Lead analysts: Cameron Sweeney, Lucy Gee, Louis Tiley, James Dyer
“Tremendous-app” WeChat gives a wealth of performance—from prompt messaging, textual content and voice messaging, and video calls to cell funds, journey reserving, ordering meals deliveries, paying payments and even accessing authorities companies.
Offered by Chinese language know-how conglomerate Tencent, WeChat has change into deeply built-in into day by day life in China and utilization has been spreading globally. The app now boasts over 1.4 billion energetic customers (24.8% of whole web customers).
In addition to interesting to respectable customers, the breadth of performance—notably WeChat’s cell cost functionality—additionally makes it engaging to cybercriminals. An preliminary phishing electronic mail is used to maneuver victims into WeChat the place social engineering assaults and cost fraud can happen in an surroundings that it’s harder to watch and safe.
Very similar to WeChat utilization, these assaults are on the rise exterior of China.
In 2024, solely 0.04% of phishing emails detected by KnowBe4 Defend within the US and EMEA (together with the UK) contained WeChat “Add Contact” QR codes. Because the begin of 2025, this has risen to 1.43%, spiking in November at 5.1%.
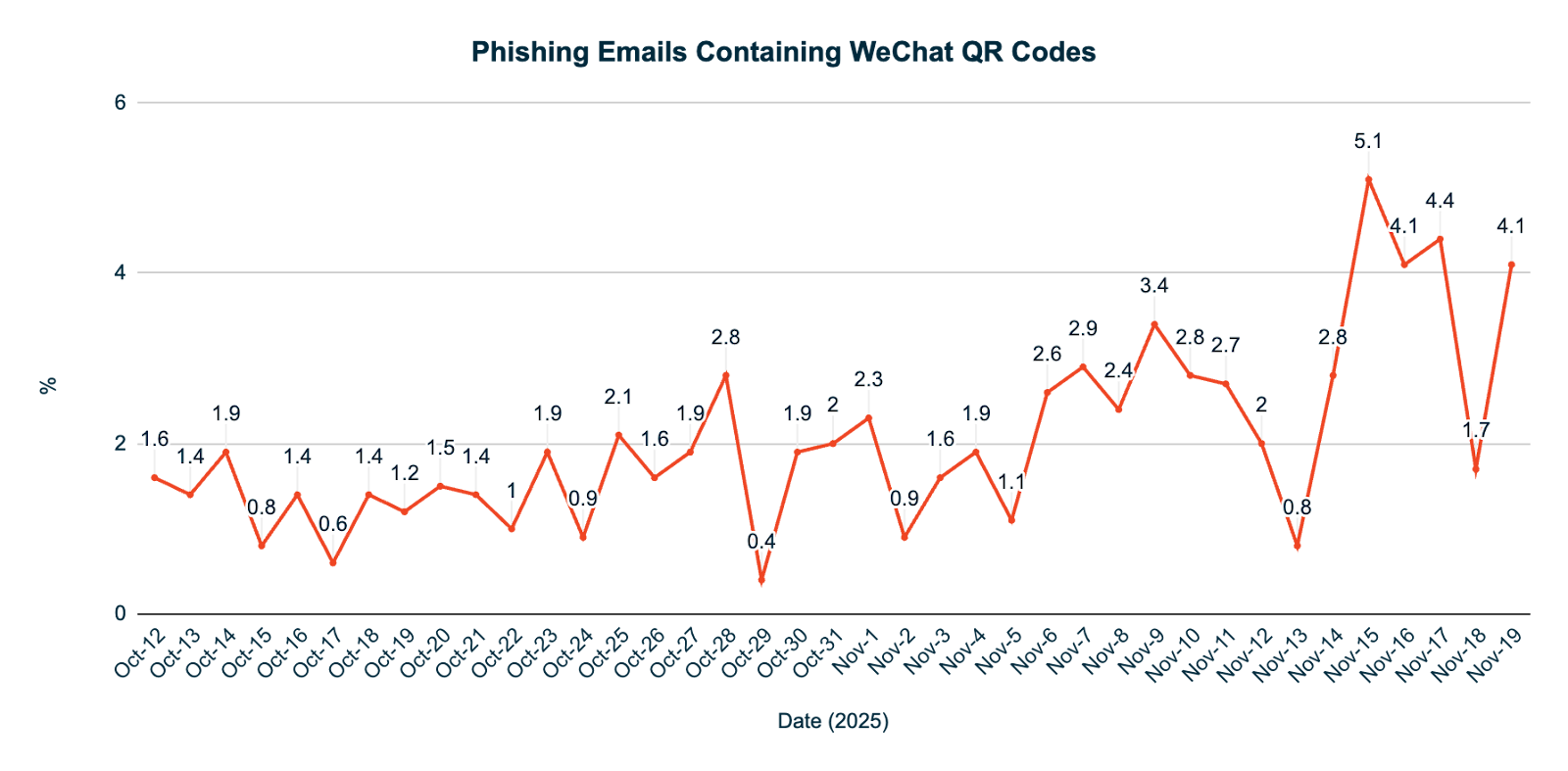
Whereas the general quantity stays comparatively low, this represents a 3,475% enhance throughout these areas.
