[ad_1]
A major shift within the cyber menace panorama has been recognized in a brand new analysis report, distinguishing trendy “Hacktivist Proxy Operations” from conventional digital protests or felony schemes.
The findings recommend that hacktivism has advanced right into a repeatable, model-driven instrument of statecraft, permitting nations to exert geopolitical strain whereas sustaining believable deniability.
The report particulars how these operations occupy a strategic “gray zone.” In contrast to state-sponsored Superior Persistent Threats (APTs) that search intelligence or destruction, or financially motivated cybercrime gangs, Hacktivist Proxies operate as ideologically aligned intermediaries.
They don’t require formal command-and-control or direct funding. As a substitute, they act on shared narratives that align with state pursuits, providing a low-cost, high-deniability mechanism for coercion.
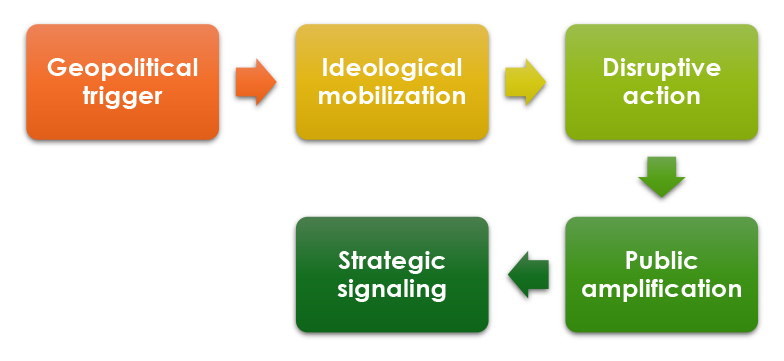
The Activation Chain: A Predictable Cycle
Analysis signifies that these operations are not often random. As a substitute, they observe a constant “activation chain” triggered by particular geopolitical occasions such because the announcement of financial sanctions, navy assist packages, or diplomatic escalations.
As soon as a set off occasion happens, the mannequin observes a fast sequence:
- Narrative Mobilization: On-line channels shift from routine chatter to requires retaliation.
- Volunteer Coordination: Goal lists are distributed, prioritizing high-visibility sectors like authorities portals, finance, and transportation.
- Disruptive Execution: Teams launch DDoS assaults, web site defacements, and symbolic intrusions.
- Amplification: The psychological impression is maximized by way of social media claims of “infrastructure collapse,” typically exaggerated past the precise technical harm.
- De-escalation: Operations taper off as soon as the political level is scored, distinguishing them from persistent felony campaigns.
Whereas the technical strategies primarily DDoS and defacement are sometimes unsophisticated, their cumulative strategic impression is substantial.
In contrast to conventional cyber operations, which search technical dominance or long-term entry, hacktivist proxy exercise seeks visibility, disruption, and signalling.
The target is just not essentially to trigger lasting harm, however to show functionality, impose friction, and affect notion at vital moments.
The report argues that safety frameworks typically misclassify these assaults as mere “nuisances.” This underestimation is harmful.
For vital infrastructure operators and authorities our bodies, repeated low-intensity disruptions exhaust defensive sources, erode public belief, and manipulate media notion throughout delicate political moments.
The core benefit for beneficiary states is ambiguity. By counting on volunteers and customary instruments, these operations complicate attribution.
States can body the exercise as impartial “patriotic” resistance, delaying diplomatic response and lowering the chance of direct escalation.
Implications for Protection
The report concludes that current cyber protection fashions are inadequate for countering proxy strain.
As geopolitical competitors intensifies, Hacktivist Proxy Operations are anticipated to turn out to be a normalized function of contemporary statecraft, demanding that defenders put together for waves of ideologically pushed disruption that mirror the heart beat of worldwide politics.
Organizations are suggested to maneuver past purely technical attribution and combine geopolitical intelligence into their menace modelling.
“Efficient mitigation doesn’t require attribution certainty, however slightly improved resilience… and operational preparedness for episodic, narrative-driven disruption,” the report states.
Comply with us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most well-liked Supply in Google.
[ad_2]



