[ad_1]
Right here’s what to know in regards to the malware with an insatiable urge for food for worthwhile knowledge, a lot in order that it tops this yr’s infostealer detection charts
22 Oct 2025
•
,
3 min. learn

Infostealers stay one of the persistent threats on at this time’s risk panorama. They’re constructed to quietly siphon off worthwhile data, sometimes login credentials and monetary and cryptocurrency particulars, from compromised programs and ship it to adversaries. They usually accomplish that with nice success.
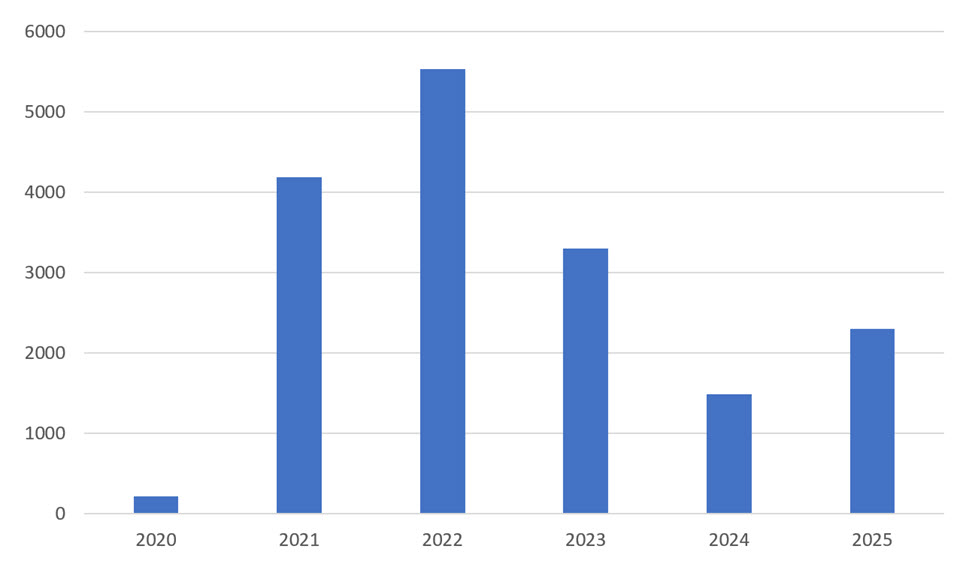
ESET researchers have tracked quite a few campaigns lately the place an infostealer was the ultimate payload. Agent Tesla, Lumma Stealer, FormBook and HoudRAT proceed to make the rounds in giant numbers, however in line with the ESET Risk Report H1 2025, one household surged forward of the remaining within the first half of this yr: SnakeStealer.
A risk is born
Detected by ESET merchandise primarily as MSIL/Spy.Agent.AES, SnakeStealer first appeared in 2019. Early reviews traced it to a risk initially marketed as 404 Keylogger or 404 Crypter on underground boards earlier than it rebranded underneath its present identify.
In its early variants, SnakeStealer used Discord to host its payloads, which victims unwittingly downloaded after opening a malicious electronic mail attachment. Whereas internet hosting malware on professional cloud platforms wasn’t new, the widespread abuse of Discord quickly grew to become an indicator tactic. SnakeStealer reached its first large wave of exercise in 2020 and 2021, spreading globally with none clear regional focus.
In the meantime, the supply strategies different. Phishing attachments nonetheless stay the first vector, however the payload itself could also be disguised in numerous varieties, together with password-protected ZIP information, weaponized RTF, ISO and PDF information, and even bundled with different malware. Sometimes, SnakeStealer hides inside pirated software program or pretend apps, which speaks to the truth that not each compromise begins with a malicious electronic mail.
Malware-as-a-service: A worthwhile ‘enterprise mannequin’
Like many different trendy threats, SnakeStealer follows the malware-as-a-service (MaaS) mannequin. Its operators lease or promote entry to the malware, full with technical help and updates, which makes it straightforward for even low-skilled attackers to launch their very own campaigns.
SnakeStealer’s current resurgence is not any coincidence. After Agent Tesla started to say no and lose developer help, underground Telegram channels began recommending SnakeStealer as its successor. This endorsement, mixed with the comfort of its MaaS setup and its ready-made infrastructure, propelled SnakeStealer to the highest of detection charts, a lot in order that SnakeStealer was lately chargeable for virtually one-fifth of worldwide infostealer detections as tracked by ESET telemetry.

Key options
SnakeStealer might not break new floor, nevertheless it’s polished, dependable, and straightforward to deploy. It affords a full toolkit of capabilities that’s typical of professional-grade info-stealing malware, and given its modularity, attackers can swap options on or off to go well with their wants.
- Evasion: With a purpose to keep underneath the radar, SnakeStealer can terminate processes related to safety and malware evaluation instruments and verify for digital environments.
- Persistence: It alters Home windows boot configurations to take care of entry on compromised programs.
- Credential theft: It extracts saved passwords from internet browsers, databases, electronic mail and chat purchasers, together with Discord, and Wi-Fi networks.
- Surveillance: It captures clipboard knowledge, takes screenshots and logs keystrokes.
- Exfiltration: It sends stolen knowledge by way of FTP, HTTP, electronic mail, or Telegram bots.
How you can shield your self
Whether or not you’re a person person or a enterprise, these steps may help cut back the chance towards infostealers like SnakeStealer:
- Be skeptical of unsolicited messages. Deal with attachments and hyperlinks, particularly from unknown senders, as potential threats, even when they seem professional. Confirm them with the sender by way of different channels.
- Hold your system and apps up to date. Patching identified vulnerabilities in a well timed method reduces the chance of compromise stemming from software program loopholes.
- Allow multi-factor authentication (MFA) wherever attainable. Even when your password is stolen, MFA can cease unauthorized logins.
- When you suspect a compromise: change all passwords from a clear machine, revoke open classes, and monitor your accounts for suspicious exercise.
- Use respected safety software program on all units, desktop and cell alike.
Ultimate ideas
SnakeStealer’s rise is a reminder of how shortly the cybercrime market adapts and as such displays a bigger fact about at this time’s risk panorama: cybercrime has industrialized. This professionalization makes it simpler than ever for anybody to steal knowledge at scale. And as one infostealer fades, one other fills the hole, armed with largely the identical tried-and-tested techniques. The excellent news is that robust cybersecurity practices will go a great distance in direction of maintaining you secure.
[ad_2]



