Preliminary entry dealer Storm-0249 has developed from a mass phishing operation into a complicated menace actor weaponizing professional Endpoint Detection and Response (EDR) processes by way of sideloading strategies to hide malicious exercise as routine safety operations.
This represents a major escalation within the group’s capabilities and poses a crucial threat to organizations counting on conventional protection mechanisms.
ReliaQuest researchers, in collaboration with SentinelOne, have documented how Storm-0249 exploits trusted signed executables particularly SentinelOne’s SentinelAgentWorker.exe to execute malicious payloads whereas evading detection.
The strategies noticed are readily adaptable to different EDR platforms, making this a cross-industry menace requiring fast consideration from safety groups.
Storm-0249’s current assault methodology begins with ClickFix assault, a social engineering approach that manipulates customers into executing encoded instructions through the Home windows Run dialog. As soon as preliminary entry is established, the assault unfolds by way of three coordinated phases.
The primary part leverages curl.exe, a professional built-in Home windows utility generally utilized by IT directors for downloading updates and testing APIs.
As a result of curl.exe not often triggers safety alerts, attackers pipe malicious PowerShell scripts instantly into reminiscence from spoofed Microsoft domains.
The attackers host payloads on attacker-controlled infrastructure however prepend URLs with faux /us.microsoft.com/ paths to impersonate professional Microsoft sources. This fileless execution approach bypasses signature-based antivirus options fully, because the malicious code by no means touches disk.
The second part entails delivering a trojanized MSI bundle that exploits Home windows Installer’s SYSTEM-level privileges.
The bundle comprises a malicious DLL impersonating a professional SentinelOne EDR element, strategically positioned within the AppData folder a location usually excluded from rigorous safety monitoring to scale back alert noise.
When the professional SentinelOne executable launches, it masses the attacker’s malicious DLL as a substitute of the professional model, a way generally known as DLL sideloading that makes the assault seem as routine safety software program habits.
Safety Software program Into an Assault Vector
The implications of Storm-0249’s skill to abuse trusted EDR processes are profound. By hijacking digitally signed executables, the group transforms safety software program into an assault vector.
Community monitoring instruments observe the compromised SentinelAgentWorker.exe establishing command-and-control communications to newly registered domains, however belief the method as a result of it stays allowed and digitally signed.
The attackers encrypt C2 visitors with TLS, rendering it invisible to deep packet inspection and SSL inspection home equipment.
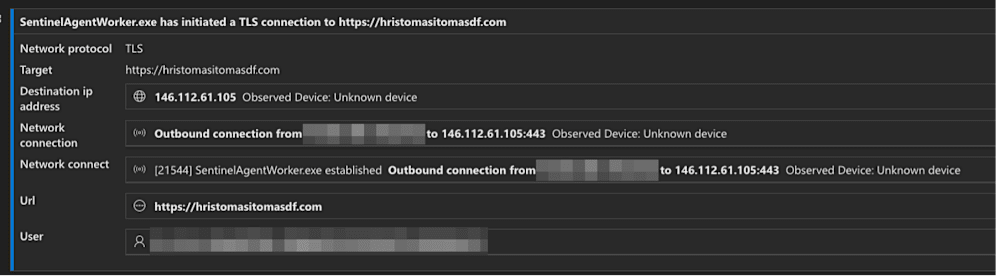
This neutralizes a good portion of conventional perimeter defenses whereas permitting operators to transmit malware encryption keys and payload directions with out detection.
Following preliminary compromise, Storm-0249 conducts reconnaissance utilizing professional Home windows utilities like reg.exe and findstr.exe to extract system identifiers together with MachineGuid.
Protection Imperatives
This information turns into crucial for ransomware associates, as teams like LockBit and ALPHV use MachineGuid to bind encryption keys to particular person sufferer techniques.
By securing this data, Storm-0249 delivers pre-profiled targets to ransomware prospects, dramatically decreasing time-to-ransom from weeks to days.
Organizations should implement behavioral analytics to detect anomalies corresponding to DLL sideloading, monitor DNS for newly registered domains (underneath 30-90 days outdated), and implement strict controls on professional instruments like curl.exe and PowerShell.
Automated incident response playbooks that isolate compromised hosts, block malicious domains, and stop execution of identified malicious hashes are important.
Storm-0249’s evolution demonstrates that conventional signature-based defenses are inadequate.
Safety groups should prioritize visibility into trusted processes, implement behavioral monitoring, and preserve community segmentation to disrupt these subtle assaults earlier than ransomware deployment turns into inevitable.
IOCs
| Artifact | Kind | Particulars |
|---|---|---|
07c5599b9bb00feb70c2d5e43b4b76f228866930 |
SHA-1 Hash | Malicious DLL named “SentinelAgentCore” (used for DLL sideloading) |
423f2fcf7ed347ee57c1a3cffa14099ec16ad09c |
SHA-1 Hash | Spear.msi (Malicious Installer) |
krivomadogolyhp[.]com |
Area | C2 Area |
hristomasitomasdf[.]com |
Area | C2 Area |
hamcore[.]se2 |
File/Useful resource* | C2 Area (Doubtless a reference to SoftEther VPN configuration file or artifact)* |
sgcipl[.]com |
Area | C2 Area (Used for spoofed Microsoft domains) |
178.16.52[.]145 |
IP Handle | Malicious IP Handle |
172.67.206[.]124 |
IP Handle | Malicious IP Handle |
Observe us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most well-liked Supply in Google.

