ESET Analysis, Risk Studies
An outline of the actions of chosen APT teams investigated and analyzed by ESET Analysis in Q2 2024 and Q3 2024
07 Nov 2024
•
,
3 min. learn

ESET APT Exercise Report Q2 2024–Q3 2024 summarizes notable actions of chosen superior persistent menace (APT) teams that had been documented by ESET researchers from April 2024 till the tip of September 2024. The highlighted operations are consultant of the broader panorama of threats we investigated throughout this era, illustrating the important thing tendencies and developments, and comprise solely a fraction of the cybersecurity intelligence information offered to prospects of ESET’s non-public APT reviews.
Through the monitored interval, we noticed a notable enlargement in concentrating on by China-aligned MirrorFace. Usually targeted on Japanese entities, it prolonged its operations to incorporate a diplomatic group within the European Union (EU) for the primary time whereas persevering with to prioritize its Japanese targets. Moreover, China-aligned APT teams have been relying more and more on the open-source and multiplatform SoftEther VPN to take care of entry to victims’ networks. We detected intensive use of SoftEther VPN by Flax Storm, noticed Webworm switching from its full-featured backdoor to utilizing the SoftEther VPN Bridge on machines of governmental organizations within the EU, and observed GALLIUM deploying SoftEther VPN servers at telecommunications operators in Africa.
We additionally noticed indications that Iran-aligned teams could be leveraging their cybercapabilities to assist diplomatic espionage and, doubtlessly, kinetic operations. These teams compromised a number of monetary providers corporations in Africa – a continent geopolitically vital to Iran; performed cyberespionage in opposition to Iraq and Azerbaijan, neighboring nations with which Iran has advanced relationships; and elevated their curiosity within the transportation sector in Israel. Regardless of this seemingly slim geographical concentrating on, Iran-aligned teams maintained a worldwide focus, additionally pursuing diplomatic envoys in France and academic organizations in the USA.
North Korea-aligned menace actors endured in advancing the targets of their regime, which has been accused by the United Nations and South Korea of stealing funds – each conventional currencies and cryptocurrencies – to assist its weapons of mass destruction packages. These teams continued their assaults on protection and aerospace firms in Europe and the US, in addition to concentrating on cryptocurrency builders, suppose tanks, and NGOs. One such group, Kimsuky, started abusing Microsoft Administration Console information, that are usually utilized by system directors however can execute any Home windows command. Moreover, a number of North Korea-aligned teams continuously misused standard cloud-based providers, together with Google Drive, Microsoft OneDrive, Dropbox, Yandex Disk, pCloud, GitHub, and Bitbucket. For the primary time, we noticed an APT group – particularly ScarCruft – abusing Zoho cloud providers.
We detected Russia-aligned cyberespionage teams continuously concentrating on webmail servers corresponding to Roundcube and Zimbra, often with spearphishing emails that set off identified XSS vulnerabilities. Apart from Sednit concentrating on governmental, tutorial, and defense-related entities worldwide, we recognized one other Russia-aligned group, which we named GreenCube, stealing electronic mail messages by way of XSS vulnerabilities in Roundcube. Different Russia-aligned teams continued to deal with Ukraine, with Gamaredon deploying massive spearphishing campaigns whereas transforming its instruments utilizing and abusing the Telegram and Sign messaging apps. Sandworm utilized its new Home windows backdoor, which we named WrongSens, and its superior Linux malware: LOADGRIP and BIASBOAT. Moreover, we detected Operation Texonto, a disinformation and psychological operation primarily geared toward demoralizing Ukrainians, additionally concentrating on Russian dissidents. We additionally analyzed the general public hack-and-leak of the Polish Anti-Doping Company, which we imagine was compromised by an preliminary entry dealer who then shared entry with the Belarus-aligned FrostyNeighbor APT group, the entity behind cyber-enabled disinformation campaigns crucial of the North Atlantic Alliance. Lastly, from analyzing an exploit discovered within the wild, we found a distant code execution vulnerability in WPS Workplace for Home windows. We attribute the assault leveraging the exploit to the South Korea-aligned APT-C-60 group.
