An extended-running Chrome extension malware marketing campaign has silently hijacked greater than 500,000 VKontakte (VK) accounts, forcing customers into attacker-controlled teams, resetting their settings each 30 days, and abusing VK’s personal infrastructure as command-and-control.
What seemed to be innocent VK customization instruments have been in actuality a tightly maintained malware undertaking operated by a single risk actor utilizing the GitHub.
The investigation started when a browser threat engine detected a Chrome extension injecting Yandex show advert scripts into each web page, a habits generally related to monetization however not essentially indicative of a full compromise.
Pivoting on the identical Yandex show framework and monitoring code led researchers to an extension referred to as “VK Types Themes for vk.com,” boasting round 400,000 installations and constructive critiques whereas claiming to reinforce VK’s consumer interface merely.
Contained in the extension, analysts discovered a dynamically computed Yandex metric ID: ‘R-A-‘ + 843079 * 2, which evaluates to R-A-1686158, a trick used to evade static string-based detection by scanners and retailer reviewers.
This ID turned the important thing to mapping a broader community of 5 associated extensions, collectively reaching roughly 502,000 installations, two of which have since been faraway from the Chrome Internet Retailer.
One of the vital standard entries on this community, VK Types, was eliminated on February 6 after the exercise got here to mild.
Working deeper evaluation on the VK Types codebase, researchers uncovered a multi-stage structure.
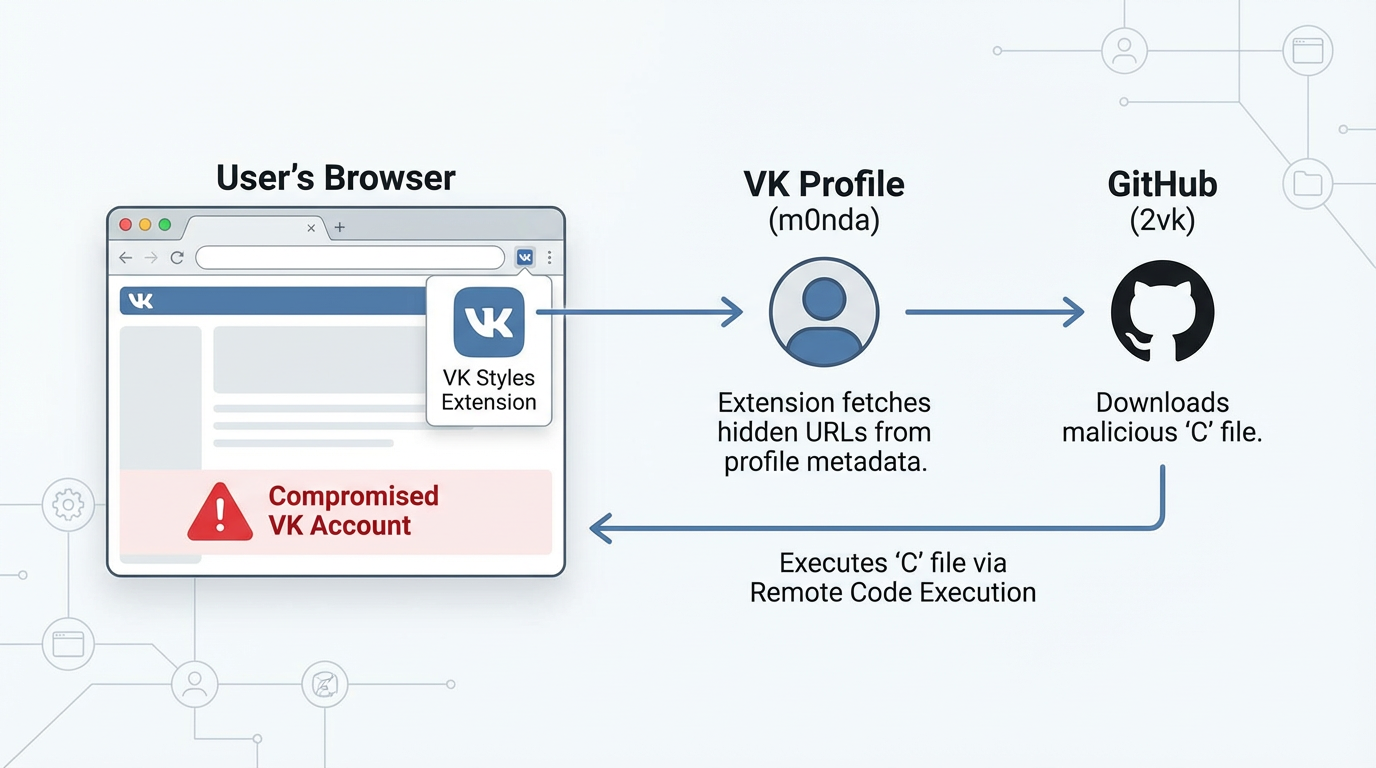
Two seemingly innocuous code fragments allowed arbitrary strings to be executed, and a name chain ultimately pointed to a VK profile at vk.com/m0nda, which the extension used as a covert management hub.
