Cybercriminals are leveraging reviews of Venezuelan President Nicolás Maduro’s arrest on January 3, 2025, to distribute backdoor malware by way of a classy social engineering marketing campaign.
Safety researchers at Darktrace have uncovered a malicious operation that exploits this high-profile geopolitical occasion to compromise unsuspecting victims.
Assault Technique
The menace actors probably used spear-phishing emails containing a ZIP archive titled “US now deciding what’s subsequent for Venezuela.zip”.
Contained in the archive, victims discover an executable file named “Maduro to be taken to New York.exe” alongside a malicious dynamic-link library (DLL) known as “kugou.dll”.
The executable is definitely a professional KuGou binary, a Chinese language streaming platform, that has been weaponized to load the malicious DLL by way of DLL search-order hijacking.
As soon as executed, the malware creates a listing at C:ProgramDataTechnology360NB and copies itself there.
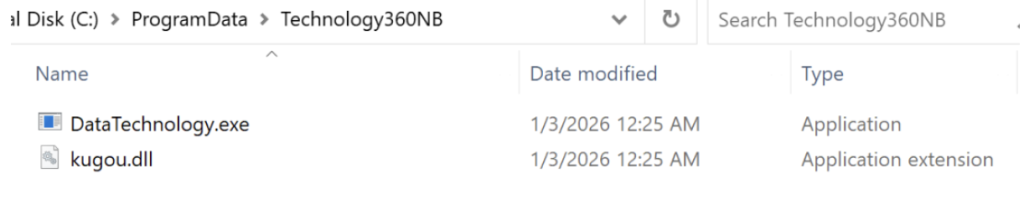
The executable is renamed “DataTechnology.exe” and configured to run robotically at system startup by way of a registry key at HKCUSoftwareMicrosoftWindowsCurrentVersionRunLite360.
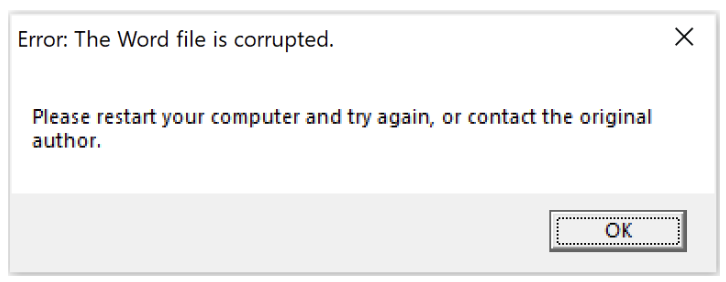
A misleading dialog field then prompts customers to restart their pc, and in the event that they don’t comply, the malware forces a system restart.
After the restart, the malware establishes encrypted TLS connections to its command-and-control server at 172.81.60[.]97 on port 443, periodically beaconing to obtain directions and configuration updates from the attackers.
This marketing campaign follows a well-established sample of exploiting main world occasions for malicious functions.
Related techniques have been noticed in campaigns associated to the Ukraine struggle, with menace actors utilizing prisoner-of-war references in phishing emails.
The Chinese language menace group Mustang Panda has repeatedly employed comparable methods, utilizing lures about Ukraine, Tibet conventions, the South China Sea, and Taiwan to deploy backdoors.
Whereas the techniques, methods, and procedures present similarities to Mustang Panda operations, researchers emphasize there’s inadequate proof to attribute this marketing campaign to a selected menace group definitively.
Organizations and customers are strongly suggested to train warning when opening e-mail attachments, notably these referencing present occasions.
Indicators of Compromise (IoCs)
- 172.81.60[.]97
- 8f81ce8ca6cdbc7d7eb10f4da5f470c6 – US now deciding what’s subsequent for Venezuela.zip
- 722bcd4b14aac3395f8a073050b9a578 – Maduro to be taken to New York.exe
- aea6f6edbbbb0ab0f22568dcb503d731 – kugou.dll
Comply with us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.

