A vulnerability in Verizon’s Name Filter characteristic allowed prospects to entry the incoming name logs for one more Verizon Wi-fi quantity by an unsecured API request.
The flaw was found by safety researcher Evan Connelly on February 22, 2025, and was fastened by Verizon someday within the following month. Nevertheless, the full interval of publicity is unknown.
Verizon’s Name Filter app is a free utility that gives customers spam detection and computerized name blocking. A paid model (Plus) provides a spam lookup and danger meter, the flexibility to use blocks by sort of caller, and obtain caller ID on unknown numbers.
The free model of the app comes pre-installed and enabled by default on eligible Android and iOS units purchased straight from Verizon, and is believed for use on thousands and thousands of units.
Connelly advised BleepingComputer that he solely examined the iOS app. Nevertheless, he famous that the Android app was additionally very probably impacted by the identical bug, as the problem was with the characteristic’s API reasonably than the apps themselves.
Exposing name histories
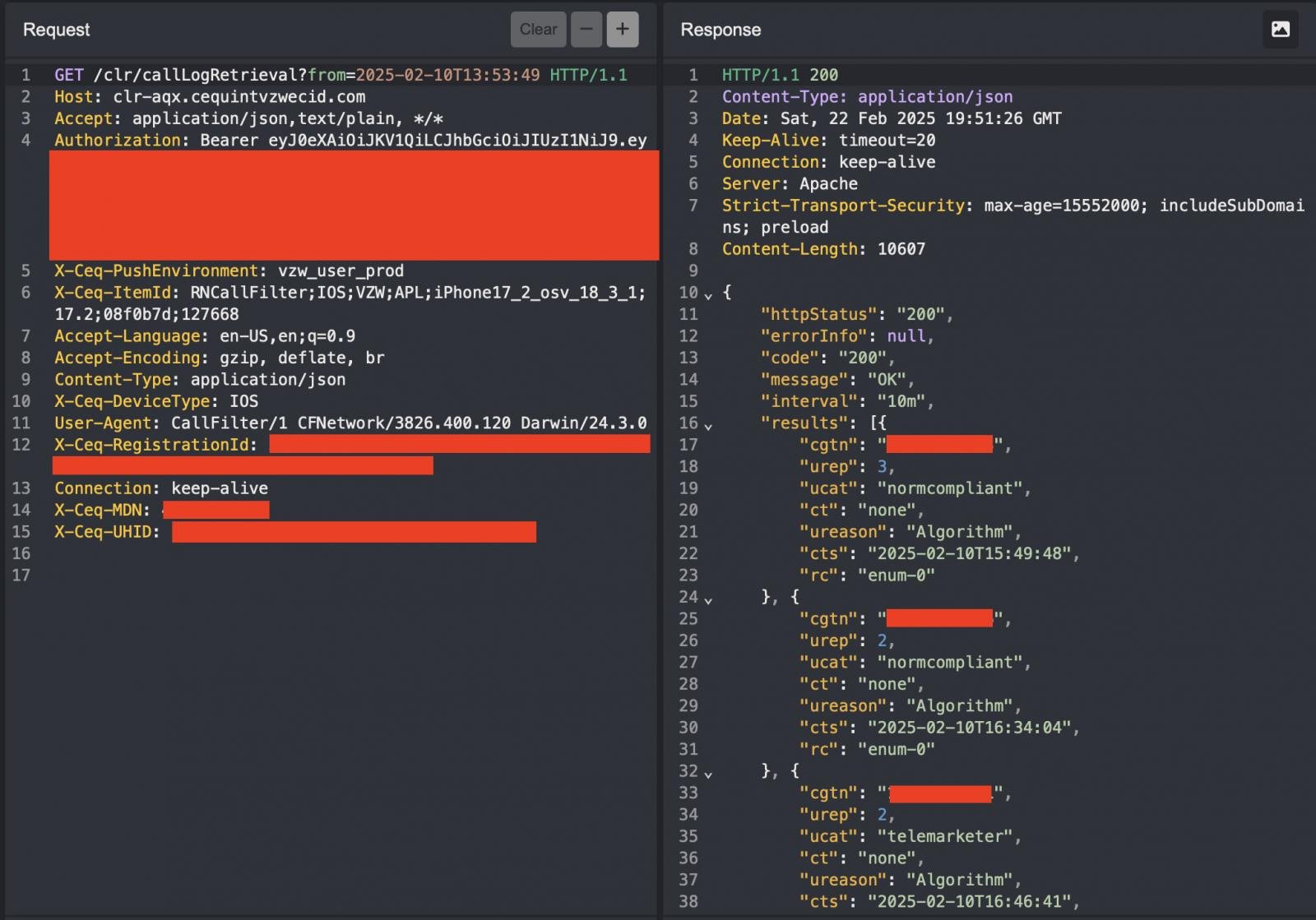
When utilizing the Name Filter app, Connelly found that the app would connect with an API endpoint, https://clr-aqx.cequintvzwecid.com/clr/callLogRetrieval, to retrieve the logged-in person’s incoming name historical past and show it within the app.
