Two new adware campaigns that researchers name ProSpy and ToSpy lured Android customers with faux upgrades or plugins for the Sign and ToTok messaging apps to steal delicate knowledge.
To offer the malicious information a way of legitimacy, the menace actor distributed them by web sites that impersonated the 2 communication platforms.
Sign is a well-liked end-to-end encrypted messenger with greater than 100 million downloads on Google Play.
ToTok is developed by the UAE-based synthetic intelligence firm G42 and was kicked out from the Apple and Google app shops in 2019 after allegations of being a spying device for the UAE authorities.
Presently, ToTok is on the market for obtain from its official web site and third-party app shops.
Stealth and persistence
Researchers at cybersecurity firm ESET found the ProSpy marketing campaign in June however they consider that the exercise could have began since a minimum of 2024. Based mostly on their evaluation, the malicious campaigns are concentrating on customers within the United Arab Emirates.
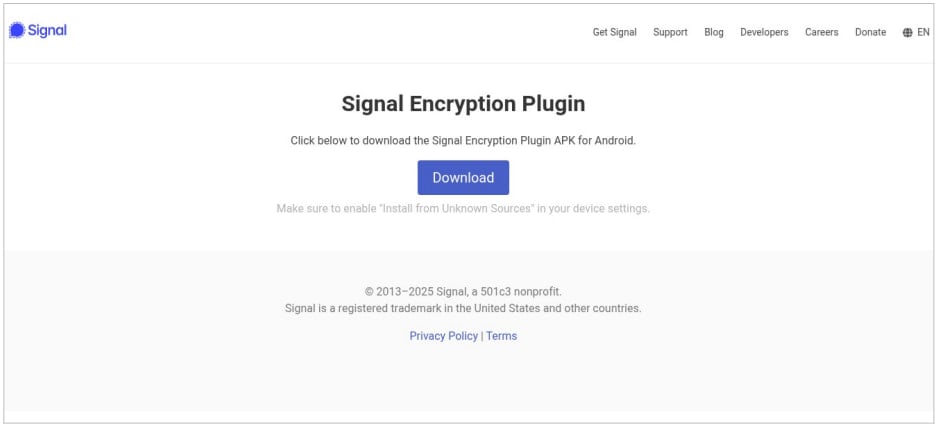
Through the investigation, they found “two beforehand undocumented adware households” that fake to be a Sign Encryption Plugin and a Professional variant of the ToTok app, none of which exist.
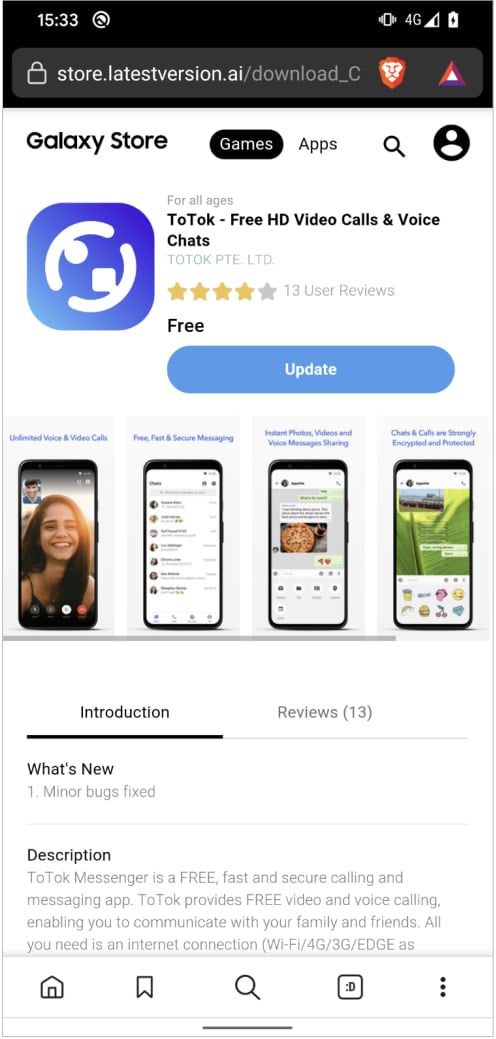
The operator of the adware marketing campaign distributed the malicious APK information by internet pages that impersonated the official Sign web site (https://sign.ct[.]ws and https://encryption-plug-in-signal.com-ae[.]internet/) and the Samsung Galaxy Retailer (retailer.latestversion[.]ai and https://retailer.appupdate[.]ai).
