Appears will be deceiving, a lot in order that the acquainted icon may masks malware designed to steal your knowledge and cash.
06 Oct 2025
•
,
5 min. learn

PDF recordsdata have change into a staple of our every day digital lives, each at work and at house. They work seamlessly throughout working programs and gadgets, they usually couldn’t be simpler to create and share. Day by day, numerous PDF (Transportable Doc Format) recordsdata are exchanged throughout inboxes and messaging platforms, and likelihood is, you’ve opened one at present with out a second thought.
Nonetheless, this all can be partly what makes PDFs the proper disguise for all method of threats. At first look, PDF recordsdata appear about as benign as digital recordsdata get. To the bare eye, a malware-laced PDF or, certainly, one other file sort spreading below the guise of a PDF doesn’t essentially look a lot totally different from an strange bill, resume or authorities type.
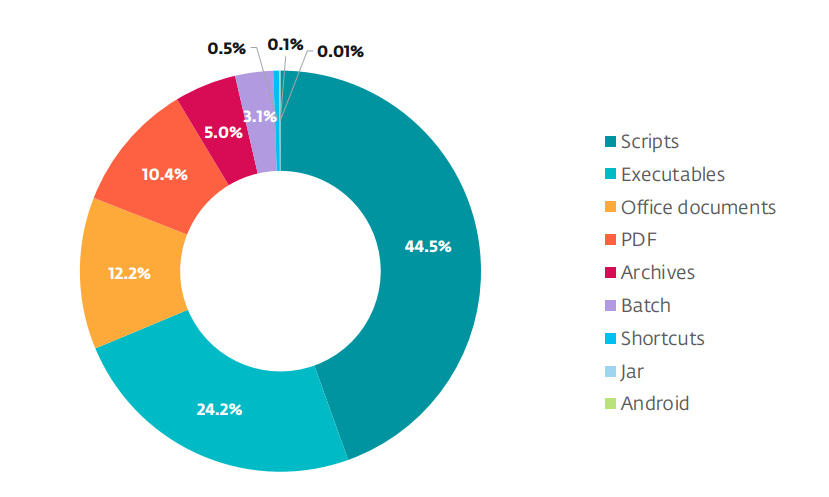
Safety researchers are seeing PDF recordsdata present up many times as lures particularly in mass social engineering campaigns, but additionally in APT group operations and even in subtle zero-day assaults. Current ESET telemetry confirms that PDFs rank among the many high file varieties abused in malicious campaigns.
A wolf in sheep’s clothes
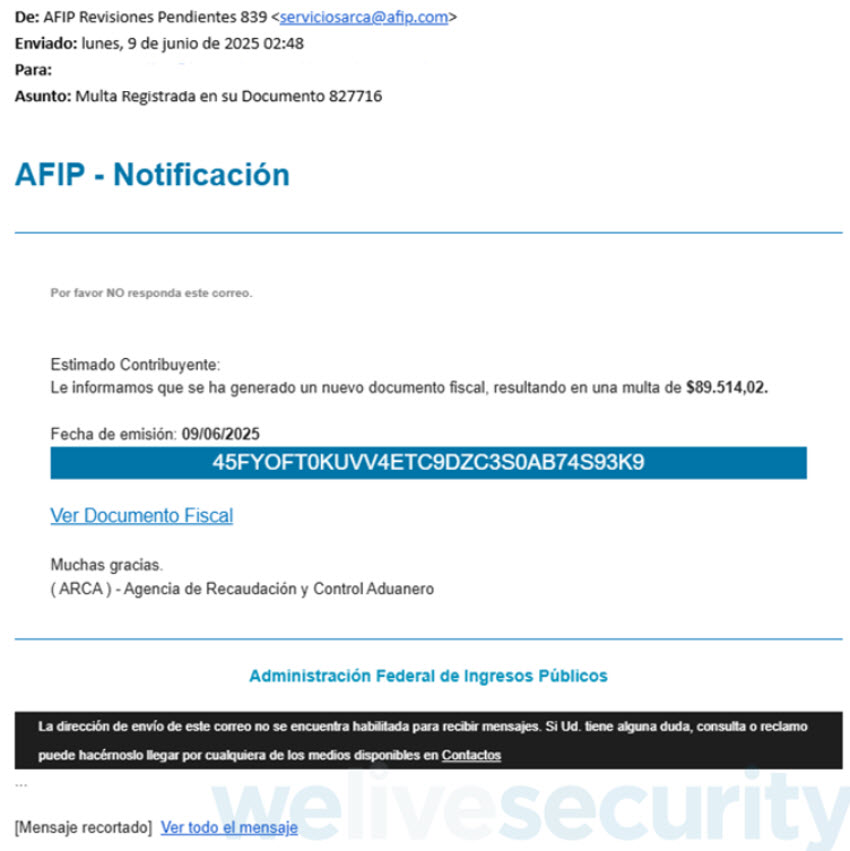
Booby-trapped PDFs sometimes arrive as e mail attachments or hyperlinks in phishing messages that trick victims into taking motion. As is frequent with social engineering campaigns, the lures are rigorously crafted to spark emotion, corresponding to urgency (suppose “remaining discover”), concern (“account suspended”) or curiosity (“take a look at outcomes out there”). The tip objective is to get you to decrease your guard and utilizing all method of exhortations, corresponding to “pay now” and “overview instantly”, strain you into opening a file or clicking a hyperlink.