Moreover, 61.7% of those phishing emails have been written in English and an additional 6.5% have been in languages aside from Chinese language or English, indicating a rising and focused diversification.
This transfer displays regulation enforcement crackdowns on home and near-border fraud networks in China, pushing rip-off operators to department out. GenAI has been a key accelerator of this shift, eradicating the necessity for language proficiency to ship a convincing phishing electronic mail or prompt message. Each international programs and home Chinese language LLMs (equivalent to Baidu’s ERNIE Bot) make it simple for cybercriminals to create pure, high-quality phishing emails in non-Chinese language languages.
WeChat Phishing Assault Abstract
Vector and sort: E-mail Phishing
Strategies: Impersonation, Quishing, Cost Fraud
Bypassed SEG detection: Sure
Targets: Organizations globally
The assaults usually start with a high-volume phishing marketing campaign generated by a bulk-sending phishing toolkit with a respectable WeChat “Add Contact” embedded inside the template. The emails use social engineering to lure the recipient in with an attention-grabbing provide, equivalent to enterprise alternatives, buy orders, funding ideas, procurement requests, job gives or partnership invites.
The phishing electronic mail beneath was detected by KnowBe4 Defend concentrating on certainly one of our US prospects. The e-mail is written in fluent English, asking the recipient to progress an software for a “Distant Administrative Assistant” position providing key perks to entice the recipient.