Malicious actions described in ESET APT Exercise Report Q2 2024–Q3 2024 are detected by ESET merchandise; shared intelligence is primarily based on proprietary ESET telemetry information and has been verified by ESET researchers.
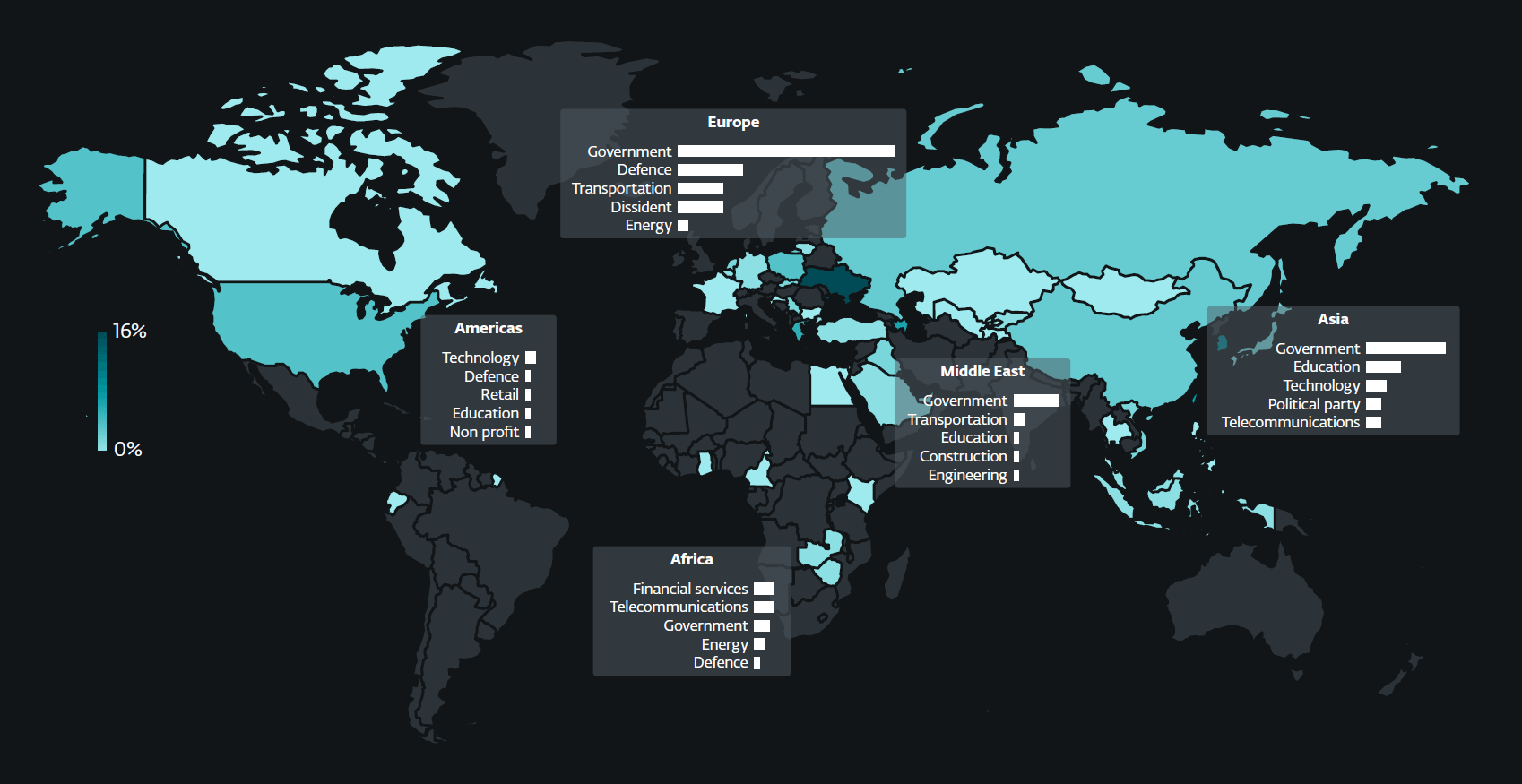
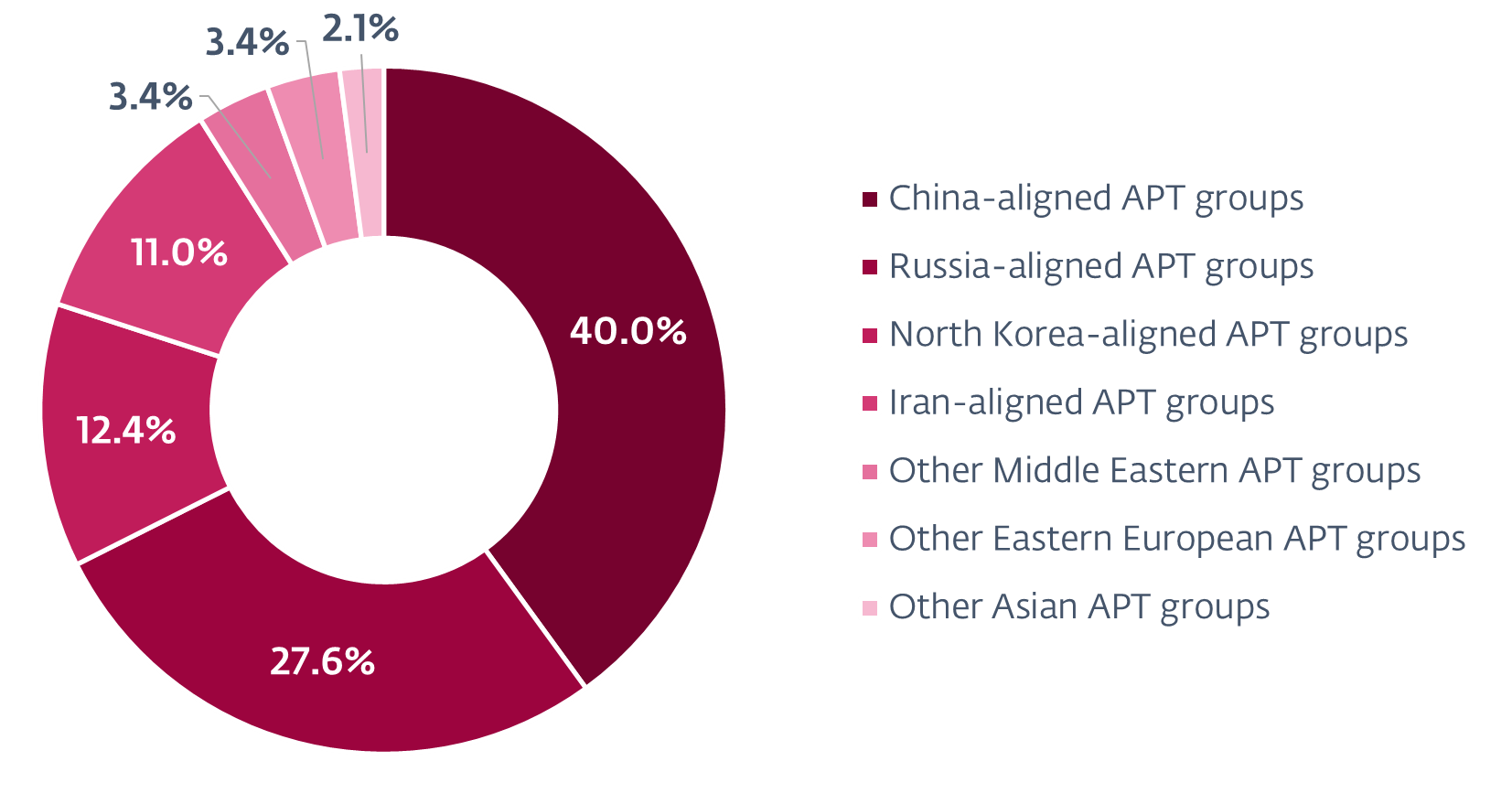
ESET APT Exercise Studies comprise solely a fraction of the cybersecurity intelligence information offered in ESET APT Studies PREMIUM. For extra info, go to the ESET Risk Intelligence web site.
Comply with ESET analysis on Twitter for normal updates on key tendencies and prime threats.