The assault strategies fluctuate and have through the years included:
- Embedded scripts that run when the file opens, letting attackers launch numerous actions and deploy further payloads. JavaScript in PDFs can carry out professional duties, corresponding to creating interactive kinds and automating processes, but it surely’s additionally abused to obtain or execute code.
- Hidden or malicious hyperlinks: Hyperlinks contained within the PDF can redirect you to credential-harvesting pages or immediate you to obtain a malicious ZIP archive or executable.
- Exploiting vulnerabilities in PDF readers: Malformed objects or specifically crafted content material can reap the benefits of bugs in susceptible variations of frequent PDF readers and result in code execution, as was the case with a software program loophole affecting Adobe Reader and documented by ESET researchers.
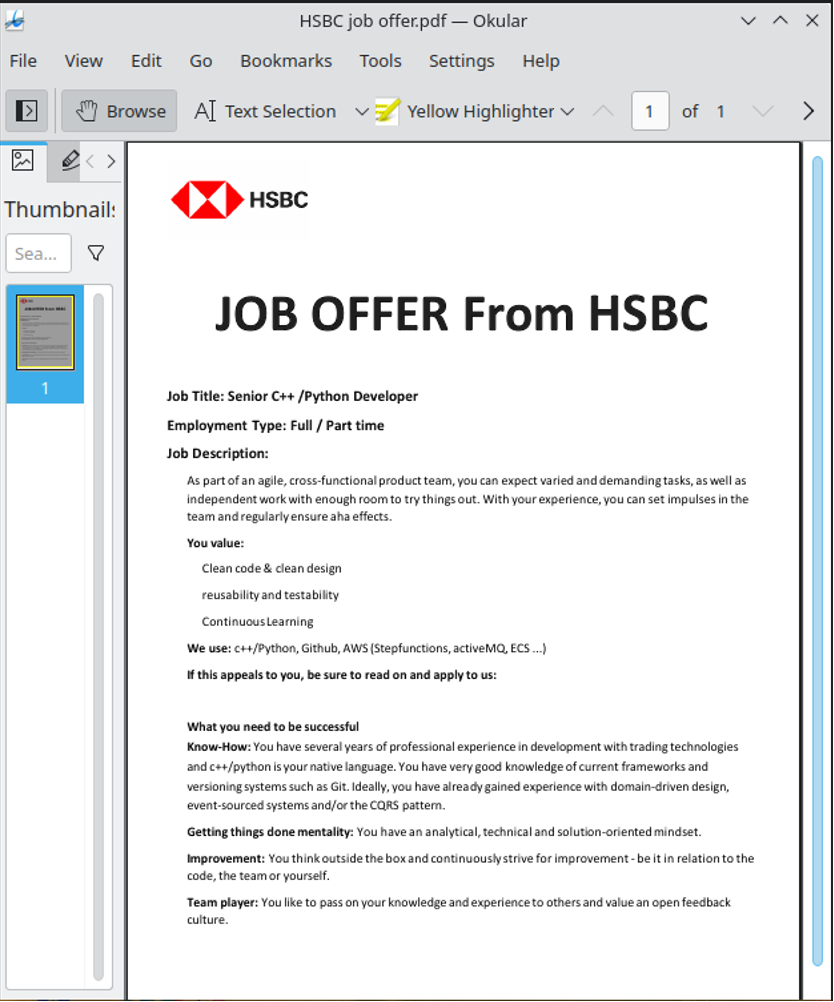
- Recordsdata that solely pose as PDFs and are as a substitute scripts, executables and even malicious Microsoft Workplace recordsdata, amongst others, however their true file extensions could also be hidden. Whereas you might even see a file known as “bill.pdf”, clicking it truly launches an executable.
Talking of which, earlier this yr we wrote a few marketing campaign that distributed the Grandoreiro banking trojan and began with an e mail urging the sufferer to open a doc, ostensibly in PDF format. In actuality, it’s a ZIP archive containing, amongst different issues, a VBScript file that unleashes Grandoreiro on the system and in the end offers criminals entry to the sufferer’s banking credentials.