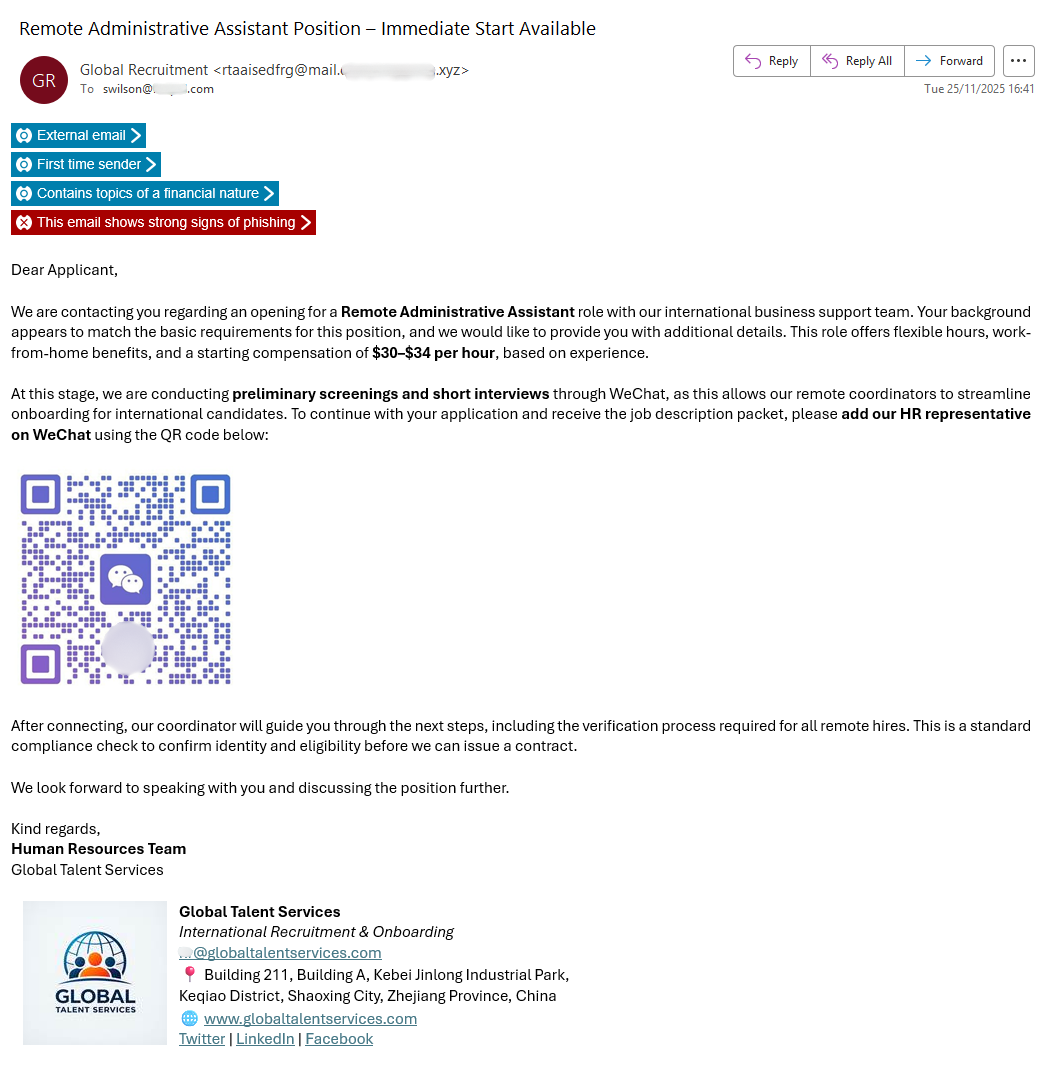
Preliminary templated electronic mail assault despatched utilizing a phishing toolkit, with KnowBe4 Defend anti-phishing banners seen.
As soon as the cybercriminal is added on WeChat, they conduct a personalised dialog designed to socially engineer the goal, progressively constructing belief earlier than transferring onto their final intention: monetary fraud, equivalent to advance-fee fraud, pretend procurement deposits, funding scams, romance-style social manipulation, or requests for “pressing” cross-border funds.
These financial transfers happen through WeChat Pay, which gives a quick cost service that’s troublesome to hint and reverse. The platform additionally offers a largely closed ecosystem. Id particulars and dialog histories exist inside Tencent’s surroundings, which may make cross-border investigation and restoration sluggish. In consequence, shifting victims from electronic mail into WeChat is now a core tactic in lots of China-linked fraud operations.
How Cybercrimals Use WeChat to Defraud Their Victims
KnowBe4 Menace Labs engaged straight with the attacker to higher perceive the character of the social-engineering payload.
The next screenshots seize this interplay and reveal that the marketing campaign was an try and defraud victims via a pretend job-recruitment scheme.
