Cybersecurity researchers at Rapid7 Labs have uncovered a classy new menace: SantaStealer, a malware-as-a-service data stealer actively promoted on Telegram channels and underground hacker boards.
The malware, which not too long ago rebranded from “BluelineStealer,” is scheduled for launch earlier than the top of 2025 and represents a rising menace to customers worldwide as a consequence of its means to exfiltrate delicate information whereas working completely in reminiscence to evade detection.
SantaStealer is designed to gather and exfiltrate a complete vary of delicate data together with paperwork, credentials, cryptocurrency wallets, and information from quite a few purposes.
The stolen information is compressed, divided into 10 MB chunks, and transmitted to command-and-control servers over unencrypted HTTP connections.
The malware operators promote their product as “totally written in C” with a “customized C polymorphic engine” that claims to be “totally undetected,” although Rapid7’s evaluation reveals a distinct image.
The invention occurred in early December 2025 when Rapid7 recognized a Home windows executable that triggered generic infostealer detection guidelines sometimes related to the Raccoon stealer household.
Evaluation of the pattern revealed a 64-bit DLL containing over 500 exported symbols with descriptive names corresponding to “payload_main,” “check_antivm,” and “browser_names,” together with quite a few unencrypted strings indicating credential-stealing capabilities.
Technical Structure
The malware reveals a modular, multi-threaded design that includes 14 completely different specialised modules.
These embody generic modules for studying surroundings variables and taking screenshots, in addition to specialised modules concentrating on Telegram desktop, Discord, Steam, browser extensions, shopping histories, and passwords.
For Chromium-based browsers, SantaStealer employs strategies to bypass AppBound Encryption by embedding an extra executable that seems to be based mostly on the ChromElevator undertaking, which makes use of direct syscall-based reflective course of hollowing to hijack reputable browser processes.
The statically linked libraries recognized within the malware embody cJSON for JSON parsing, miniz as a zlib-replacement library, and sqlite3 for interfacing with SQLite databases.
SantaStealer incorporates a number of anti-analysis options that adjust throughout samples, suggesting ongoing improvement.
These embody checks for blocked processes by customized rolling checksums, suspicious laptop names, hard-coded evaluation surroundings directories, system uptime verification, and time-based debugger detection.
Curiously, the malware consists of an elective verify for Commonwealth of Impartial States international locations, the place it detects Russian keyboard layouts utilizing the GetKeyboardLayoutList API and terminates execution if configured to keep away from CIS targets.
Pricing and Industrial Mannequin
The menace actors behind SantaStealer function a classy associates program accessible by an internet panel the place customers can register accounts and entry characteristic lists, pricing fashions, and construct configuration choices.
The malware configuration is saved as JSON-encoded information and consists of a banner with Unicode artwork spelling “SANTA STEALER” and a hyperlink to the stealer’s Telegram channel.
The fundamental variant is priced at $175 monthly, whereas a premium variant prices $300 monthly.
