Seqrite Labs has uncovered an energetic Russian phishing marketing campaign that delivers Phantom information-stealing malware by way of malicious ISO information embedded in faux fee affirmation emails.
The subtle assault primarily targets finance and accounting professionals in Russia, utilizing social engineering techniques to deceive victims into executing malicious payloads that steal credentials, cryptocurrency wallets, browser information, and delicate information.
The marketing campaign primarily focuses on finance, accounting, treasury, and fee departments inside Russian organizations.
Secondary targets embody procurement groups, authorized departments, HR and payroll employees, govt assistants, and small to medium-sized enterprises working in Russian-speaking areas.
The assault poses important dangers, together with credential theft, bill fraud, unauthorized monetary transfers, and potential lateral motion into broader IT programs.
Phishing Marketing campaign Origins
Seqrite Researchers recognized a Russian-language phishing e-mail titled “Подтверждение банковского перевода” (Affirmation of Financial institution Switch) originating from compromised e-mail addresses.
The message impersonates TorFX Forex Dealer and makes use of formal enterprise language to look professional to finance personnel.
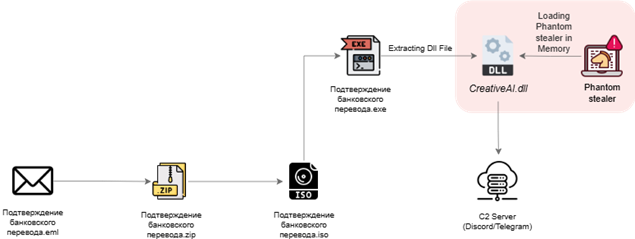
The e-mail accommodates a malicious ZIP archive roughly 1 megabyte in measurement that conceals an ISO file designed to bypass conventional safety controls.
The sender area “iskra-svarka.ru” and the spoofed “agroterminal.c” area are unrelated to the purported group, revealing clear indicators of e-mail spoofing and impersonation techniques designed to determine false credibility with potential victims.
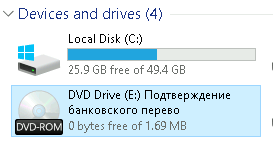
When the sufferer opens the ZIP attachment and executes the ISO file, it auto-mounts as a digital CD drive, revealing an executable disguised as a professional fee affirmation doc.
The executable masses further payloads into reminiscence, starting with a DLL file named CreativeAI.dll that accommodates encrypted code.
This DLL decrypts and injects the ultimate model of the Phantom Stealer malware into the system.
The malware employs steganography strategies, hiding malicious code throughout the System.Drawing.Bitmap objects to evade detection.
This layered strategy permits attackers to bypass safety options that primarily scan for identified malware signatures.
Operation MoneyMount-ISO represents an evolving development the place risk actors leverage ISO-mounted executables to ship commodity stealers whereas evading perimeter safety controls.
The marketing campaign’s payment-confirmation social engineering lure mixed with spoofed Russian enterprise domains signifies extremely focused credential-theft exercise explicitly designed for finance-related roles.
The growing sophistication of stealer malware delivered by way of unconventional file codecs calls for a multi-layered protection strategy that mixes technical controls with person training.
IOCs:
| 27bc3c4eed4e70ff5a438815b1694f83150c36d351ae1095c2811c962591e1bf | Electronic mail |
| 4b16604768565571f692d3fa84bda41ad8e244f95fbe6ab37b62291c5f9b3599 | Подтверждение банковского перевода.zip |
| 60994115258335b1e380002c7efcbb47682f644cb6a41585a1737b136e7544f9 | Подтверждение банковского перевода.iso |
| 78826700c53185405a0a3897848ca8474920804a01172f987a18bd3ef9a4fc77 | HvNC.exe |
Comply with us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.

