A worrying shift within the techniques of “Clear Tribe,” a infamous risk group also referred to as APT36. Traditionally targeted on Indian authorities, protection, and academic sectors, the group has now expanded its scope to focus on India’s rising startup ecosystem.
This new marketing campaign makes use of refined lures themed round actual startup founders to contaminate victims with the “Crimson RAT” malware.
Energetic since 2013 and broadly linked to Pakistan-based actors, Clear Tribe often focuses on espionage in opposition to army and diplomatic targets.
The hackers are particularly concentrating on startups concerned in OSINT (Open Supply Intelligence) and cybersecurity.
Nevertheless, TRU’s current findings point out the group is now looking for intelligence inside personal firms.
These firms usually collaborate with authorities our bodies and regulation enforcement companies. By compromising these startups, the hackers probably goal to entry delicate authorities information not directly.
It’s a basic “provide chain” model method: in case you can not hack the federal government instantly, hack the personal distributors they belief.
The Clear Tribe Lure
The assault begins with a spear-phishing e mail containing an ISO file attachment named “MeetBisht.iso.”
To make the e-mail seem reliable, the hackers used decoy supplies referencing an actual Indian startup, “Voldebug,” and its founder.
When a sufferer opens the ISO file, they see what seems like an Excel shortcut (LNK file). Nevertheless, clicking this shortcut doesn’t open a spreadsheet. As a substitute, it triggers a hidden chain of occasions:
- A hidden batch script runs within the background.
- A decoy doc pops as much as distract the person.
- The “Crimson RAT” malware is silently put in on the pc.
The malware used on this marketing campaign is a Distant Entry Trojan (RAT). The model analyzed by Acronis has a definite characteristic: it’s artificially inflated to an enormous 34MB measurement.

The hackers stuffed the file with “rubbish information” to trick antivirus programs, as many safety scanners are designed to skip giant information to avoid wasting processing time.
As soon as energetic, Crimson RAT provides the attackers whole management over the contaminated machine. Its capabilities embody:
- Surveillance: Recording the display, turning on the webcam, and recording audio by way of the microphone.
- Theft: Itemizing all drives, trying to find particular information, and importing stolen information to the hackers.
- System Management: Killing operating processes and executing new instructions.
The malware makes use of a customized communication technique (TCP protocol) to speak to its command-and-control server, making it more durable for normal community screens to identify the site visitors.
Connecting the Dots
Acronis researchers are extremely assured that Clear Tribe is behind this assault. The digital fingerprints left behind together with particular server infrastructure hosted in the USA and the reuse of code from earlier assaults match the group’s historical past.
The malicious LNK, which was uploaded below the title Meet Bishkt.xlsx.lnk, had additionally been uploaded as Evidance.pdf.lnk.
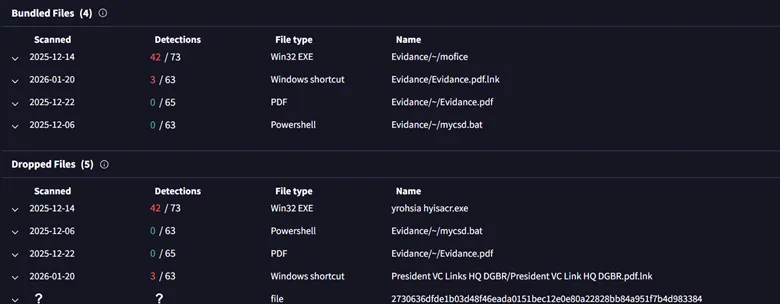
Apparently, the researchers additionally discovered a “signature” mistake: the hackers repeatedly misspelled the phrase “Proof” as “Evidance” of their file names. This spelling error has been seen in earlier campaigns concentrating on the Indian authorities.
This marketing campaign serves as a warning that India’s startups are now not flying below the radar. Due to their proximity to authorities operations and regulation enforcement, these agile firms are actually high-value targets for state-sponsored espionage.
Cybersecurity leaders within the startup sector should acknowledge that they’re now on the digital frontline.
Comply with us on Google Information, LinkedIn, and X to Get Immediate Updates and Set GBH as a Most well-liked Supply in Google.

