A brand new wave of phishing campaigns the place scammers are abusing Google’s legit infrastructure to bypass safety filters.
Attackers at the moment are creating free developer accounts on Google Firebase to ship fraudulent emails that impersonate well-known manufacturers.
By leveraging the status of the Firebase area, these attackers are efficiently touchdown in customers’ inboxes, bypassing commonplace spam detection programs.
How the Assault Works
Google Firebase is a well-liked platform utilized by builders to construct cell and net functions.
It provides free accounts to assist builders check their software program. Sadly, scammers have realized that emails despatched from these accounts originate from trusted Google servers.
On this marketing campaign, attackers register free accounts and use them to broadcast phishing emails.
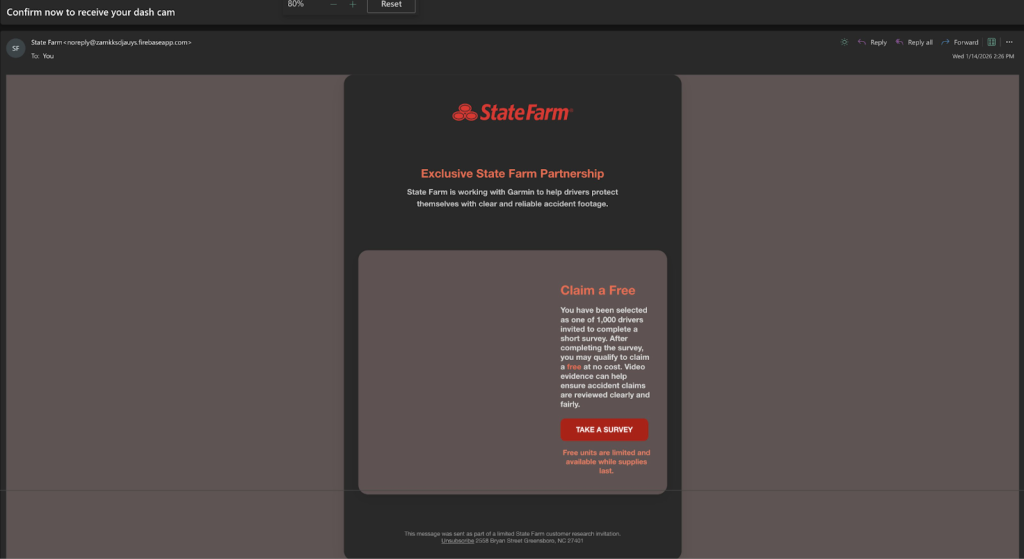
These messages sometimes come from addresses ending in firebaseapp.com. As a result of the emails are technically despatched from a legit Google service, electronic mail safety gateways typically mark them as secure.
The campaigns depend on two main psychological triggers: worry and greed.
- Scare Ways: Many victims obtain pressing alerts claiming that their financial institution accounts or on-line profiles have been compromised. These messages typically warn of “fraudulent account use” and demand speedy motion to forestall account lockout.
- Faux Giveaways: Different emails lure victims with the promise of free, high-value gadgets. These pretend promotions mimic widespread retail manufacturers, encouraging customers to click on hyperlinks to say a prize.
As soon as a person clicks a hyperlink in these emails, they’re redirected to malicious web sites designed to steal delicate information, reminiscent of login credentials or bank card numbers, as reported PaloAlto Community.
Indicators of Compromise (IoCs)
Safety groups must be looking out for particular patterns in electronic mail site visitors.
The attackers typically use randomly generated subdomains on the Firebase platform. Examples of sending addresses noticed on this marketing campaign embrace:
Moreover, the hyperlinks contained inside these emails redirect to exterior phishing pages.
Researchers have recognized a number of malicious URLs, together with these hosted on clouud.thebatata[.]org and shortened hyperlinks utilizing rebrand[.]ly.
To remain secure, customers must be skeptical of any unsolicited emails, even when they seem to return from a good technical area like Firebase.
All the time confirm the sender’s tackle fastidiously. If an electronic mail claims to be from a financial institution or retailer however the tackle ends in firebaseapp.com, it’s nearly definitely a rip-off.
Community directors are suggested to observe site visitors for the recognized domains and to contemplate blocking emails from unknown Firebase subdomains if their group doesn’t actively use them for growth.
Observe us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google