Supply: ESET
BleepingComputer tried accessing the fraudulent web site however most of them had been offline and one redirected to the official ToTok web site.
When executed, the ProSpy malware samples request entry to the contact checklist, SMS, and information, that are the standard permissions for messenger apps.
As soon as lively on the system, the malware exfiltrates the next knowledge:
- system info ({hardware}, working system, IP tackle)
- saved SMS texts, the contact checklist
- information (audio, paperwork, photos, movies)
- ToTok backup information
- checklist of the put in purposes
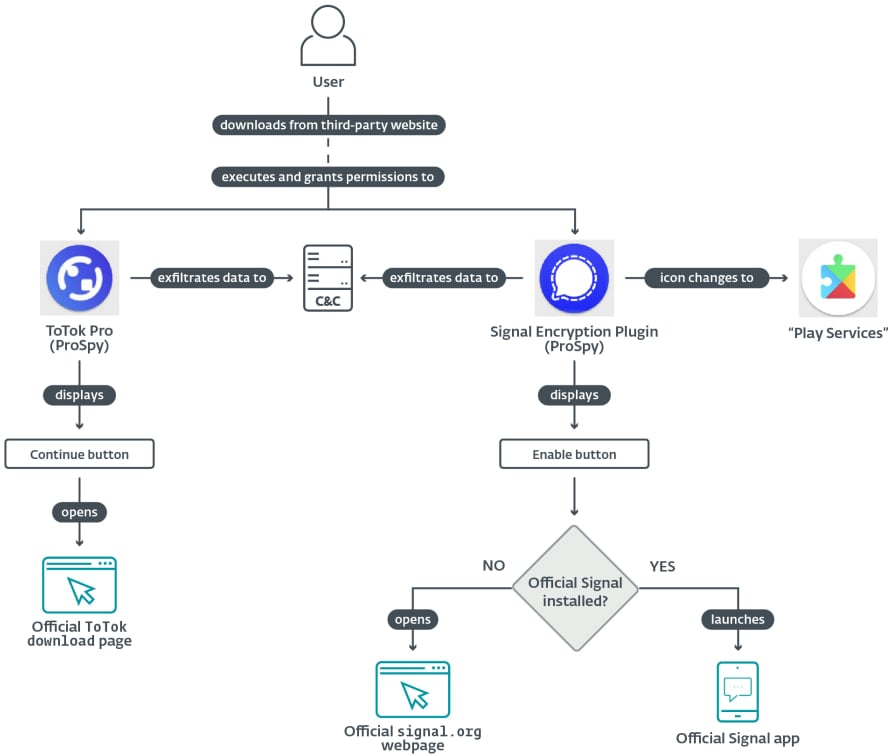
To remain hidden, the Sign Encryption Plugin makes use of the ‘Play Providers’ icon and label on the house display screen. Moreover, when tapping the icon the information display screen of a authentic Google Play Service app will open.
The diagram beneath explains how a ProSpy compromise works. The menace made an effort to keep away from elevating consumer suspicion by redirecting them to the official obtain website when the authentic app was lacking on the system.
Supply: ESET
ToSpy marketing campaign could have originated in 2022
In response to the researches, the ToSpy marketing campaign continues to be persevering with, based mostly on the lively standing of the command-and-control (C2) infrastructure.
ESET notes that this exercise could date way back to 2022, as they discovered a number of indicators pointing to that interval: a developer certificates created on Might 24, 2022, a website used for distribution and C2 registered on Might 18 that yr, and samples uploaded to the VirusTotal scanning platform on June 30.
