Amazon Internet Companies’ Easy Notification Service (AWS SNS) is a flexible cloud-based pub/sub service that facilitates communication between functions and customers.
Whereas its scalability and integration capabilities make it a strong device for organizations, its misuse by adversaries for malicious functions similar to information exfiltration and phishing has raised vital safety issues.
This text delves into the mechanisms by which AWS SNS may be exploited, explores real-world abuse eventualities, and offers actionable insights into detection and prevention methods.
By understanding the vulnerabilities inherent in SNS configurations and leveraging strong detection methodologies, organizations can mitigate dangers and improve their cloud safety posture.
Understanding AWS SNS: A Double-Edged Sword
AWS Easy Notification Service (SNS) is a cloud-based pub/sub communication service that permits customers to ship notifications to subscribers by way of numerous endpoints similar to e mail, SMS, or cellular push notifications.
It operates on two main workflows: application-to-person (A2P) and application-to-application (A2A).
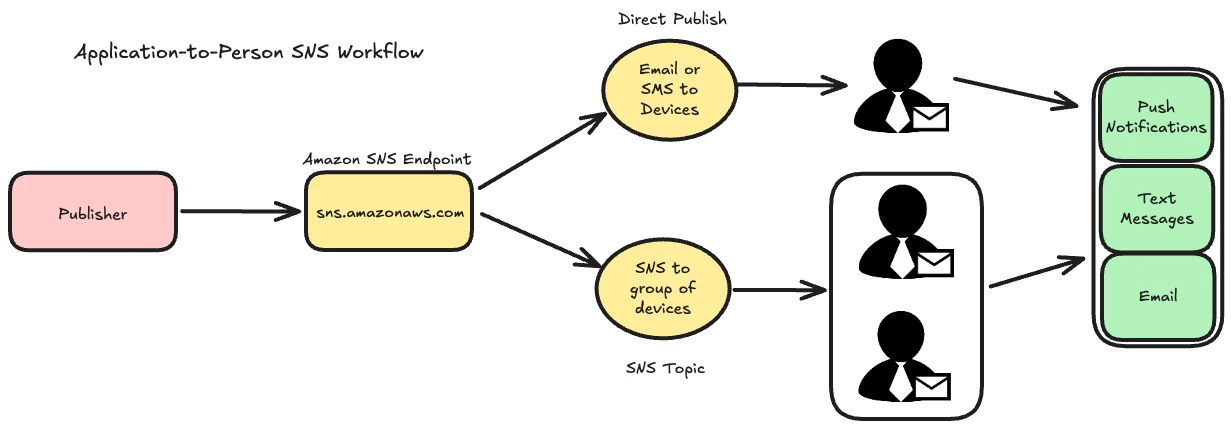
Whereas A2P workflows are designed to combine seamlessly with AWS companies like Lambda and SQS, in addition they function potential vectors for abuse when misconfigured.


Options similar to filter insurance policies, server-side encryption (SSE), supply retries, and lifeless letter queues (DLQs) improve the performance of SNS however can be exploited by adversaries.
The scalability of SNS permits it to deal with large message volumes with out handbook intervention, making it cost-effective for organizations.
Nevertheless, this scalability additionally implies that adversaries can leverage the service for large-scale malicious actions similar to phishing campaigns or information exfiltration.
Regardless of its strong structure, AWS SNS is prone to abuse resulting from misconfigurations in IAM roles, inadequate monitoring of API actions, and gaps in logging mechanisms.
For example, adversaries can exploit permissive IAM insurance policies to create subjects, subscribe exterior endpoints, and publish delicate information with out triggering alarms.
The dearth of visibility into sure API actions—similar to failed Publish requests—additional complicates detection efforts.
Encryption mechanisms in SNS focus totally on securing information at relaxation utilizing AWS Key Administration Service (KMS).
Whereas this ensures the safety of delicate data similar to Personally Identifiable Data (PII), adversaries can bypass these safeguards by exploiting encryption gaps throughout information transit or leveraging unmonitored endpoints.
Whitebox Testing: Simulating Malicious Conduct
Whitebox testing offers a managed setting to emulate adversarial behaviors and validate detection capabilities.
Not like endpoint-based simulations that depend on malware binaries, cloud-focused whitebox testing exploits present API-driven companies by “living-off-the-cloud” strategies.
This strategy is especially efficient for analyzing ways, strategies, and procedures (TTPs) focusing on AWS companies like SNS.
In a current whitebox train, researchers simulated information exfiltration utilizing SNS by creating a subject that served as a proxy for forwarding stolen credentials to exterior endpoints.
This methodology bypassed conventional safety mechanisms similar to community ACLs and demonstrated the benefit with which adversaries may exploit misconfigured infrastructure.
Knowledge Exfiltration Workflow
Adversaries usually observe a scientific workflow to exfiltrate delicate information by way of AWS SNS:
- Preliminary Entry: Gaining entry into an EC2 occasion by strategies like exploiting weak internet functions or utilizing stolen credentials.
- Credential Discovery: Figuring out delicate data saved regionally in recordsdata similar to
.envor GitHub credential recordsdata. - Matter Creation: Utilizing short-term credentials obtained from IMDSv2 to create an SNS matter.
- Subscription Setup: Registering exterior e mail addresses or cellular numbers as subscribers to the subject.
- Knowledge Publishing: Encoding delicate information in Base64 format and publishing it to the subject for distribution.
This workflow highlights the minimal effort required to stage an assault as soon as preliminary entry is achieved.