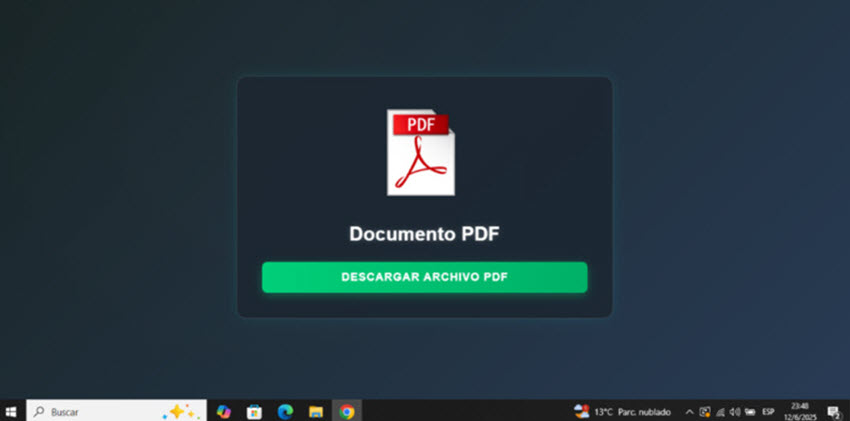
Find out how to spot a suspicious PDF
So what are the pink flags that ought to put you on excessive alert?
- The file has a deceptive seen title or double extension. That is the case with names like bill.pdf.exe or doc.pdf.scr, particularly the place attackers forged their nets vast and intend to ensnare as many individuals as attainable. These recordsdata truly aren’t PDFs in any respect – they’re simply dressed as much as appear like PDFs.
- The sender’s e mail tackle or title doesn’t match what the file says. The e-mail sender’s tackle is totally different from the group that the doc claims to be from, or the area is misspelled or suspicious.
- The PDF is compressed inside a ZIP or RAR archive. The PDF arrives inside a ZIP or RAR – that’s in a bid to bypass detection by e mail filters.
- The complete message is sudden or sounds “out of context”. Ask your self: did I ask for this file? Do I do know the sender? Does it make sense for them to ship it to me?
What to do if you happen to obtain a suspicious PDF
If a PDF raises pink flags, take these precautions:
- Resist the temptation to instantly obtain or open the file. The adage “when unsure, kick it out” works right here properly.
- Confirm the sender and context. Earlier than opening the doubtless sketchy attachment, contact the sender by a separate communication channel, corresponding to a telephone name, to examine that they’ve actually despatched it.
- Verify the file extension and measurement. Toggle “present file extensions” or related in your working system and make sure the file is an actual .pdf (not an .exe, for instance) and that the file measurement appears believable.
- Scan the file together with your safety software program (or alternatively, add it to VirusTotal to get a fast first look).
- Open with care. Should you completely should open it and have taken the opposite precautions, use an up-to-date PDF viewer with sandboxing or a protected view function enabled (corresponding to Adobe’s Protected View).
What to do if you happen to suspect you’ve opened a sketchy PDF
- Disconnect from the web to cut back the prospect of information exfiltration or additional payload downloads.
- Run a full laptop scan with an up to date safety resolution. Should you don’t have any, run a one-time examine as out there courtesy of ESET’s free scanner.
- Verify working processes and community connections for anomalies. Should you’re not skilled, get an expert to research.
- Change passwords particularly in your monetary and different worthwhile accounts, notably the place you observed your credentials might have been stolen – however accomplish that from a tool aside from the one the place you downloaded the PDF.
- Report the incident to your IT/safety workforce (in case you opened the file in your work machine).
Parting ideas
These tried-and-tested guidelines will go a good distance in direction of conserving you protected from dodgy PDFs:
- Should you weren’t anticipating the file, don’t open it, at the very least not with out checking first that the file is professional.
- Educate your self on the way to acknowledge phishing scams.
- As many assaults depend on recognized software program vulnerabilities, maintain your working system and all different software program, together with PDF readers, up-to-date.
- Allow Protected View or sandbox mode in your PDF reader of alternative and take into account adjusting or disabling your JavaScript settings in it.
- Use respected, multi-layered safety software program on all of your gadgets.
It’s protected to say that cybercriminals will proceed to take advantage of the belief we place in PDFs. Using PDFs for malicious ends can be a reminder that safety threats sometimes don’t arrive wrapped in suspicious-looking recordsdata. The tried-and-true rule applies right here, too: Deal with each sudden hyperlink and attachment with warning and depend on trusted instruments to guard your knowledge and gadgets.