Supply: ESET
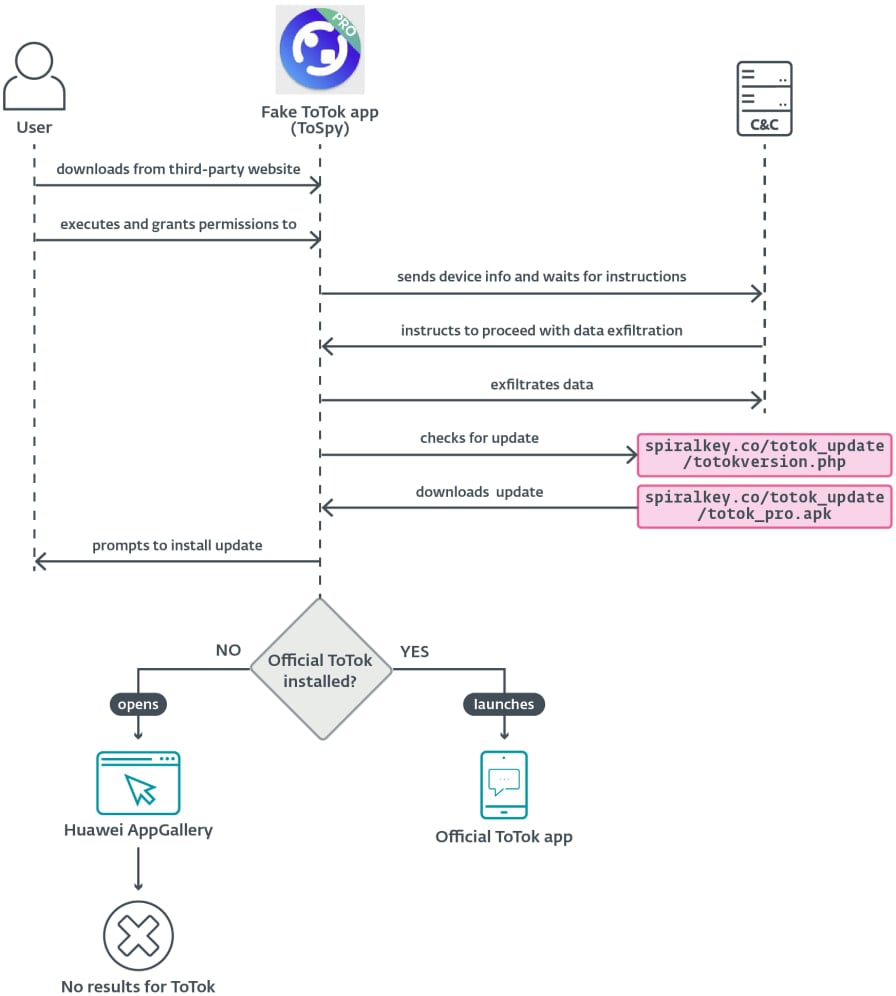
The faux ToTok app distributed on this marketing campaign prompts victims to grant contact and storage entry permissions, and collects the related knowledge, specializing in paperwork, photos, video, and ToTok chat backups (.ttkmbackup information).
ESET’s report notes that every one exfiltrated knowledge is first encrypted utilizing the AES symmetric encryption algorithm in CBC mode.
For stealth, ToSpy launches the true ToTok app when opened, if it is obtainable on the system.
If the app will not be current, the malware tries to open the Huawei AppGallery (both the authentic app or the default internet browser) so the consumer can get the official ToTok app.
Supply: ESET
Each adware households use three persistence mechanisms on contaminated units:
- Abuse of the ‘AlarmManager’ Android system API to restart mechanically if killed.
- Use a foreground service with persistent notifications so the system treats it as a high-priority course of.
- Registers to obtain BOOT_COMPLETED broadcast occasions so it may possibly restart the adware upon system reboot with out consumer interplay.
ESET has shared a complete checklist of indicators of compromise (IoCs) related to the ProSpy and ToSpy campaigns, however attribution stays inconclusive.
Android customers are really helpful to obtain apps solely from official or trusted repositories, or immediately from the writer’s webisite. They need to hold the Play Defend service lively on their system to disable already recognized threats.