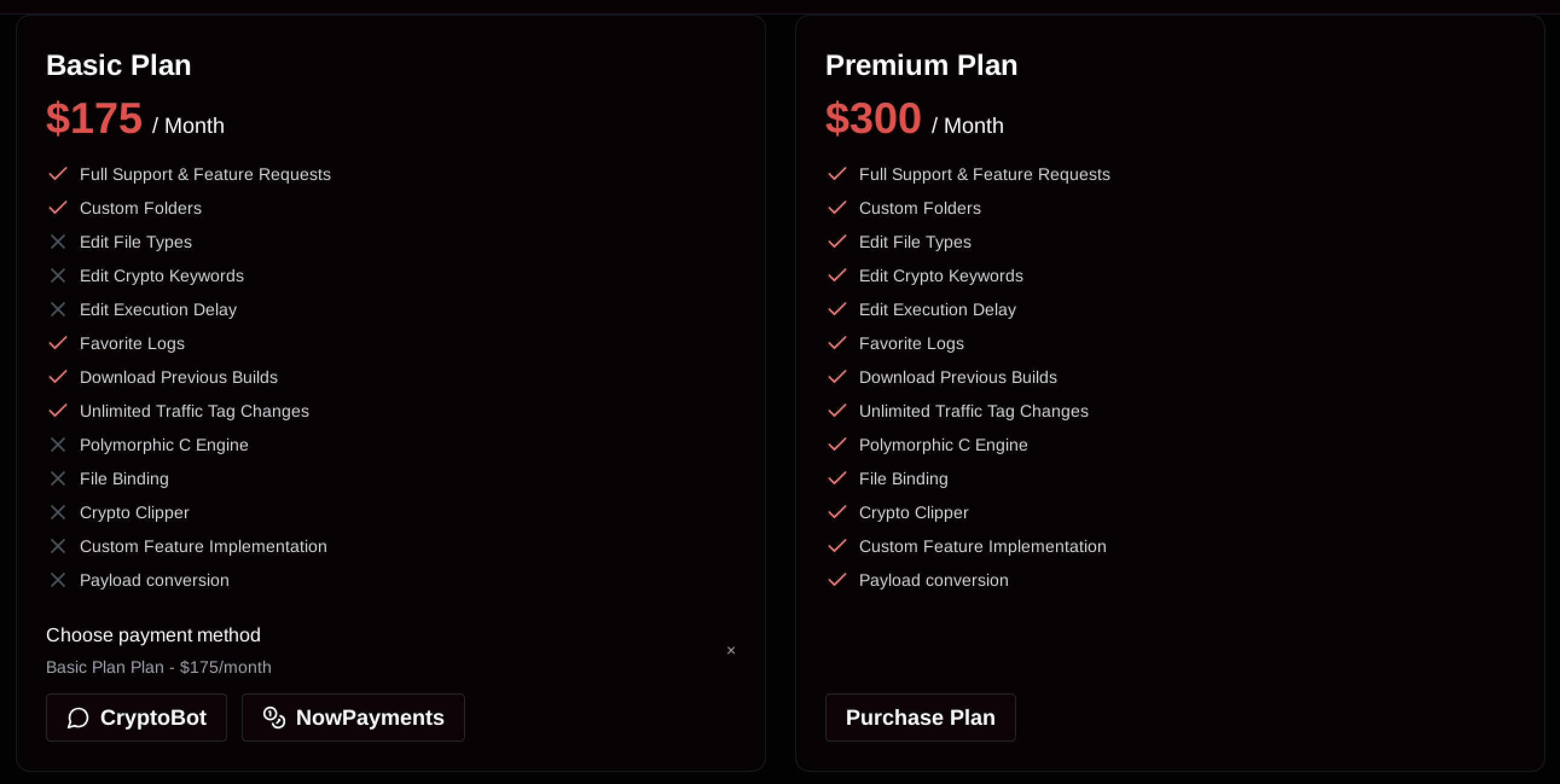
The operators promote bold capabilities together with anti-analysis strategies, antivirus bypasses, and deployment capabilities in authorities companies and company networks.
The malware is promoted on each Telegram and the Russian-speaking Lolz hacker discussion board, with indicators suggesting Russian citizenship of the operators based mostly on using Soviet Union nation code domains and CIS concentrating on choices.
Regardless of the daring claims made by SantaStealer’s operators, Rapid7’s evaluation reveals vital operational safety failures.
The leaked samples include unobfuscated code with full image names and unencrypted strings, making them removed from undetectable and comparatively easy to research.
The untimely leak of those improvement builds with such clear indicators suggests poor operational safety which will considerably undermine the malware’s effectiveness.
To guard towards SantaStealer infections, customers ought to train warning with unrecognized hyperlinks and e mail attachments, keep away from pretend human verification prompts or technical assist directions requesting command execution, and chorus from operating unverified code from sources corresponding to pirated software program, videogame cheats, or unverified plugins and extensions.
Organizations ought to guarantee endpoint detection programs are up to date to acknowledge the present indicators of compromise related to this rising menace.
Comply with us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most popular Supply in Google.

