelsemium develops its personal customized malware. |
||
|
Execution |
Command-Line Interface: Unix Shell |
Gelsemium malware is able to executing Linux shell instructions. |
|
|
Persistence |
Boot or Logon Initialization Scripts: RC Scripts |
The WolfsBane launcher stays persistent on the system through the use of RC startup scripts. |
|
|
Create or Modify System Course of: Systemd Service |
The WolfsBane dropper can create a brand new system service for persistence. |
||
|
Hijack Execution Move: Dynamic Linker Hijacking |
The WolfsBane Hider rootkit abuses the ld.so.preload preload approach. |
||
|
Boot or Logon Autostart Execution: XDG Autostart Entries |
The FireWood backdoor persists on the system by creating the gnome-control.desktop autostart file. |
||
|
Privilege Escalation |
Occasion Triggered Execution: .bash_profile and .bashrc |
The WolfsBane dropper tampers with numerous shell configuration recordsdata to realize persistence. |
|
|
Abuse Elevation Management Mechanism: Setuid and Setgid |
Gelsemium makes use of a easy instrument abusing setuid and setguid for retaining escalated privileges. |
||
|
Protection Evasion |
Indicator Elimination: File Deletion |
The WolfsBane dropper removes itself. |
|
|
Indicator Elimination: Timestomp |
The FireWood backdoor has a command for modifying the MAC time of recordsdata. |
||
|
Indicator Elimination: Clear Persistence |
The WolfsBane dropper removes itself from disk. |
||
|
Cover Artifacts: Hidden Information and Directories |
Each the WolfsBane and FireWood backdoors are situated/put in in hidden folders. |
||
|
File Permissions Modification: Linux and Mac File and Listing Permissions Modification |
The WolfsBane dropper makes use of Linux chmod instructions to change permissions of dropped executables. |
||
|
Obfuscated Information or Info: Embedded Payloads |
The WolfsBane dropper has all its payloads compressed and embedded. |
||
|
Rootkit |
Each WolfsBane and FireWood malware make the most of rootkits for evasion. |
||
|
Masquerading: Match Authentic Title or Location |
Gelsemium typically names its malware to match respectable recordsdata and folders. |
||
|
Discovery |
System Info Discovery |
The WolfsBane dropper enumerates system data. |
|
|
File and Listing Discovery |
The FireWood backdoor is able to looking within the machine file system for specified recordsdata and folders. |
||
|
Assortment |
Enter Seize |
The SSH password stealer captures consumer credentials. |
|
|
Exfiltration |
Exfiltration Over C2 Channel |
The FireWood backdoor exfiltrates collected information using C&C communications. |


