A complicated cybercrime marketing campaign leveraging Close to Area Communication know-how has exploded throughout a number of continents, with researchers at zLabs figuring out over 760 malicious Android purposes designed to steal banking credentials and facilitate fraudulent transactions.
What initially appeared as remoted incidents in April 2024 has advanced right into a large-scale risk operation focusing on monetary establishments throughout Russia, Poland, the Czech Republic, Slovakia, Brazil, and past.
The malware ecosystem operates via an intensive infrastructure comprising greater than 70 command-and-control servers, dozens of personal Telegram channels for information exfiltration, and purposes impersonating roughly 20 authentic banking establishments and authorities companies.
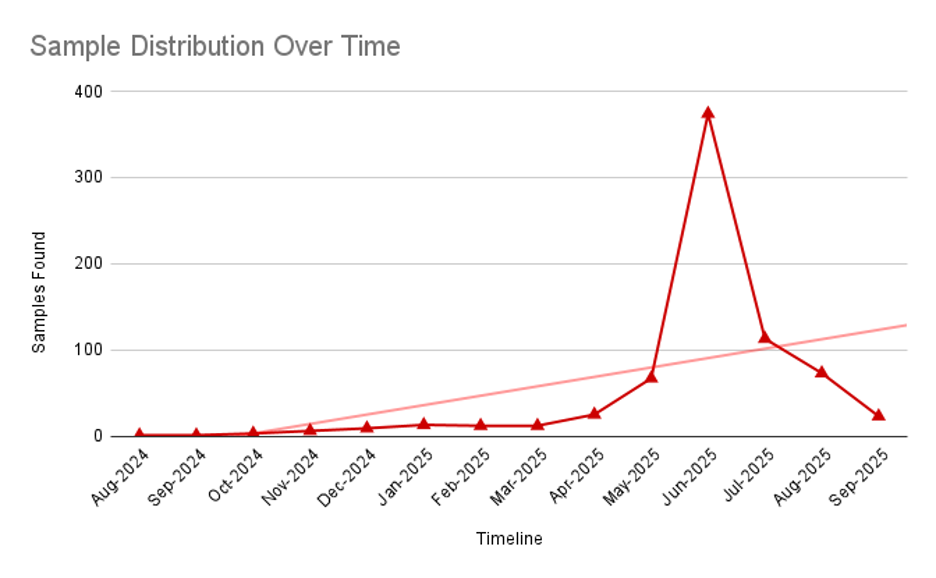
Safety researchers monitoring these campaigns have documented a gradual improve in malicious samples all through 2024, indicating that risk actors are repeatedly refining their methods and increasing their geographic attain.
These malicious purposes make use of social engineering by masquerading as authentic companies from main monetary establishments and authorities companies.
Risk actors have impersonated distinguished organizations together with VTB Financial institution, Tinkoff Financial institution, Santander, PKO Financial institution Polski, Bradesco, Itaú, and even authorities companies like Russia’s Gosuslugi portal and regulatory our bodies such because the Central Financial institution of Russia and Nationwide Financial institution of Slovakia.
By replicating the branding and interfaces of those trusted entities, attackers efficiently trick victims into granting the purposes harmful NFC permissions.
The malware leverages Android’s Host Card Emulation performance to intercept cost information when customers try contactless transactions.
As soon as put in, these purposes request to turn into the default NFC cost methodology whereas displaying convincing full-screen banking interfaces—usually rendered inside WebViews to reinforce authenticity.
