The Cybersecurity and Infrastructure Safety Company (CISA) and the Nationwide Safety Company (NSA), joined by Canadian cyber authorities, have issued a joint alert warning of a classy new malware marketing campaign dubbed “BRICKSTORM.”
In keeping with the advisory launched, state-sponsored hackers from the Folks’s Republic of China (PRC) are actively utilizing this device to infiltrate and conceal inside vital authorities and expertise networks.
The alert describes BRICKSTORM as a harmful “backdoor,” a sort of malicious software program that capabilities like a secret unlocking mechanism, permitting attackers to return to a sufferer’s system every time they please.
The malware is particularly designed to focus on VMware vSphere, a broadly used software program for operating digital servers, in addition to commonplace Home windows environments.
Officers acknowledged that the first objective of the marketing campaign is espionage. By concentrating on the underlying software program that manages company servers (particularly VMware vCenter and ESXi), the attackers can successfully turn into “ghosts” within the machine.
They will monitor exercise, steal delicate knowledge, and even copy whole “snapshots” of servers to extract passwords and cryptographic keys with out triggering commonplace safety alarms.
How the Assault Works
The report reveals that these assaults are extremely calculated. In a single confirmed case, hackers gained entry to a sufferer’s community as early as April 2024 and remained undetected till September 2025.
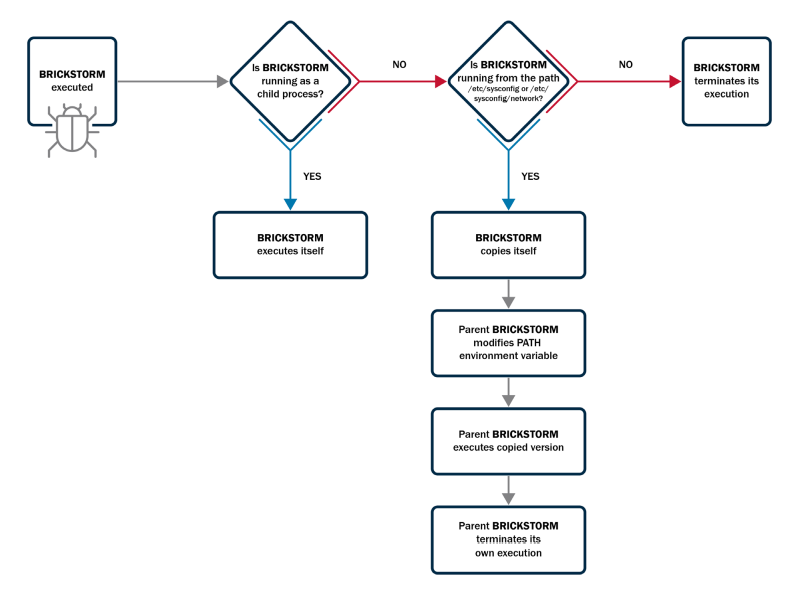
They initially broke in by means of a weak internet server, then moved sideways by means of the community utilizing stolen passwords. As soon as deep inside, they planted the BRICKSTORM malware.
What makes BRICKSTORM significantly troublesome to detect is its potential to mix in. The malware makes use of advanced encryption strategies to cover its communications.
It disguises its instructions as common internet site visitors or safe web connections, making it seem like common enterprise exercise to community defenders.
It additionally has a “self-watching” characteristic. If a safety program tries to cease or delete it, BRICKSTORM can routinely reinstall itself and reboot, guaranteeing the attackers by no means lose their foothold.
The businesses warned that this marketing campaign is concentrating on “Authorities Companies and Amenities” and the “Info Know-how” sectors.
The influence of a profitable an infection could be extreme. Within the analyzed assaults, hackers stole vital digital keys, enabling them to impersonate reputable customers and entry extremely restricted areas of the community.
CISA and the NSA are urging all organizations, particularly these in vital infrastructure, to look their networks for indicators of this particular menace instantly.
The businesses have launched technical “signatures”, digital fingerprints that safety groups can use to determine the malware.
Directors are suggested to replace their VMware merchandise instantly, strictly restrict entry to administration techniques, and monitor for any uncommon account exercise. “
It is a long-term persistence device,” the alert concludes, warning that merely eradicating the preliminary an infection might not be sufficient if the attackers have already burrowed deep into the virtualization infrastructure.
Comply with us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most well-liked Supply in Google.

