A Proof-of-Idea (PoC) has been launched for a major vulnerability found in SolarWinds Internet Assist Desk, exposing encrypted passwords and different delicate knowledge.
This vulnerability arises from the predictable encryption keys used within the software and the misuse of AES-GCM encryption, a extensively revered cryptographic customary.
The problem highlights the significance of safe key administration and correct encryption practices in software program improvement.
AES-GCM (Galois/Counter Mode) is an authenticated encryption mode that gives each confidentiality and integrity. Nonetheless, it requires distinctive nonces (initialization vectors) for every encryption operation.
If the identical key and nonce are reused, an attacker can exploit this to recuperate the encryption keystream and decrypt different ciphertexts with out understanding the important thing.
Vulnerability in SolarWinds Internet Assist Desk
As per the NetSPI report, the vulnerability impacts Internet Assist Desk customers who make the most of AES-GCM encryption for securing delicate knowledge reminiscent of database connection passwords, LDAP question passwords, and SMTP e mail passwords. The problem is twofold:
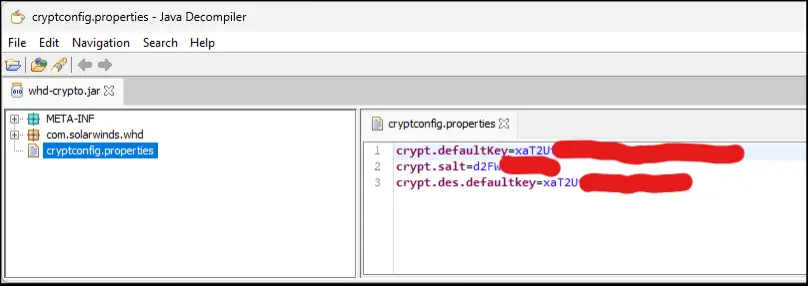
- Predicable Encryption Keys: The encryption keys utilized by Internet Assist Desk are comparatively straightforward to recuperate. The default secret is embedded within the software’s supply code and may be accessed by decompiling the software program. Extra keys are derived from database knowledge and supply code, however these transformations supply little safety attributable to a small key area.
- Reuse of Key and Nonce: The applying usually reuses keys and nonces throughout a number of encryption operations. This misuse of AES-GCM permits attackers to recuperate the keystream via recognized plaintext assaults, enabling them to decrypt any ciphertext encrypted with the identical key and nonce.
Exploitation Instance
In a single case, a recognized ciphertext and plaintext pair have been used to compute the keystream through XOR.
This keystream was then utilized to an unknown ciphertext to retrieve its plaintext, demonstrating how simply an attacker can exploit this vulnerability.
# Simplified Python code to display keystream restoration and decryption
def xor_keystream(plaintext, ciphertext):
keystream = bytearray()
for p, c in zip(plaintext, ciphertext):
keystream.append(p ^ c)
return keystream
# Recognized plaintext and ciphertext pair
known_plaintext = b'x00x00x00x09Password1'
known_ciphertext = b'frcLMeS3nchpg_Ucxz-evzlfNUlfHLnpvKyjAYisVLmlEtyZ2ZFRRiVw7Kd5KQbR'
keystream = xor_keystream(known_plaintext, known_ciphertext)
# Use keystream to decrypt unknown ciphertext
unknown_ciphertext = b'your_unknown_ciphertext_here'
unknown_plaintext = bytearray()
for uc, ks in zip(unknown_ciphertext, keystream):
unknown_plaintext.append(uc ^ ks)
print("Unknown Plaintext:", unknown_plaintext.decode('utf-8'))Suggestions and Impression
To mitigate this vulnerability, it’s essential for customers to improve their Internet Assist Desk software program to the newest model.
Furthermore, backup information containing delicate knowledge must be secured with entry restricted to solely vital personnel.
The invention of this vulnerability highlights the necessity for strong key administration practices and adherence to encryption requirements in software program improvement.
In conclusion, the discharge of the PoC for the SolarWinds Internet Assist Desk vulnerability serves as a reminder of the significance of safe coding practices and accountable disclosure of vulnerabilities.
As software program continues to play a central position in managing delicate knowledge, guaranteeing that encryption is applied appropriately will turn into more and more important to defending consumer privateness and stopping knowledge breaches.
Are you from SOC/DFIR Groups? – Analyse Malware Incidents & get stay Entry with ANY.RUN -> Begin Now for Free.