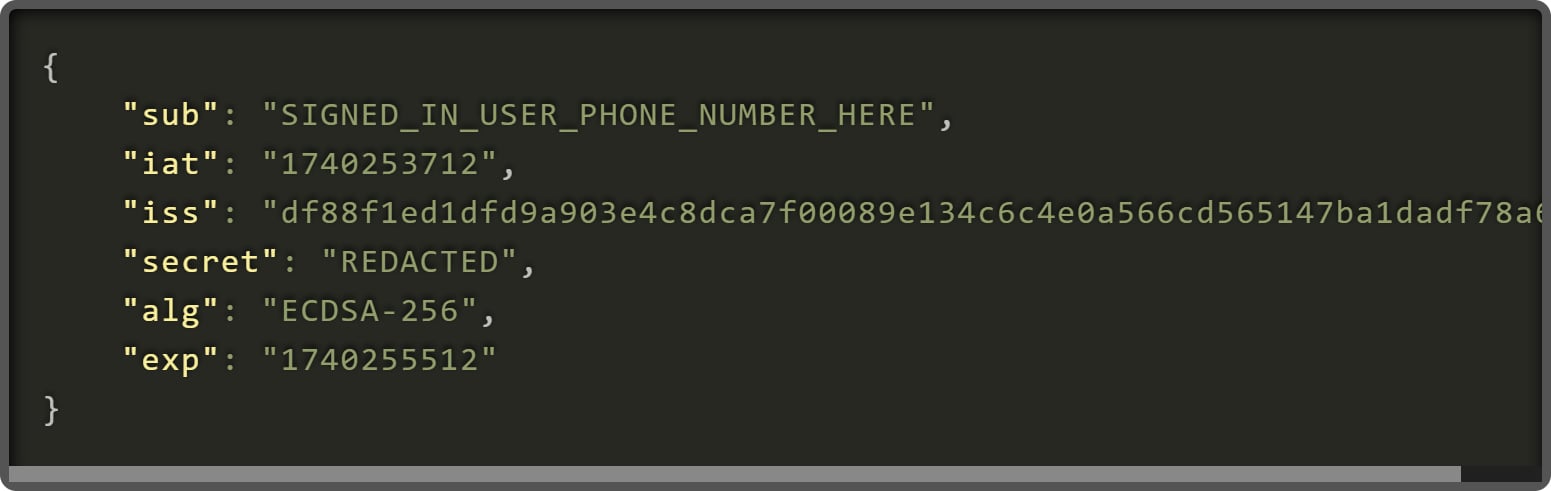
“This endpoint requires a JWT (JSON Net Token) within the Authorization header utilizing the Bearer scheme and makes use of an X-Ceq-MDN header to specify a cellphone quantity to retrieve name historical past logs for,” explains Connelly.
“A JWT has three components: header, payload, and signature. It is typically used for authentication and authorization in internet apps.”
Connelly says the payload contains numerous information, together with the telephone variety of the logged-in person making the request to the API.
Supply: Connelly
Nevertheless, the researcher found that the telephone quantity within the JWT payload for the logged-in person was not verified towards the telephone quantity whose incoming name logs have been being requested.
Because of this, any person might ship requests utilizing their very own legitimate JWT token, however exchange the X-Ceq-MDN header worth with one other Verizon telephone to retrieve their incoming name historical past.
Supply: evanconnelly.github.io
This flaw is especially delicate for high-value targets like politicians, journalists, and regulation enforcement brokers, as their sources, contacts, and day by day routines may very well be mapped out.
“Name metadata may appear innocent, however within the unsuitable arms, it turns into a robust surveillance device. With unrestricted entry to a different person’s name historical past, an attacker might reconstruct day by day routines, establish frequent contacts, and infer private relationships,” defined Connelly.
It’s unclear if price limiting was in place to forestall mass scraping for thousands and thousands of subscribers, however Connolly advised BleepingComputer he noticed no indication of such a mechanism or an API gateway that often implements a safety characteristic like this.
Poor safety practices
Though the researcher commends Verizon for its immediate response to his disclosure, he highlighted worrying practices the telecom agency has adopted in dealing with subscribers’ name information.
The weak API endpoint utilized by Name Filter seems to be hosted on a server owned by a separate telecommunications expertise agency referred to as Cequint, which makes a speciality of caller identification companies.
Cequint’s personal web site is offline, and public details about them is restricted, elevating issues about how delicate Verizon name information is dealt with.
BleepingComputer contacted Verizon to ask when the flaw was launched, if it was seen exploited prior to now, and if it impacted all Name Filter customers however has not acquired a response right now.


