A provide chain assault on the broadly used ‘tj-actions/changed-files’ GitHub Motion, utilized by 23,000 repositories, doubtlessly allowed risk actors to steal CI/CD secrets and techniques from GitHub Actions construct logs.
The GitHub Motion is a very talked-about automation instrument designed for GitHub Actions workflows. It permits builders to establish information modified in a pull request or commit and take actions primarily based on these modifications, typically utilized in testing, workflow triggering, and automatic code linting and validation.
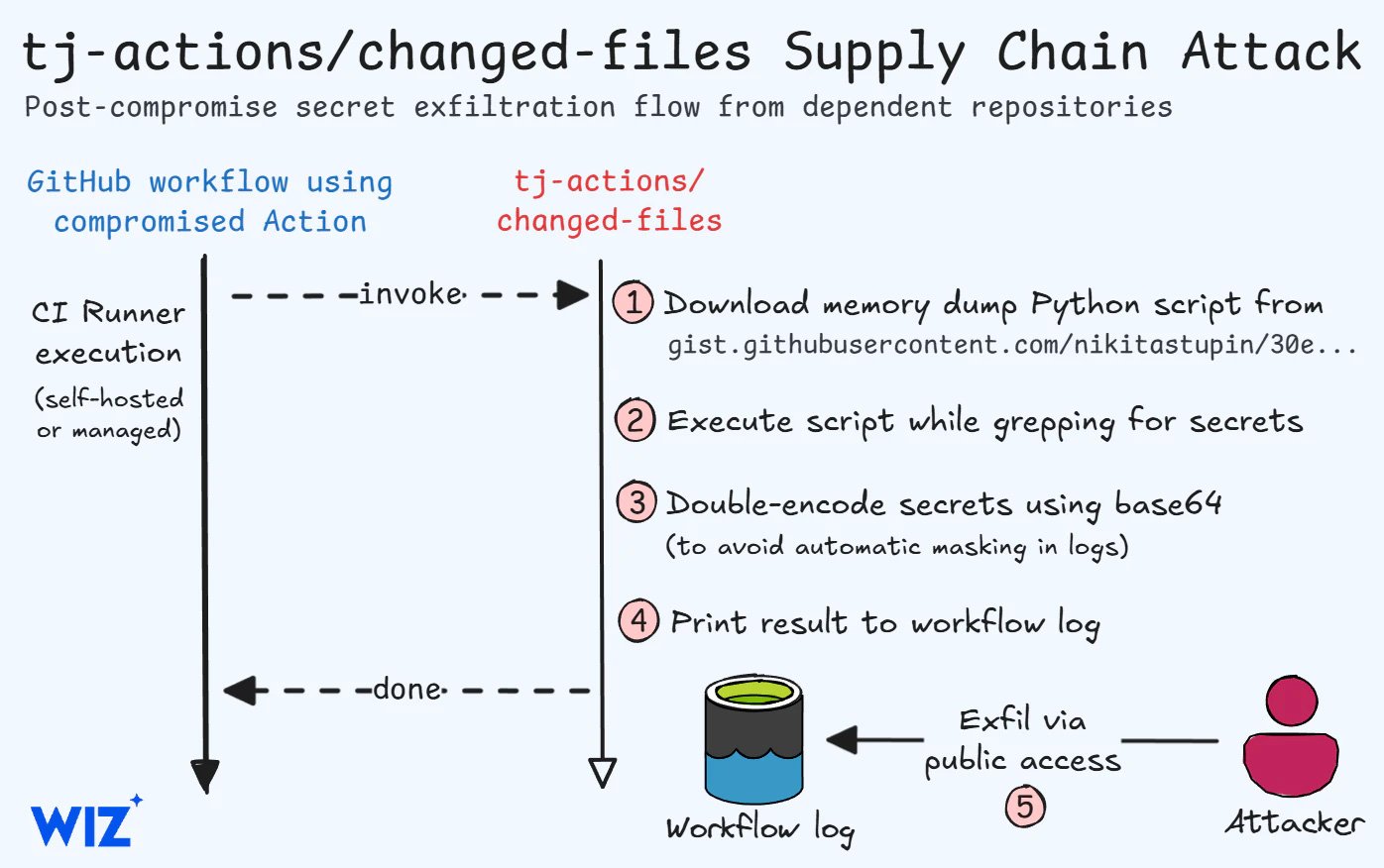
As first reported by StepSecurity, attackers added a malicious decide to the instrument on March 14, 2025, at 4:00 PM UTC, that dumped CI/CD secrets and techniques from the Runner Employee course of to the repository of any initiatives utilizing the motion. Because of this, if workflow logs have been publicly accessible, anybody might learn and steal uncovered secrets and techniques.
Attackers modified the motion’s code and retroactively up to date a number of model tags to reference a malicious commit, so all variations of the instrument have been compromised.
As per the newest replace by the builders, the attacker compromised a GitHub private entry token (PAT) utilized by a bot (@tj-actions-bot), which had privileged entry to the instrument’s repository. Nevertheless, it’s at the moment unclear how precisely the PAT was compromised.
On March 15, 2:00 PM UTC, GitHub eliminated the compromised motion, and at 10:00 PM UTC on the identical day, the repository was restored with the malicious code having been eliminated.
Nevertheless, the compromise has lasting repercussions for impacted software program initiatives, so a CVE ID (CVE-2025-30066) was assigned to the incident for monitoring.
Unusually, the malicious code didn’t exfiltrate the reminiscence output to a distant server, as a substitute solely making it seen in publicly accessible repositories.
“The compromised motion injected malicious code into any CI workflows utilizing it, dumping the CI runner reminiscence containing the workflow secrets and techniques,” explains Wiz in a write-up on the incident.
“On public repositories, the secrets and techniques would then be seen to everybody as a part of the workflow logs, although obfuscated as a double-encoded base64 payload.”
Supply: Wiz
The restored tj-actions repository was up to date earlier at the moment to embody directions on what doubtlessly impacted customers have to do, which embody:
- Rotate any secrets and techniques used through the assault’s timeframe (March 14-15)
- Assessment Workflows to surprising output underneath the ‘changed-files’ part
- In case your workflows reference the compromised commit by SHA, replace them instantly.
- Be sure you at the moment are utilizing a tagged model (e.g., v35, v44.5.1)
To forestall secrets and techniques from being uncovered to comparable compromises sooner or later, it’s GitHub recommends that every one GitHub Actions be pinged to particular commit hashes as a substitute of model tags.
Additionally, GitHub gives allow-listing performance that may be leveraged to dam unauthorized/non-trusted GitHub Actions.


