Microsoft has eliminated two widespread VSCode extensions, ‘Materials Theme – Free’ and ‘Materials Theme Icons – Free,’ from the Visible Studio Market for allegedly containing malicious code.
The 2 extensions are very fashionable, having been downloaded practically 9 million instances in complete, with customers now receiving alerts in VSCode that the extensions have routinely been disabled.
The writer, Mattia Astorino (aka equinusocio), has a number of extensions on the VSCode market, totaling over 13 million installs.
Information of the extensions being malicious comes from cybersecurity researchers Amit Assaraf and Itay Kruk, who’ve experience in scanning VSCode for malicious extensions.
In a report printed as we speak, the researchers say they found suspicious code within the extensions and reported their findings to Microsoft.
“Microsoft eliminated each extensions from the VS Code market and banned the developer,” reads a submit from a Microsoft worker to YCombinator’s Hacker Information.
“A member of the neighborhood did a deep safety evaluation of the extension and located a number of crimson flags that point out malicious intent and reported this to us. Our safety researchers at Microsoft confirmed this claims and located further suspicious code.”
“We banned the writer from the VS Market and eliminated all of their extensions and uninstalled from all VS Code cases which have this extension working. For readability – the removing had nothing to do about copyright/licenses, solely about potential malicious intent.”
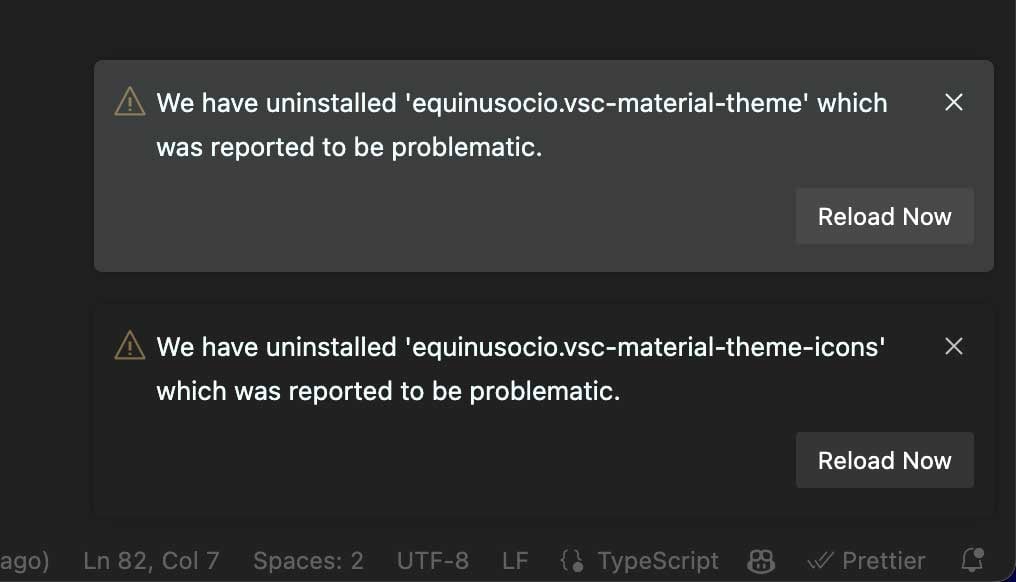
Supply: bsdahl
The researchers instructed BleepingComputer that their specialised scanner detected malicious exercise within the extension’s code. One of many researchers, Amit Assaraf, says they consider the malicious code was launched in an replace to the extensions, indicating both a provide chain assault via a dependency or the developer’s account was compromised.