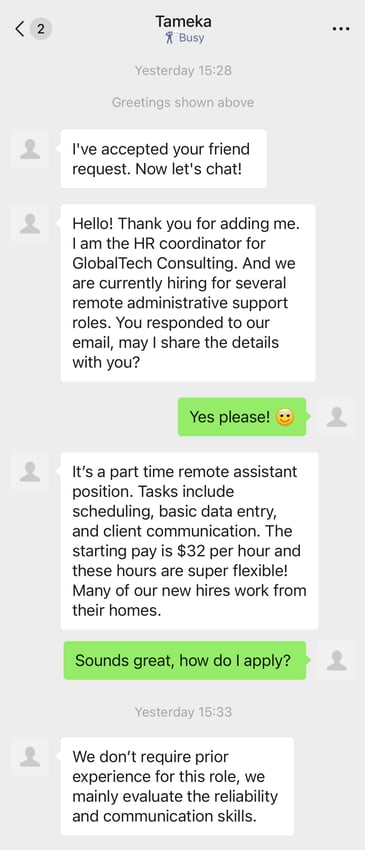 |
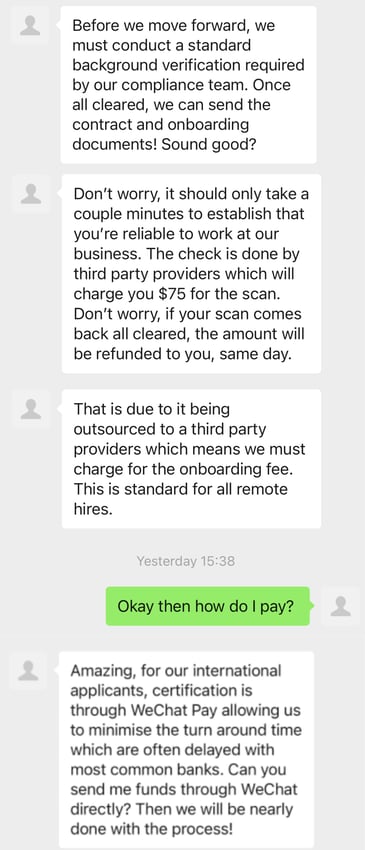 |
Instance of a WeChat social engineering assault.
After transferring the sufferer into WeChat, the attacker tried to extract cash below the guise of a “refundable background examine” required for employment. The small quantity requested ($75) is meant to look routine and keep away from elevating the goal’s suspicions. Moreover, if a sufferer pays, the cybercriminal is aware of they might be inclined to future extortion.
Just like the above electronic mail, the assault is written in fluent English, with the cybercriminal creating an in depth pretext about why the funds are required and must be transferred utilizing WeChat Pay. The identical day moneyback assure for a clear background examine can additional incentivize the goal, particularly in the event that they consider the examine received’t disclose something.
Phishing Toolkit That Simplifies WeChat Assaults
This assault leveraged an SMTP bulk-sending phishing toolkit generally known as a 邮件群发器 (“mass-mailer” or “bulk ship device”). This equipment is designed to ship extraordinarily excessive volumes of templated phishing emails whereas robotically rotating sender identities, spoofed domains and message codecs to evade conventional electronic mail safety filters.
The emails our Menace Lab crew analyzed confirmed a number of sturdy fingerprint indicators.