By pulling and executing knowledge from that profile, the extension successfully turned a traditional social account into stay C2 infrastructure.
Chrome Extension Malware Assault
The attacker hid the next-stage configuration inside HTML meta tags on the VK profile, together with an encoded description subject similar to: 4000 :: G2vk.github.io/-/ V1.0.250.69 Yan.yandex.ru/system/context.js Ayastatic.internet/partner-code-bundles/ :.
Decoding this reveals three key endpoints: a GitHub Pages website at https://2vk.github.io/-/, a Yandex promoting script, and extra ad-bundle internet hosting at Yandex’s static infrastructure, together with a model marker.
This design means the extension by no means hardcodes URLs; as a substitute, it fetches the VK profile, parses the meta tags, after which downloads the next-stage payload from GitHub, giving the attacker versatile, profile-driven configuration that’s troublesome to dam with out disrupting authentic VK site visitors.
On GitHub, below the account “2vk,” the repository named “-” hosts a JavaScript file merely referred to as C, which holds the core obfuscated payload injected into each VK web page visited by victims.
Koi’s analysis famous this marketing campaign, energetic since at the least June 2025 and nonetheless evolving as of January 2026, highlights how browser extensions, social networks, and developer platforms could be chained into resilient malware provide chains.
Commit historical past from June 2025 via January 2026 exhibits deliberate evolution: preliminary variations established CSRF cookie manipulation and primary VK API wrappers, later updates launched auto-subscription logic with a 75% chance per session, a 30‑day configuration reset cycle, and ultimately donation monitoring by way of the VK Donut API characteristic gating primarily based on cost standing.
Exposing the 500K Person Breach
Latest commits concentrate on decreasing detection floor, together with eradicating greater than 100 traces of IntersectionObserver code and refining selectors whereas persevering with model bumps.
Functionally, the malware performs 5 most important classes of malicious habits as soon as absolutely deployed.
First, it auto-subscribes customers to VK group -168874636, which redirects to the VK Types neighborhood (vk.com/2style), utilizing a 3-in-4 chance each time a sufferer visits VK, turning compromised accounts right into a development engine for the attacker’s personal group that now boasts over 1.4 million followers.
With excessive privileges, silent auto-updates, and restricted market vetting, malicious extensions like VK Types can quietly remodel regular social accounts into C2 servers and on a regular basis customers into unwitting distribution nodes.
Second, it enforces a 30‑day reset mechanism that modifications feed sorting, forces a default message theme, and overwrites consumer preferences, making certain continued management even when victims try to repair settings.
Third, the code manipulates VK’s CSRF safety cookie remixsec_redir, undermining a core safety management designed to validate delicate actions and making extension-driven requests seem authentic to VK’s backend.
Fourth, the malware tracks donation standing by way of VK Donut, selectively unlocking or limiting options primarily based on whether or not the sufferer has paid, successfully turning hijacked accounts right into a monetization channel somewhat than merely a botnet.
Lastly, the multi-stage structure, pushed by VK profile metadata and GitHub-hosted payloads, permits the attacker to replace habits in actual time with out altering the extension bundle itself; auto-updating extensions then propagate new malicious logic immediately to greater than half 1,000,000 customers.
IOCs
| Extension ID | Set up Rely |
|---|---|
| ceibjdigmfbbgcpkkdpmjokkokklodmc | 400,000 |
| mflibpdjoodmoppignjhciadahapkoch | 80,000 |
| lgakkahjfibfgmacigibnhcgepajgfdb | 20,000 |
| bndkfmmbidllaiccmpnbdonijmicaafn | 2,000 |
| pcdgkgbadeggbnodegejccjffnoakcoh | 2,000 |
Comply with us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most well-liked Supply in Google.