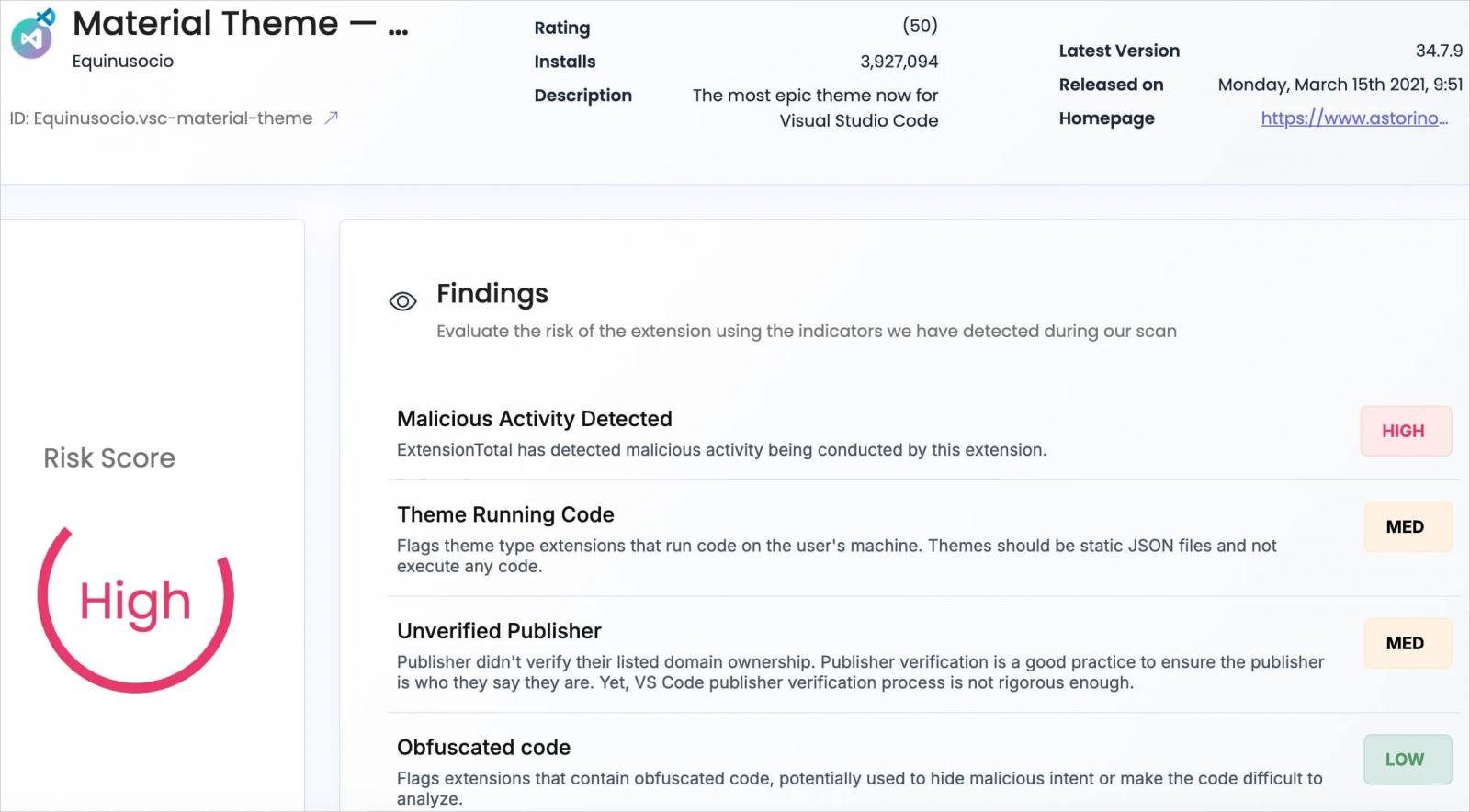
Supply: app.extensiontotal.com
Furthermore, they defined that themes ought to be static JSON information and never execute any code, so this habits was marked as suspicious of their analysis.
As verified by BleepingComputer, the “release-notes.js” information within the theme include closely obfuscated JavaScript, which is all the time a crimson flag in open-source software program.
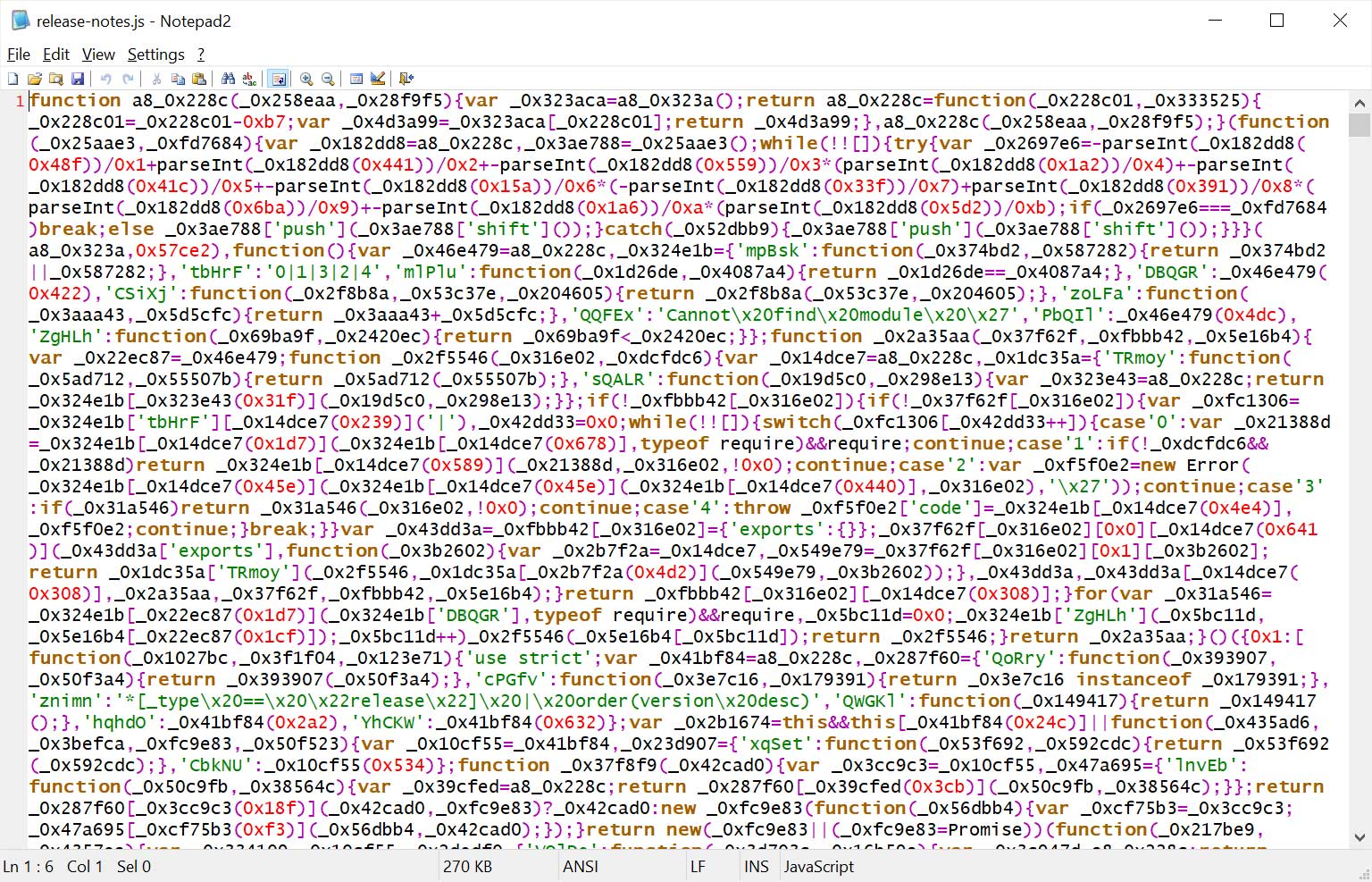
Supply: BleepingComputer
A partial deobfuscation of the code confirmed quite a few references to usernames and passwords. Nevertheless, because the file was nonetheless closely obfuscated, BleepingComputer couldn’t decide in what method they had been being referenced.
Microsoft says they may publish extra particulars concerning the extension and any detected malicious exercise to the VSMarketplace GitHub repository quickly.
The developer of the extensions, Mattia Astorino (aka equinusocio), responded to considerations concerning the extensions being malicious, stating that the problems are attributable to outdated Sanity.io dependency that “seems compromised.”
“Expensive @gegtor nothing dangerous was ever shipped inside Materials Theme.,” reads a submit from Astorino in Microsoft’s VSMarketplace repository.
“We simply had an outdated sanity.io dependency used since 2016 to indicate launch notes from sanity headless CMS, that was the one problem they discovered.”
“That dependency has been there since 2016 and handed each examine since then, now it seems compromised however NO ONE from Microsoft reached us to take away it. They only pulled down every part inflicting points to hundreds of thousands of customers, and inflicting a loop in vscode (yep, it is their fault)”