|
Fingerprint Noticed |
Description |
Indicated Toolkit Conduct |
Confidence |
|
Polymorphic From-address |
Randomized sender names + disposable domains (e.g., brief. web site domains) |
Automated sender rotation function in Chinese language “群发器” mass-mailing kits |
Excessive |
|
Artificial Area (no SPF/DKIM/DMARC) |
Area seems machine-generated and never configured for authentication |
Bulk SMTP kits utilizing auto-registered or throwaway domains; no authentication setup |
Excessive |
|
Base64-encoded HTML physique |
Total message physique encoded in Base64 with easy HTML template |
Matches Python SMTP群发器 script output that wraps templates in Base64 |
Excessive |
|
MIME boundary format (===============__…) |
Boundary string has double underscores and particular construction |
Matches Python electronic mail.mime.multipart default format utilized in Chinese language bulk-mailer variants |
Excessive |
|
Header ordering irregularities |
Message-ID, boundaries, and content material headers seem in non-standard sequence |
Attribute of “DIY” Chinese language spam kits utilizing Python libraries moderately than business mailers |
Medium |
|
Message-ID not tied to sending area |
Random ID not related to the spoofed area |
Signifies use of Python’s electronic mail.utils.make_msgid() in SMTP spam scripts |
Excessive |
|
Chinese language-language encoded topic fields |
UTF-8 Base64-encoded topic, typical of Chinese language spam templates |
Frequent in Chinese language mass-spam kits designed for worldwide campaigns |
Excessive |
|
Template-style electronic mail physique with QR placeholder |
HTML structure designed for swapping in pictures (e.g., WeChat QR) |
Signifies prebuilt template system present in Chinese language funnelling kits (“引流套件”) |
Excessive |
|
No phishing hyperlink solely QR to WeChat |
E-mail designed emigrate sufferer into WeChat, to not an internet site |
Matches “WeChat lead funnel” kits utilized in job, romance, and funding fraud |
Excessive |
Past these technical artefacts this marketing campaign contained traits intently aligned with Python-based SMTP “群发器” instruments and tutorials extensively shared on Chinese language-language developer platforms (generally bought on Chinese language Telegram and QQ channels).
A extensively referenced tutorial on Tencent Cloud Developer demonstrates these precise strategies, together with establishing MIMEMultipart messages, embedding HTML templates, and authenticating to SMTP servers utilizing easy username/password credentials—mirroring the construction of the phishing emails noticed on this marketing campaign.
GitHub additionally hosts brazenly accessible tasks that help bulk or spam-style SMTP sending, together with “A Easy SMTP Server to ship electronic mail (spam?)”, “Python Script for E-mail Bombing which helps Gmail, Yahoo, Hotmail/Outlook”, “python-smtp-mass-mailer”, and a number of other Chinese language-language repositories labelled as “邮件群发工具”.
These scripts routinely incorporate the identical primitives Python-generated MIME boundaries, rudimentary header development, disposable SMTP account help and high-volume looping that seem within the phishing samples. Whereas the particular script used on this assault can’t be recognized, the overlap in methodology strongly means that the operator relied on a generally circulated Python SMTP 群发 script sourced from this surroundings of tutorials and mass-sending examples.
Defending Your Workers and Group From WeChat Phishing (Quishing) Assaults
Very similar to different third-party platforms, it’s troublesome for organizations to watch and safe WeChat. Because the app’s international presence continues to develop, then, it’s turning into more and more essential that organizations can detect an preliminary WeChat-themed phishing electronic mail earlier than the assault strikes platforms.
Our Menace Lab crew has analyzed a number of WeChat phishing toolkits (alongside the one outlined right here) and all contained strategies, equivalent to robotically rotating sender identities and spoofed domains, designed to evade conventional safe electronic mail gateways and native defenses.
Consequently, organizations want to make sure additionally they use superior electronic mail safety, equivalent to KnowBe4 Defend, to detect inbound assaults. These merchandise make the most of AI-driven detection applied sciences like pure language processing (NLP) and pure language understanding (NLU) to determine linguistic markers of phishing, together with atypical requests and manipulation, equivalent to urging a goal to attach on a third-party platform to debate a job provide. Moreover, it’s essential that the product takes a zero-trust method to detect assaults whatever the area they’re despatched from.
Lastly, it’s essential to persistently increase consciousness of WeChat as a possible channel for cybercrime. This may be executed via conventional consciousness campaigns and coaching however real-time nudges and training, equivalent to context-aware phishing banners, present a strong device in constructing vigilance.
By combining instruments and coaching, organizations can fight the rising risk introduced by cybercriminals exploiting WeChat.