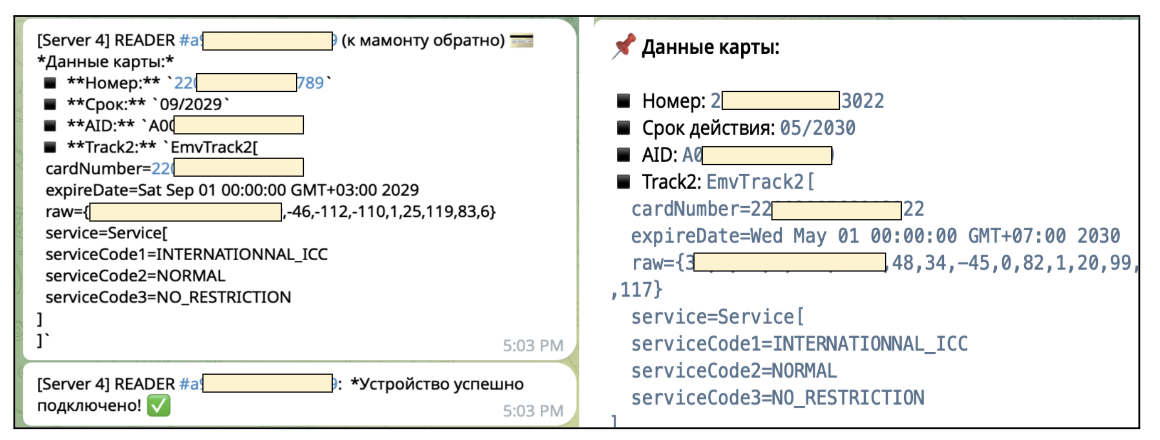

Behind this facade, background companies silently seize card numbers, expiration dates, and significant EMV information fields transmitted throughout cost makes an attempt.
From Information Theft to Automated Fraud Operations
Operational strategies differ throughout totally different risk actor teams. Some campaigns deploy paired purposes the place one instrument extracts card information whereas one other interfaces with point-of-sale methods to finish fraudulent purchases.
Different variants focus completely on information exfiltration, robotically transmitting stolen credentials to non-public Telegram channels the place cybercriminals obtain structured messages containing gadget identifiers, full card particulars, and transaction metadata.
The malware maintains persistent communication with command-and-control infrastructure via an intensive protocol of instructions together with gadget registration, APDU relay for terminal communication, PIN harvesting, and standing monitoring.
Instructions like “apdu_command” and “apdu_response” allow real-time relay assaults the place the malicious app forwards cost terminal requests to distant servers managed by attackers, successfully permitting criminals to conduct transactions utilizing victims’ cost credentials from wherever on the earth.
Cybercriminal boards have adopted the Russian slang time period “Mamont”—that means mammoth—to discuss with victims of those schemes, underscoring the organized nature of those operations and their roots in Jap European cybercrime networks.
Rising Risk Calls for Heightened Vigilance
The speedy proliferation of NFC-based cost malware displays cybercriminals adaptation to the growing adoption of contactless cost applied sciences.
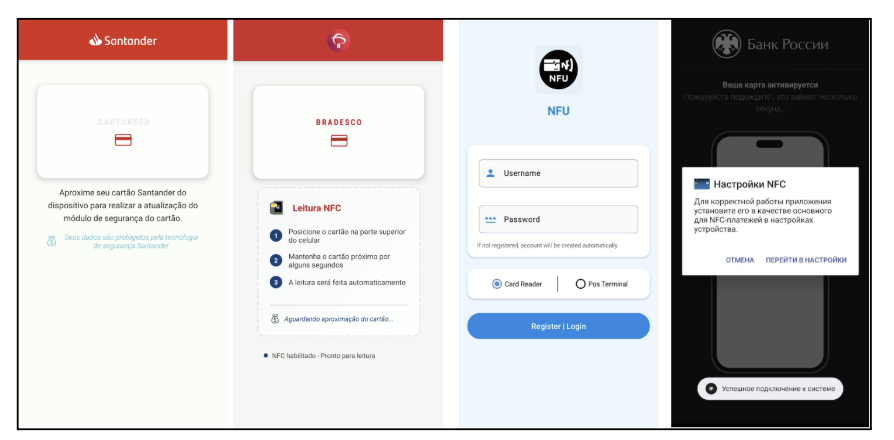

As “Faucet-to-Pay” transactions turn into ubiquitous globally, the assault floor for NFC exploitation continues to develop.
The dimensions of this risk—evidenced by a whole bunch of malicious purposes, intensive server infrastructure, and coordinated Telegram-based command channels—demonstrates that that is now not experimental exercise however moderately a longtime and worthwhile legal enterprise.
Monetary establishments should improve fraud detection methods to determine anomalous NFC transaction patterns, whereas cell gadget producers ought to implement stricter controls round NFC permissions.
Customers ought to train excessive warning earlier than granting any utility entry to NFC cost performance, significantly when putting in apps from unofficial sources or unfamiliar builders requesting payment-related privileges.
Comply with us on Google Information, LinkedIn, and X to Get Immediate Updates and Set GBH as a Most popular Supply in Google.