“They broke every part with out ever reaching out to us for clarification. Eradicating the outdated dependency was a fast 30-second repair, however plainly’s simply how Microsoft operates. We additionally ship an obfuscated index.js file that comprises all of the theme instructions and logic. It is obfuscated as a result of the extension is now closed-source; nonetheless, in case you delete it, the extension will nonetheless perform with plain JSON information.”
Till the scenario clears up and it is decided whether or not or not the extensions are malicious, it is suggested to take away the next from all initiatives:
- equinusocio.moxer-theme
- equinusocio.vsc-material-theme
- equinusocio.vsc-material-theme-icons
- equinusocio.vsc-community-material-theme
- equinusocio.moxer-icons
The developer, Astorino, later printed what they declare is a “fully rewritten extension” with none dependencies named “Fanny Themes” to the VSCode Market, which Microsoft subsequently eliminated.
In response to our questions concerning the obfuscated release-notes.js file, Astorino repeated what he posted to GitHub, stating {that a} @sanity dependency was compromised and will have been rapidly eliminated if he had been notified.
“The discharge notes file was made and used to generate an internet view to indicate modifications from sanity.io, an headless cms, again in 2016,” Astorino instructed BleepingComputer.
“By no means touched it since then, as I used to be centered on the brand new model of the extension. The one dangerous factor was the outdated (and solely) @sanity dependency which has been compromised. However i didn’t comprehend it.”