By leveraging native AWS companies like CLI instructions and IAM roles, adversaries can mix their actions into reliable site visitors patterns.
Probably the most regarding functions of AWS SNS abuse is its use in smishing (SMS phishing) campaigns.


SentinelOne’s analysis uncovered situations the place adversaries employed Python-based instruments like SNS Sender to distribute fraudulent messages at scale utilizing compromised AWS credentials.
These campaigns leveraged authenticated API requests to bypass safeguards and ship phishing messages impersonating trusted entities.
The success of such campaigns hinges on the adversary’s capability to ascertain production-level messaging permissions inside AWS Finish Person Messaging companies.
This requires regulatory approval for origination identities and provider pre-approval for high-volume SMS messaging a hurdle that refined attackers can overcome by compromising accounts with pre-existing permissions.
Whereas the abuse of AWS SNS presents vital benefits for adversaries—similar to mixing into reliable site visitors and bypassing egress monitoring it additionally poses challenges:
- Preliminary Entry: Exploiting vulnerabilities in EC2 situations or buying credentials by social engineering.
- Session Persistence: Sustaining energetic classes amidst strong endpoint protections.
- Infrastructure Setup: Configuring IAM roles with permissive insurance policies for SNS actions.
- Sandbox Restrictions: Overcoming limitations imposed by AWS on new accounts restricted to SMS sandbox mode.


These challenges underscore the significance of proactive safety measures similar to hardening IAM insurance policies and monitoring CloudTrail logs for anomalies.
Detection Methods and Menace Looking
CloudTrail audit logs function a significant useful resource for detecting uncommon API actions associated to SNS abuse.
By specializing in assumed roles connected to EC2 situations, safety groups can establish anomalies similar to uncommon matter creation or subscription occasions.
Detection guidelines may be crafted utilizing Elastic’s New Phrases logic to flag first occurrences of suspicious actions:
- Matter Creation by Uncommon Person: Figuring out when an assumed position creates an SNS matter unexpectedly.
- Subscription with Exterior Electronic mail: Monitoring subscriptions that specify exterior endpoints.
- Message Publishing Spikes: Detecting sudden will increase in direct-to-phone messaging exercise.


These guidelines allow organizations to pinpoint potential abuse eventualities whereas minimizing false positives by contextual evaluation.
Looking Queries
Menace searching queries present deeper insights into potential compromises by parsing CloudTrail logs for particular attributes similar to user-agent strings or request parameters.
For instance:
- Uncommon Matter Creation: Aggregating information based mostly on EC2 occasion IDs and areas to establish uncommon exercise.
- Electronic mail Subscriptions: Filtering subscriptions by protocol sort to detect unauthorized exterior endpoints.
- Direct Messaging Spikes: Monitoring Publish actions with cellphone numbers in request parameters to uncover smishing campaigns.


These queries assist safety groups prioritize investigations based mostly on anomalous alerts whereas refining detection logic over time.


AWS SNS is a strong communication device that provides immense utility for organizations but additionally presents vital dangers if left unmonitored or misconfigured.
The analysis outlined above highlights how adversaries can exploit its options for malicious functions similar to information exfiltration and phishing campaigns.
By understanding these vulnerabilities and implementing strong detection methods utilizing CloudTrail logs and risk searching queries, organizations can mitigate dangers successfully.
Key suggestions embody:
- Hardening IAM insurance policies with principle-of-least-privilege (PoLP).
- Enabling complete logging mechanisms throughout CloudTrail and CloudWatch.
- Crafting anomaly-based detection guidelines tailor-made to organizational contexts.
- Conducting common whitebox testing workouts to validate safety controls.
As cloud environments proceed to evolve, staying proactive in monitoring rising threats might be essential for sustaining strong safety postures towards adversarial abuse of companies like AWS SNS.
Discover this Information Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Prompt Updates!

